OKX Web3 & WTF Academy: You are working hard to make money one second, but your home is "stolen" by hackers the next?
Introduction: OKX Web3 Wallet has specially planned the "Security Special Issue" column to provide special answers to different types of on-chain security issues. Through the most real cases happening around users, in collaboration with experts or institutions in the security field, dual sharing and answers from different perspectives are conducted, so as to sort out and summarize the rules of safe transactions from the shallow to the deep, aiming to strengthen user security education while helping users learn to protect their private keys and wallet asset security from themselves.
The hair-pulling operation is as fierce as a tiger, but the safety factor is negative 5?
As a high-frequency user of on-chain interactions, safety always comes first for the furry people.
Today, the "pit avoidance kings" on the two major chains will teach you how to conduct security protection strategies
This issue is the 3rd security special issue. We have invited industry-renowned security experts 0x AA and the OKX Web3 wallet security team to explain the common security risks and prevention measures of "Mao Ren" from the perspective of practical guidelines.
WTF Academy: Thank you very much for the invitation from OKX Web3. I am 0x AA from WTF Academy. WTF Academy is a Web3 open source university that helps developers get started with Web3 development. This year, we incubated a Web3 rescue project, RescuETH (on-chain rescue team), which focuses on rescuing the remaining assets in users' stolen wallets. So far, we have successfully rescued more than 3 million RMB worth of stolen assets on Ethereum, Solana, and Cosmos.
OKX Web3 Wallet Security Team: Hello everyone, I am very happy to share this. The OKX Web3 Wallet Security Team is mainly responsible for the construction of various security capabilities of OKX in the Web3 field, such as wallet security capabilities, smart contract security audits, on-chain project security monitoring, etc., providing users with multiple protection services such as product security, fund security, and transaction security, and contributing to maintaining the entire blockchain security ecosystem.
Q1: Please share some real-life examples of risks encountered by people who pet fur.
WTF Academy: Private key leakage is one of the major security risks faced by Coinbase users. In essence, a private key is a string of characters used to control crypto assets, and anyone who possesses a private key can fully control the corresponding crypto assets. Once a private key is leaked, an attacker can access, transfer, and manage the user's assets without authorization, causing the user to suffer financial losses. Therefore, I will focus on sharing several cases of private key theft.
Alice (pseudonym) was induced by hackers to download malware on social media, and her private key was stolen after running the malware. Currently, malware comes in various forms, including but not limited to: mining scripts, games, conference software, bot scripts, clamp robots, etc. Users need to raise their security awareness.
After Bob (pseudonym) accidentally uploaded his private key to GitHub, it was obtained by others, resulting in the theft of assets.
When Carl (pseudonym) was consulting a question in the project's official Tegegram group, he trusted the fake customer service who contacted him and leaked his mnemonic phrase, and his wallet assets were subsequently stolen.
OKX Web3 Wallet Security Team: There are many risk cases of this type. We have selected several classic cases that users encountered when they were making money.
The first type is fake airdrops released by high-imitation accounts. When user A was browsing the Twitter of a popular project, he found an announcement of an airdrop activity under the latest Twitter, and then clicked on the announcement link to participate in the airdrop, which eventually led to phishing. Currently, many phishers use high-imitation official accounts and post false announcements under official Twitter to lure users into the trap. Users should be careful to distinguish and not take it lightly.
The second type is the hijacking of the official account. The official Twitter and Discord accounts of a certain project were hacked, and then the hacker posted a fake airdrop activity link on the official account of the project. Since the link was released from the official channel, user B did not doubt its authenticity and clicked on the link to participate in the airdrop, but was phished.
The third type is encountering malicious project parties. When user C participated in a mining activity of a certain project, in order to obtain higher rewards, he invested all his USDT assets in the staking contract of the project. However, the smart contract was not strictly audited and was not open source. As a result, the project party stole all the assets deposited by user C in the contract through the backdoor reserved in the contract.
For LuMao users, who may have dozens or hundreds of wallets, how to protect the security of wallets and assets is a very important topic. They need to be vigilant at all times and improve their safety awareness.
Q2: As a high-frequency user, what are the common security risks and protective measures for LuMao people in on-chain interactions?
WTF Academy: For Web3 users and even all Web3 users, the two most common security risks are phishing attacks and private key leaks.
The first type is phishing attacks: hackers usually impersonate official websites or applications, trick users into clicking on social media and search engines, and then induce users to trade or sign on phishing websites, thereby obtaining token authorization and stealing user assets.
Preventive measures: First, it is recommended that users only access official websites and applications from official channels (such as links in official Twitter profiles). Second, users can use security plug-ins to automatically block some phishing websites. Third, when users access suspicious websites, they can consult professional security personnel to help determine whether they are phishing websites.
The second type is private key leakage: This has been introduced in the previous question and will not be expanded here.
Preventive measures: First, if the user has a wallet installed on their computer or mobile phone, try not to download suspicious software from unofficial channels. Second, users need to know that official customer service usually will not take the initiative to send you private messages, let alone ask you to send or enter private keys and mnemonics on fake websites. Third, if the user's open source project requires the use of private keys, please configure the .gitignore file first to ensure that the private key is not uploaded to GitHub.
OKX Web3 Wallet Security Team: We have summarized 5 common security risks that users encounter in on-chain interactions and listed some protective measures for each risk.
1. Airdrop Scam
Risk profile: Some users often find a large number of unknown tokens in their wallet addresses. These tokens usually fail to trade on commonly used DEXs. The page will prompt users to exchange them on its official website. Then, when users authorize transactions, they often grant smart contracts the authority to transfer account assets, which eventually leads to asset theft. For example, in the Zape airdrop scam, many users suddenly received a large number of Zape coins in their wallets, which seemed to be worth hundreds of thousands of dollars. This made many people mistakenly believe that they had accidentally made a fortune. However, this is actually a carefully designed trap. Since these tokens cannot be queried on regular platforms, many users who are eager to cash out will find the so-called "official website" based on the token name. After connecting the wallet as prompted, they thought they could sell these tokens, but once authorized, all assets in the wallet would be stolen immediately.
Protective measures: Avoiding airdrop scams requires users to be highly vigilant, verify the source of information, and always obtain airdrop information from official channels (such as the project's official website, official social media accounts, and official announcements). Protect private keys and mnemonics, do not pay any fees, and use communities and tools for verification to identify potential scams.
2. Malicious Smart Contracts
Risk Profile: Many unaudited or non-open-source smart contracts may contain vulnerabilities or backdoors and cannot guarantee the safety of user funds.
Protective measures: Users should try to interact only with smart contracts that have been strictly audited by formal audit companies, or pay attention to checking the security audit report of the project. In addition, projects that usually have bug bounties are more secure.
3. Authorization management:
Risk Profile: Over-authorization of interactive contracts may lead to theft of funds. Here are some examples: 1) The contract is an upgradeable contract. If the private key of a privileged account is leaked, an attacker can use the private key to upgrade the contract to a malicious version, thereby stealing the assets of authorized users. 2) If there are unidentified vulnerabilities in the contract, over-authorization may allow attackers to exploit these vulnerabilities in the future to steal funds.
Protective measures: In principle, only necessary authorizations are granted to interactive contracts, and unnecessary authorizations need to be checked and revoked regularly. When signing off-chain permit authorizations, be sure to clearly understand the target contract/asset type/authorization amount, and think twice before acting.
4. Fishing Authorization
Risk Profile: Clicking on a malicious link and being induced to authorize a malicious contract or user
Protective measures: 1) Avoid blind signing: Before signing any transaction, make sure you understand the content of the transaction to be signed and ensure that each step is clear and necessary. 2) Be cautious with the authorization target: If the authorization target is an EOA address (Externally Owned Account) or an unverified contract, you must be vigilant. Unverified contracts may contain malicious code. 3) Use anti-phishing plug-in wallets: Use plug-in wallets with anti-phishing protection, such as OKX Web3 wallet, which can help identify and block malicious links. 4) Protect mnemonics and private keys: All websites that require mnemonics or private keys are phishing links. Do not enter these sensitive information on any website or application.
5. Malicious Scripts
Risk profile: Running malicious scripts can cause Trojans to be implanted in your computer, leading to the theft of your private keys.
Protective measures: Be cautious when running unknown plucking scripts or plucking software.
In short, we hope that users can be cautious and protect the security of their wallets and assets when interacting on the chain.
Q3: Let’s sort out the classic fishing types and techniques, and how to identify and avoid them?
WTF Academy: I would like to answer this question from another perspective: Once a user discovers that their assets have been stolen, how can they tell whether it is a phishing attack or a private key leak? Users can usually distinguish between the following two types of attack characteristics:
1. Characteristics of phishing attacks: Hackers usually obtain authorization for one or more assets in a user's single wallet through phishing websites, thereby stealing assets. Generally speaking, the types of stolen assets are equal to the number of times the user authorized on the phishing website.
2. Characteristics of private key/mnemonic phrase leakage: Hackers completely gain control of all assets in all chains under a single or multiple wallets of the user. Therefore, if one or more of the following characteristics appear, it is highly likely that the private key has been leaked:
1) The native token is stolen (such as ETH of the ETH chain) because the native token cannot be authorized.
2) Multi-chain assets were stolen.
3) Multiple wallet assets were stolen.
4) Multiple assets from a single wallet are stolen, and the person clearly remembers not authorizing these assets.
5) There is no authorization before or in the same transaction to steal tokens (Approval event).
6) The transferred Gas will be immediately transferred away by the hacker.
If it does not meet the above characteristics, it is likely a phishing attack.
OKX Web3 Wallet Security Team: To avoid being phished, you need to pay attention to two points: 1) Remember not to fill in the mnemonic/private key on any web page; 2)
Make sure the link you visit is the official link, and be careful when clicking the confirmation button on the wallet interface.
Next, we share some classic fishing scenarios to help users understand more intuitively.
1. Phishing by fake websites: Impersonating official DApp websites to trick users into entering private keys or mnemonics. Therefore, the first principle for users is not to provide their wallet private keys or mnemonics to anyone or any website. Secondly, check whether the URL is correct, try to use official bookmarks to access commonly used DApps and use regular mainstream wallets, such as OKX Web3 wallet, which will warn of detected phishing websites.
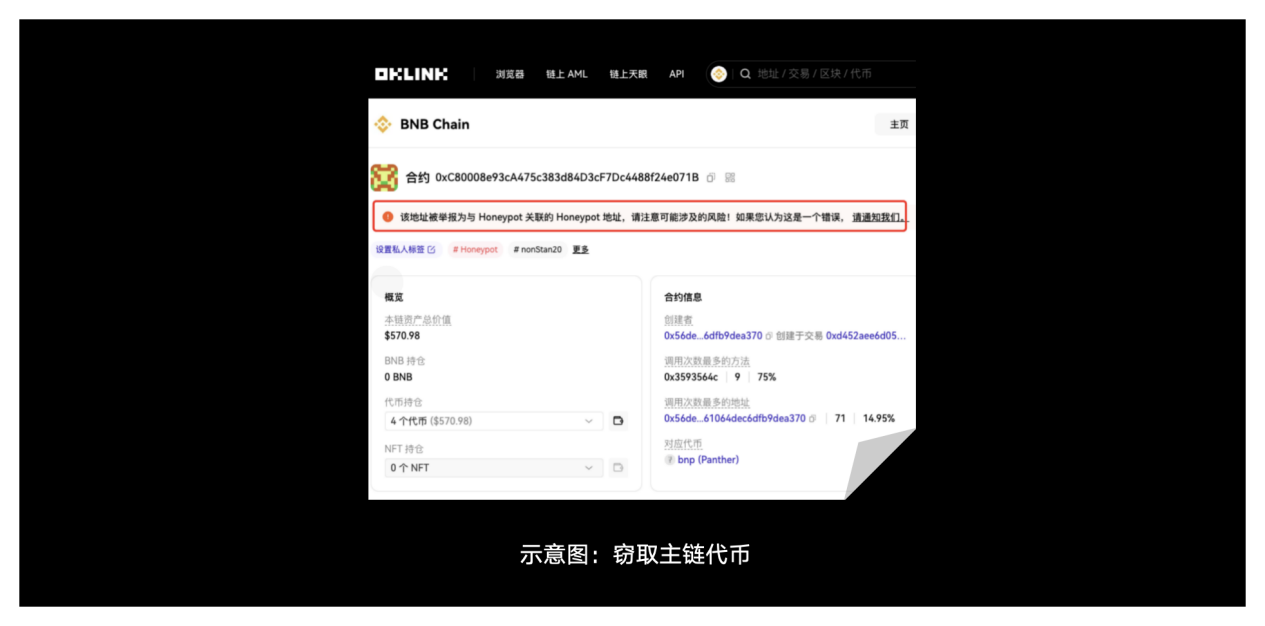
2. Stealing main chain tokens: Malicious contract functions are named Claim, SeurityUpdate, AirDrop, etc., which are misleading names. The actual function logic is empty and only the user's main chain tokens are transferred.
3. Transfers to similar addresses: Scammers will generate addresses that have the same first and last digits as a user's associated address through address collision, use transferFrom to transfer a zero amount to poison the user, or use fake USDT to transfer a certain amount, etc., to pollute the user's transaction history, hoping that the user will copy the wrong address from the transaction history for subsequent transfers.
4. Fake customer service: Hackers impersonate customer service and contact users through social media or emails, asking for private keys or mnemonics. Official customer service will not ask for private keys and will simply ignore such requests.
Q4: What safety precautions should professional hair removers pay attention to when using various tools?
WTF Academy: Since there are many types of tools involved in porn, users should strengthen safety precautions when using various tools, such as
1. Wallet security: Ensure that private keys or mnemonics are not leaked, do not save private keys in unsafe places, and avoid entering private keys on unknown or untrusted websites, etc. Users should store private keys or mnemonics backups in a safe place, such as offline storage devices or encrypted cloud storage. In addition, for wallet users with high-value assets, using a multi-signature wallet can increase security.
2. Prevent phishing attacks: When users visit any related websites, please be sure to carefully check the URL and avoid clicking on links from unknown sources. Try to obtain download links and information from the project's official website or official social media, and avoid using third-party sources.
3. Software security: Users should ensure that antivirus software is installed and updated on their devices to prevent malware and virus attacks. In addition, wallets and other blockchain-related tools should be updated regularly to ensure the latest security patches are used. Since many fingerprint browsers and remote desktops have previously had security vulnerabilities, they are not recommended.
Through the above measures, users can further reduce security risks when using various tools.
OKX Web3 Wallet Security Team: Let us first give an example from a public industry case.
For example, BitFingerprint Browser provides functions such as multi-account login, preventing window association, and simulating independent computer information, which is favored by some users, but a series of security incidents in August 2023 exposed its potential risks. Specifically, the "plug-in data synchronization" function of BitBrowser allows users to upload plug-in data to the cloud server and quickly migrate by entering a password on the new device. Although this function was originally designed to facilitate users, it also has security risks. Hackers obtained users' wallet data by invading the server. Through brute force cracking, hackers cracked the user's wallet password from the data and obtained wallet permissions. According to server records, the server storing the extension cache was illegally downloaded in early August (log records were recorded as late as August 2). This incident reminds us that while enjoying convenience, we must also be vigilant about potential security risks.
Therefore, it is crucial for users to ensure that the tools they use are safe and reliable to avoid the risk of hacker attacks and data leaks. Generally speaking, users can improve certain security from the following dimensions.
1. Use of hardware wallet: 1) Update the firmware regularly and purchase through official channels. 2) Use on a secure computer and avoid connecting in public places.
2. Use of browser plug-ins: 1) Use third-party plug-ins and tools with caution, and try to choose reputable products, such as OKX Web3 wallet, etc. 2) Avoid using wallet plug-ins on untrusted websites.
3. Use of transaction analysis tools: 1) Use a trusted platform for transactions and contract interactions. 2) Carefully check the contract address and calling method to avoid misoperation.
IV. Use of computer equipment: 1) Regularly update computer equipment systems, update software, and patch security holes. 2) Use security anti-virus software to regularly check and kill computer system viruses.
Q 5: Compared with a single wallet, how can people manage multiple wallets and accounts more securely?
WTF Academy: Since LUMAO users interact frequently on the chain and manage multiple wallets and accounts at the same time, special attention needs to be paid to asset security.
1. Use a hardware wallet: Hardware wallets allow users to manage multiple wallet accounts on the same device. The private key of each account is stored in the hardware device, which is relatively more secure.
2. Separation security strategy & separation operating environment: The first is the separation security strategy. Users can achieve the purpose of risk diversification by separating wallets for different purposes. For example, airdrop wallets, transaction wallets, storage wallets, etc. For another example, hot wallets are used for daily transactions and cashing operations, and cold wallets are used for long-term storage of important assets. In this way, even if one wallet is damaged, other wallets will not be affected.
The second is to separate the operating environment. Users can use different devices (such as mobile phones, tablets, computers, etc.) to manage different wallets to prevent the security issues of one device from affecting all wallets.
3. Password management: Users should set a strong password for each wallet account and avoid using the same or similar passwords. Or use a password manager to manage passwords for different accounts to ensure that each password is independent and secure.
OKX Web3 Wallet Security Team: For crypto users, it is not easy to manage multiple wallets and accounts more securely. For example, the wallet security factor can be improved from the following dimensions:
1. Diversify risks: 1) Do not put all assets in one wallet, store them in a decentralized manner to reduce risks. Choose different types of wallets, such as hardware wallets, software wallets, cold wallets, and hot wallets, according to the type and purpose of assets. 2) Use multi-signature wallets to manage large assets and improve security.
2. Backup and recovery: 1) Back up your mnemonics and private keys regularly and store them in multiple safe locations. 2) Use a hardware wallet for cold storage to avoid private key leaks.
3. Avoid duplicate passwords: Set strong passwords for each wallet and account, and avoid using the same password to reduce the risk of one account being hacked and other accounts being threatened at the same time.
4. Enable two-step verification: Where possible, enable two-step verification (2FA) for all accounts to increase account security.
5. Automated tools: Reduce the use of automated tools, especially those services that may store your information in the cloud or on third-party servers to reduce the risk of data leakage.
6. Limit access rights: Only authorize trusted people to access your wallet and account, and limit their operating permissions.
7. Check the security status of your wallet regularly: Use tools to monitor wallet transactions to ensure that no abnormal transactions occur. If you find that the private key of a wallet has been leaked, immediately replace all wallets, etc.
In addition to the dimensions listed above, there are many more. In any case, users should try to ensure the security of their wallets and assets through multiple dimensions as much as possible, and not rely solely on a single dimension.
Q 6: What are the protection suggestions for transaction slippage, MEV attacks, etc. that are specifically related to the profiteers?
WTF Academy: It is crucial to understand and prevent transaction slippage and MEV attacks, as these risks directly affect transaction costs and asset security.
Take MEV attacks as an example. Common types include: 1) Front-running, where miners or trading robots preemptively execute the same transaction before the user's transaction to make a profit. 2) Sandwich attack, where miners insert buy orders and sell orders before and after the user's transaction to profit from price fluctuations. 3) Arbitrage: arbitrage using price differences in different markets on the blockchain.
Users can avoid public broadcasting on the blockchain by submitting transactions to the miners' dedicated channels through the MEV protection tool. Or they can reduce the risk of being attacked by reducing the transaction disclosure time, that is, reducing the time the transaction stays in the memory pool, using higher gas fees to speed up transaction confirmation, and avoiding large transactions concentrated on one DEX platform.
OKX Web3 Wallet Security Team: Transaction slippage refers to the difference between the expected transaction price and the actual execution price, which usually occurs when the market is volatile or liquidity is low. MEV attacks refer to attackers taking advantage of information asymmetry and trading privileges to obtain excess profits. The following are some common protective measures for these two scenarios:
1. Set slippage tolerance: Due to the delay in transactions going online, as well as possible MEV attacks, users need to set a reasonable slippage tolerance in advance when trading to avoid transaction failures or capital losses due to market fluctuations or MEV attacks.
2. Trading in batches: Avoid large transactions at one time and trade in batches to reduce the impact on market prices and reduce the risk of slippage.
3. Use trading pairs with higher liquidity: When trading, choose trading pairs with sufficient liquidity to reduce the occurrence of slippage.
4. Use anti-frontrunning tools: Try not to use Memepool for important transactions. You can use professional anti-frontrunning tools to protect transactions from being captured by MEV robots.
Q 7: Can users use monitoring tools or professional methods to regularly monitor and detect wallet account anomalies?
WTF Academy: Users can use a variety of monitoring tools and professional methods to regularly monitor and detect abnormal activities in wallet accounts. These methods help improve the security of accounts and prevent unauthorized access and potential fraud. The following are some effective monitoring and detection methods:
1) Third-party monitoring services: Many platforms currently provide users with detailed reports and real-time alerts on wallet activities.
2) Use security plug-ins: Some security tools can automatically block some phishing websites.
3) Wallet built-in functions: Wallets such as OKX Web3 can automatically detect and identify some phishing websites and suspicious contracts, and provide warnings to users.
OKX Web3 Wallet Security Team: Currently, many companies or organizations provide a large number of tools for monitoring and detecting wallet addresses. We have compiled some of them based on public industry information, such as:
1. Blockchain monitoring tools: Use blockchain analysis tools to monitor abnormal transactions of wallet addresses, changes in funds, set address transaction notifications, etc.
2. Secure wallet: Use professional wallets such as OKX Web3 wallet, which can support transaction pre-execution and detect suspicious transactions in a timely manner; it can also detect and prevent interactions with malicious websites and contracts in a timely manner.
3. Alert Systems: can send reminders of transactions or balance changes based on user-set conditions, including SMS, email, or App notifications.
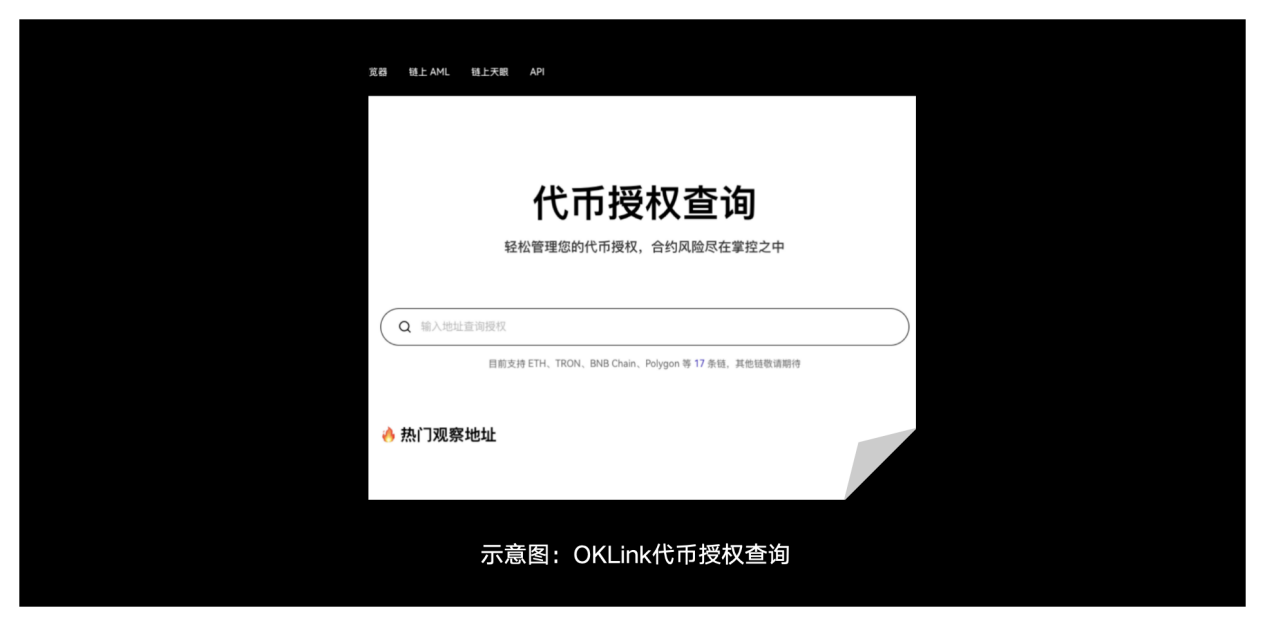
4. OKLink token authorization query: Check the wallet’s authorization for DApps, revoke unnecessary authorizations in a timely manner, and prevent authorizations from being abused by malicious contracts.
Q 8: How to protect privacy and security on the chain?
WTF Academy: Although the open and transparent nature of blockchain brings many benefits, it also means that users' transaction activities and asset information may be abused, and on-chain privacy protection becomes increasingly important. However, users can protect their personal identity privacy by creating and using multiple addresses. Fingerprint browsers are not recommended because many security vulnerabilities have occurred in the past.
OKX Web3 Wallet Security Team: Currently, more and more users are beginning to pay attention to privacy and security protection. Common methods include:
1. Multi-wallet management: Disperse user assets and reduce the risk of a single wallet being tracked or attacked.
2. Use a multi-signature wallet: Multiple signatures are required to execute transactions, which increases security and privacy protection.
3. Cold wallet: Store long-term assets in hardware wallets or offline storage to prevent online attacks.
4. Do not disclose your address: Avoid sharing your wallet address on social media or public platforms to prevent being tracked by others.
5. Use a temporary email address: When participating in airdrops or other activities, use a temporary email address to protect your personal information from being exposed.
Q9: If a wallet account is stolen, how should the user respond? Are there any efforts or mechanisms to help stolen users recover their assets and protect their assets?
WTF Academy: We focus on phishing attacks and private key/mnemonic phrase leaks separately.
First, when a phishing attack occurs, the assets authorized by the user to the hacker will be transferred to the hacker's wallet, which is almost impossible to rescue/recover; but the remaining assets in the user's wallet are relatively safe. The RescuETH team recommends that users take the following measures:
1) Withdraw the asset authorization given to the hacker
2) Contact security companies to track the stolen assets and hacker addresses.
Secondly, when a private key/mnemonic phrase leak occurs, all valuable assets in the user's wallet will be transferred to the hacker's wallet, which is almost impossible to rescue/recover. However, assets in the user's wallet that cannot be transferred can be rescued, such as unlocked pledged assets and unissued airdrops, which are also our main rescue targets. The RescuETH team recommends that users take the following measures:
1) Check your wallet immediately to see if there are any assets that have not been transferred by hackers. If there are any, transfer them to a safe wallet immediately. Sometimes hackers will miss some assets on unpopular chains.
2) If your wallet has unlocked pledged assets and unissued airdrops, you can contact a professional team for rescue.
3) If you suspect that malware has been installed, perform a virus scan on your computer as soon as possible to remove the malware. If necessary, you can reinstall the system.
Currently, we have made many attempts to rescue stolen users' assets.
First, we are the first team to conduct large-scale rescue of stolen wallet assets. In the Arbitrum airdrop event in March 2023, I collected more than 40 private keys of leaked wallets from nearly 20 fans and competed with hackers for the $ARB airdrop. In the end, we successfully rescued ARB tokens worth more than $40,000, with a success rate of 80%.
Second, when a user's wallet is stolen, assets with economic value will be transferred away by hackers, while NFTs or ENS that have no economic value but are of commemorative value to the user will remain in the wallet. However, since the wallet is monitored by hackers, the transferred Gas will be transferred away immediately, and users cannot transfer these assets. In response to this, we have made a self-help rescue application: RescuETH App, which is based on the MEV technology of Flashbots bundle. It can package transactions for transferring in Gas and transferring out NFT/ENS, preventing hackers from monitoring scripts to transfer out Gas, thereby successfully rescuing assets. Currently, RescuETH App is in internal testing and is expected to start public testing in June.
Third, for the part of the assets that can be rescued in the stolen wallets of users (unlocked pledges and unissued airdrops), we provide paid and customizable white hat rescue services. At present, our white hat team consists of nearly 20 security/MEV experts, and has rescued more than 3 million RMB in assets from stolen wallets of ETH, Solana, Cosmos and other chains.
OKX Web3 Wallet Security Team: We will discuss this from two perspectives: user measures and OKX Web3 Wallet security mechanism
1. User Measures
Once a user finds that their wallet has been stolen, it is recommended to take the following measures urgently:
1. Emergency response measures
1) Transfer funds immediately: If there are funds in your wallet, you need to transfer them to a secure new address immediately.
2) Revoke authorization: Immediately revoke all authorizations through management tools to prevent further losses.
3) Track the flow of funds: Track the flow of stolen funds in a timely manner and organize detailed information about the theft process in order to seek external help.
2. Community and project support
1) Seek help from the project and community: Report the incident to the project and community, and sometimes the project can freeze or recover the stolen assets. For example, USDC has a blacklist mechanism that can block fund transfers.
2) Join blockchain security organizations: Join relevant blockchain security organizations or groups and use collective strength to solve problems.
3) Contact the wallet customer support: Contact the wallet’s customer support team in a timely manner to seek professional help and guidance.
2. OKX Web3 Wallet Security Mechanism
OKX Web3 Wallet attaches great importance to the security of user assets and continues to invest in protecting user assets, providing multiple security mechanisms to ensure the security of users' digital assets.
1) Black address tag library: OKX Web3 wallet has established a rich black address tag library to prevent users from interacting with known malicious addresses. The tag library is continuously updated to respond to changing security threats and ensure the security of user assets.
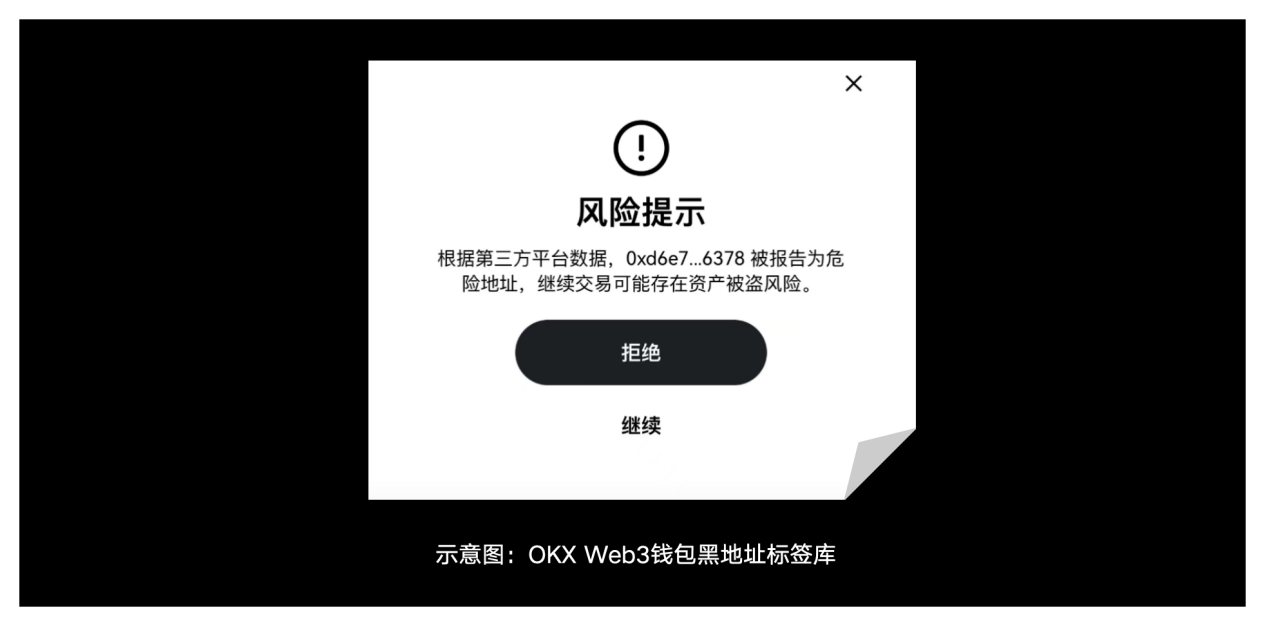
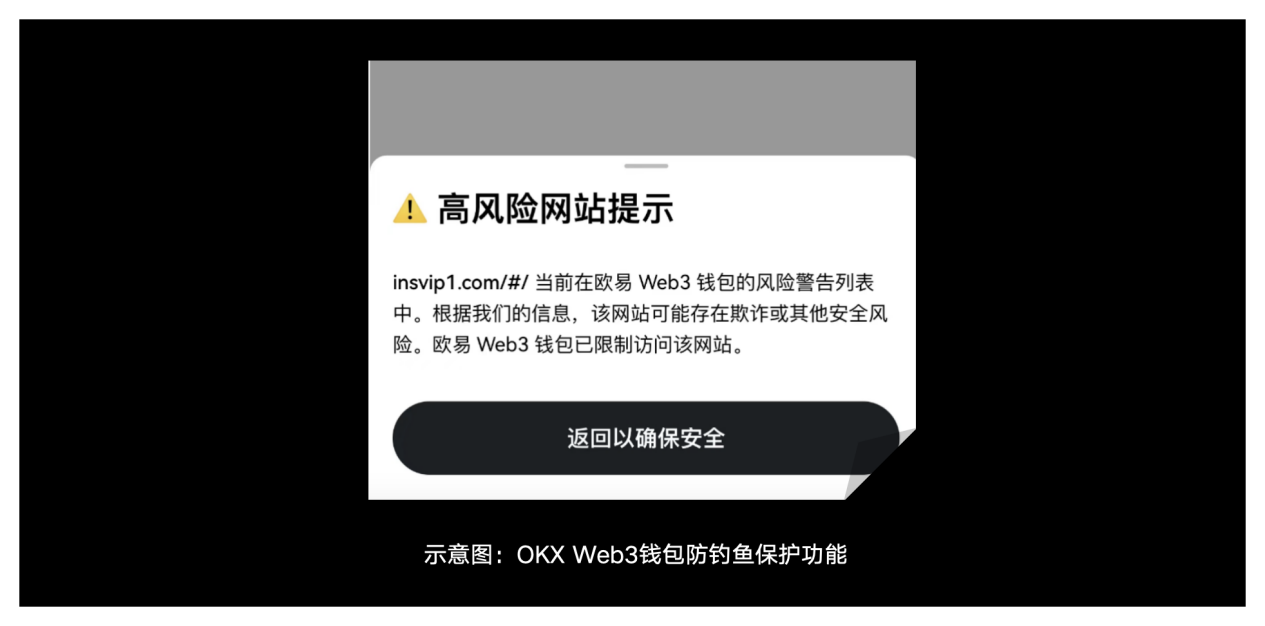
2) Security plug-in: OKX Web3 wallet provides built-in anti-phishing protection to help users identify and block potential malicious links and transaction requests, enhancing the security of user accounts.
3) 24-hour online support: OKX Web3 Wallet provides customers with 24-hour online support, promptly following up on incidents of customer asset theft and fraud, and ensuring that users can quickly get help and guidance.
4) User Education: OKX Web3 Wallet regularly publishes security tips and educational materials to help users improve their security awareness and understand how to prevent common security risks and protect their assets.
Q10: Can you share some cutting-edge security technologies, such as whether AI can be used to enhance security protection?
WTF Academy: Security in the blockchain and Web3 fields is an evolving field, with various cutting-edge security technologies and methods emerging. The most popular ones are:
1) Smart Contract Auditing: Using AI and machine learning to automate the security auditing of smart contracts can detect vulnerabilities and potential risks in smart contracts, providing faster and more comprehensive analysis than traditional manual auditing.
2) Abnormal behavior detection: Use machine learning algorithms to analyze on-chain transactions and behavior patterns to detect abnormal activities and potential security threats. AI can identify common attack patterns (such as MEV attacks, phishing attacks) and abnormal transaction behaviors, and provide real-time warnings.
3) Fraud Detection: AI can analyze transaction history and user behavior to identify and flag possible fraudulent activities.
OKX Web3 Wallet Security Team: Currently, AI has been widely used in the Web3 field. Here are some scenarios where AI is used to increase Web3 security protection:
First, anomaly detection and intrusion detection: Use AI and machine learning models to analyze user behavior patterns and detect abnormal activities. For example, deep learning models can be used to analyze transaction behavior and wallet activities to identify potential malicious behavior or abnormal activities.
Second, phishing website identification: AI can detect and block phishing websites by analyzing web page content and link features, protecting users from the threat of phishing attacks.
Third, malware detection: AI can detect new and unknown malware by analyzing the behavior and characteristics of files, preventing users from downloading and executing malicious programs.
Fourth, automated threat response: AI can automate response measures, such as automatically freezing accounts or taking other protective actions after detecting abnormal activity.
Finally, thank you for reading the 03rd issue of the OKX Web3 Wallet "Security Special Issue". We are currently preparing for the 04th issue, which will include real cases, risk identification, and security operation tips. Stay tuned!
Disclaimer
This article is for reference only and is not intended to provide (i) investment advice or investment recommendations; (ii) an offer or solicitation to buy, sell or hold digital assets; or (iii) financial, accounting, legal or tax advice. Holding digital assets (including stablecoins and NFTs) involves high risks and may fluctuate significantly or even become worthless. You should carefully consider whether trading or holding digital assets is suitable for you based on your financial situation. Please be responsible for understanding and complying with local applicable laws and regulations.