The instigator of impersonating exchange customer service fraud
 In recent years, among crimes related to virtual currency, fraud has gradually entered a "development period" and has become the fastest growing type of crime.
In recent years, among crimes related to virtual currency, fraud has gradually entered a "development period" and has become the fastest growing type of crime.
Fraudsters "advance with the times" have played with the blockchain one after another, fully combining their past fraud experience in the telecommunications fraud industry, extending their claws into the currency circle, and making a lot of money.
In fact, deception is still old wine in new bottles, or those old routines. Since the concept of virtual currency is relatively new, there is insufficient anti-fraud publicity for this type of fraud at this stage, and the public is relatively low vigilance against such fraud, which leads to the frequent success of fraudsters.
image description
image description
image description
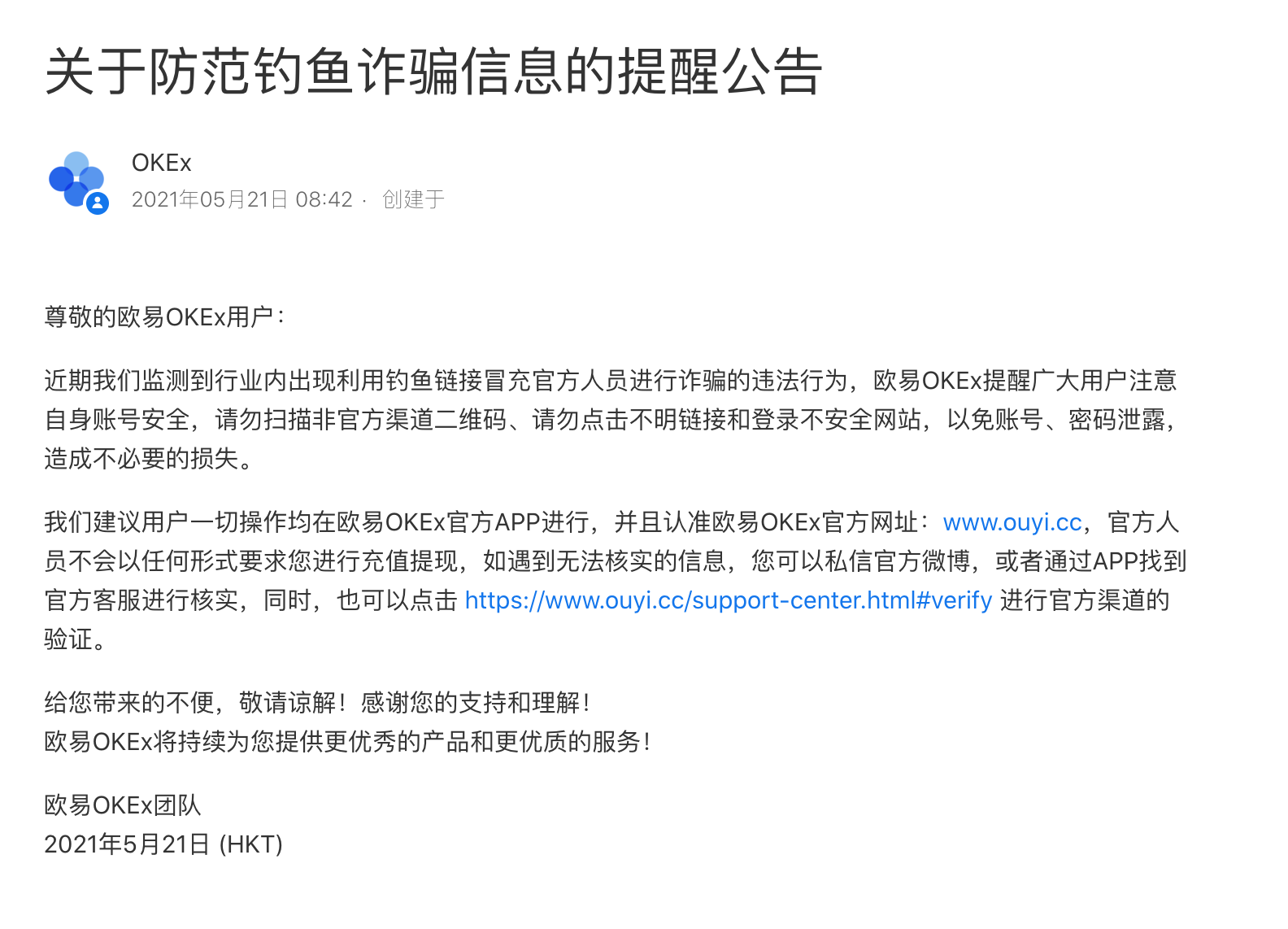
Announcement released by OKEX
Zhifan security team believes that crimes related to virtual currency include:Illegal crimes that use blockchain virtual currency as a gimmick, illegal crimes that use virtual currency as a trading medium, and illegal crimes that illegally obtain virtual currency through fraud or technical means。
The recent high-frequency scams posing as customer service of virtual currency exchanges belong to the last type.It is to directly steal the victim's virtual currency through fraudCompared with technical means such as ransomware, hacker attacks, and malware, this kind of impersonating customer service fraud has lower crime costs, and is more implementable and reproducible.
At the same time, since the scammers obtained the victim's private data (identity information, exchange account information, exchange transaction records, etc.)short and fastFraud
Fraud
image description
first step
first stepsecond step
second stepthird step
third stepthe fourth step
the fourth stepthe fifth step
the fifth step: In order to help you fall into the trap faster and complete the coin transfer operation in the email, you are required to download a niche video conferencing software and enable the screen sharing function. Human environment, do not contact anyone.
Step 6: In the state of screen sharing, the scammer threatens and brainwashes you, and teaches you to complete the currency transfer operation, and you are finally cheated (there is also a scammer who sends a fake exchange phishing website to defraud the exchange account information and mobile phone verification code first. , and then directly steal your coins).
I have to admit that the fraud gang is quite "professional", and the supporting equipment is very complete:
· Scammers use accurate user information to make victims trust. User information includes name, phone number, email, account ID, account opening time, and transaction records are very accurate. This information can dispel the victim's suspicion and give the victim a "sense of trust".
· Capturing the victim’s fears and reducing judgment. Using participation in money laundering to carry out psychological attacks, while posing as the electronic seal of law enforcement agencies in the mail, makes the victim nervous. Judgment is impaired in stressful situations.
· A full set of fakes and real ones, increasing trust again. The scammers use professional customer service skills, video authentication, work uniforms, badges, background walls, telephone transfers, and recording prompts.
· Professional criminal tools, let your guard down. Scammers use professional criminal tools, fake exchange ticketing systems, email verification codes.
Seeing this, everyone should understand that this is actuallyPretending to be customer service fraud and impersonating public security fraud, is still a familiar taste, a familiar formula, which is to call your name first, gain your trust by describing your personal information, threaten you with the name of your involvement in money laundering, and brainwash you while you are at a loss Money transferred.
Why does this old-fashioned routine work so well? Why do criminal gangs turn to the currency circle to cheat?
Zhifan Technology security experts believe that there are the following reasons:
1. Relatively speaking, people in the currency circle are more wealthy,Scammers can get more money in a limited time。
2. The anti-fraud publicity for virtual currency is relatively weak. Some investors in the currency circle are older, middle-aged and elderly, and their security awareness in this regard is relatively low.
3、Relevant departments of the state continue to increase efforts to combat cybercrime, with the "Card Breaking Action" and "Anti-Money Laundering Law" and a series of combined punches taking effect, traditional money laundering channels have been hit hard, and criminal gangs directly choose to cheat virtual currency.
4、Since virtual currency trading platforms are not protected by national laws, and the standards for determining the value of virtual currency are somewhat controversial, many criminals seize the loopholes, Using the above methods to carry out telecom fraud against Chinese users, it is difficult for the victims to report and file a case, which leads to the increasingly rampant criminals.
In-depth analysis
In-depth analysis
image description
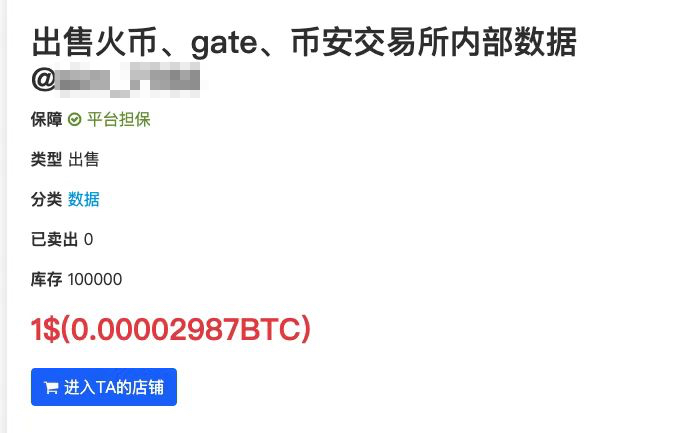
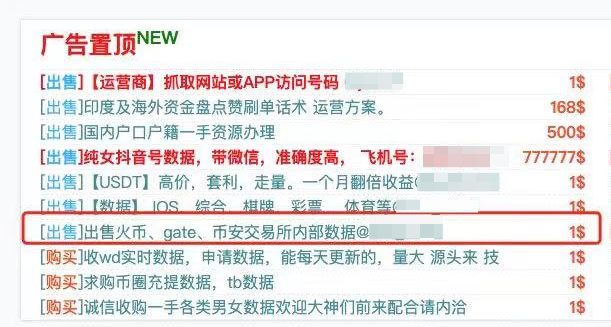
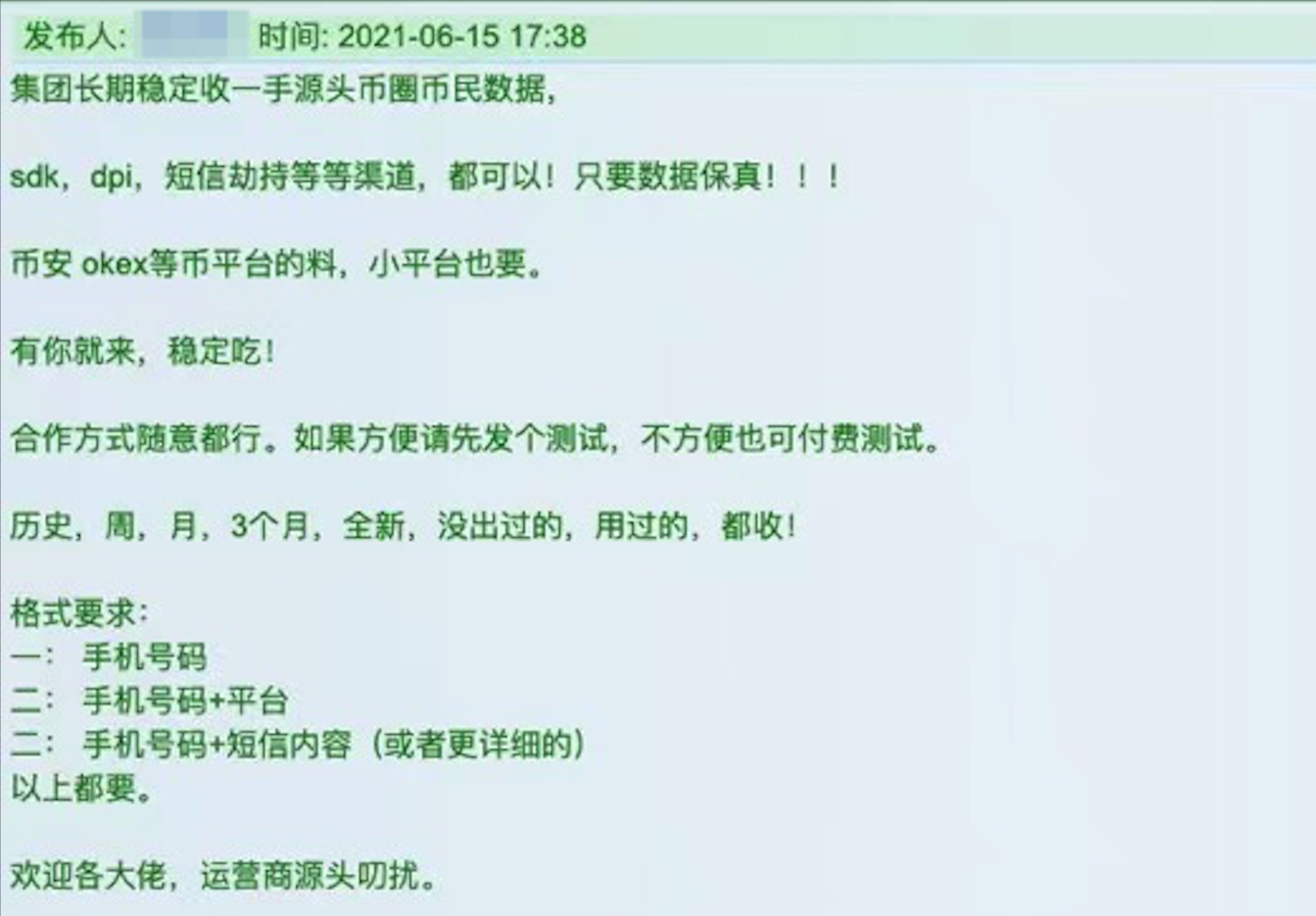
Dark web sells private exchange data
When it comes to the dark web, let’s briefly introduce the following nouns:
surface net: It is on the surface of the Internet and can be accessed and browsed through standard search engines.
deep web: The content in it is not accessible and browseable through regular search engines.
dark web: Refers to websites that have not been indexed and can only be accessed through specialized web browsers. Traditional browsers cannot directly access them. They are generally considered to be a subset of the "deep web".
Tor(the onion router): Onion Browser, which can block the user's IP address and allow anonymous browsing.
Telegram: It is a cross-platform instant messaging software with functions such as "destroy after reading", "delayed destruction", and "simultaneous deletion" of unilateral messages.
Then you need to go through Tor to access the dark web. In the world of the dark web, there are illegal transactions such as arms, drugs, and pornography everywhere.The act of buying and selling private data on the dark web provides assistance to downstream crimes and breeds cybercrime。
After research, the Zhifan security team found that the operation mode of the industrial chain is as follows:
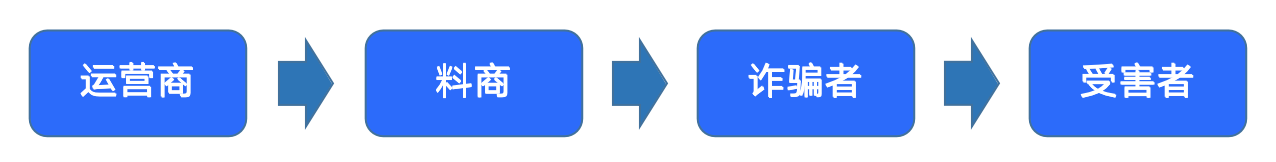
operator: A third-party organization that has direct access to exchange user transaction data. Judging from the acquisition information on the dark web, a certain team specializes in acquiring transaction data from various exchanges in the hands of operators and other institutions or individuals. The source data is mainly obtained through channels such as SDK, DPI, and SMS hijacking.
material supplierscammer
scammersafety reminder
safety reminder
Zhifan security experts remind users to raise security awareness and be vigilant at all times. Don’t trust strange phone calls and text messages, don’t click on strange links and emails to avoid being phished, and don’t trust strangers on the phone. All materials can be forged.
When you encounter problems, you must operate with caution and seek professional help. Please keep in mind:So-called security accounts and write-off accounts are all scams, The exchange also clearly stated that it will not call users. When in doubt, you can also contact us at any time to help identify.
Chase Trace-Virtual Currency Tracking and Verification PlatformChase Trace-Virtual Currency Tracking and Verification Platform", in order to assist the police in the analysis of related cases, and comprehensively improve the combat effectiveness.
Up to now, it has assisted the police in investigating more than 300 cases involving virtual currency, and the total amount of cases solved has exceeded 100 billion yuan, and has been commended and thanked by the public security department for many times。
Zhifan Technology can assist the police to track and analyze the virtual currency lost in such fraud cases. If the public security organs need assistance in related cases, they can directly reply and contact us.
In addition, users who have encountered such scams can also reply to us, we can help analyze, and at the same time synchronize relevant information to the corresponding public relations agency.



