OKX Web3:链上防钓鱼安全交易指南
Entering a new cycle, on-chain interaction risks are increasingly exposed as user activity increases. Phishers usually use methods such as fake wallet websites, stealing social media accounts, creating malicious browser plug-ins, sending phishing emails and information, and publishing fake applications to induce users to leak sensitive information, leading to asset losses. Phishing forms and scenarios are diverse. characteristics such as sex, complexity and anonymity.
For example, phishers generally create fake websites that look similar to legitimate wallet websites to trick users into entering their private keys or mnemonic phrases. These fake websites are usually promoted using social media, emails, or advertisements to mislead users into thinking they are Access regular wallet services to steal users’ assets. In addition, phishers may use social media platforms, forums or instant messaging applications to pretend to be wallet customer service or community administrators and send false messages to users, asking them to provide wallet information or private keys. This method takes advantage of users. Trust in officials, inducing them to reveal private information, etc.
Taken together, these cases highlight the threat phishing poses to Web3 wallet users. In order to help users improve their security awareness when using Web3 wallets and protect their assets from loss,OKX Web3 conducted in-depth community research and collected phishing incidents encountered by many Web3 wallet users, thereby extracting the four typical phishing scenarios that users most often encounter, and used a combination of graphic and text cases through subdivided cases in different scenarios. , has written the latest guide on how Web3 users should conduct safe transactions for your reference.
Malicious information sources
1. Twitter replies to popular projects
Reply via Popular Projects Twitter YesOne of the main ways of malicious information,The phishing Twitter account can be exactly the same as the official account in terms of logo, name, certification mark, etc., and even the number of followers can be dozens of K, and the only thing that can distinguish the two is——Twitter handle (note similar characters), please keep your eyes open.
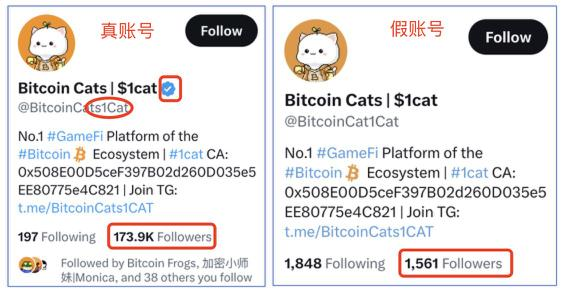
In addition, many times, fake accounts will deliberately reply to official tweets, but the replies contain phishing links, which can easily make users think they are official links and be deceived. Currently, some official accounts will add End of Tweet tweets to remind users to guard against the risk of possible phishing links in subsequent replies.
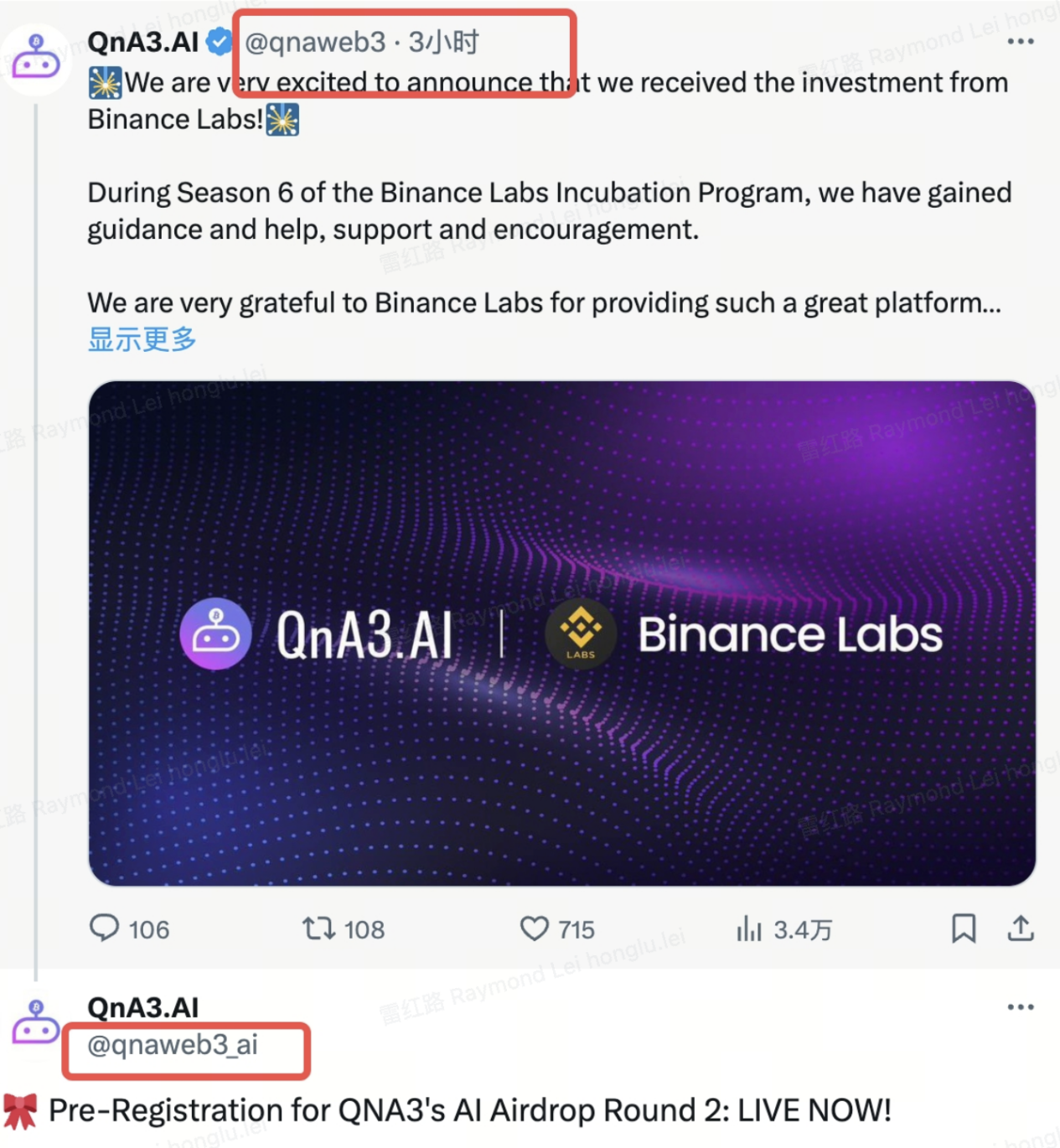
2. Steal official Twitter/Discord
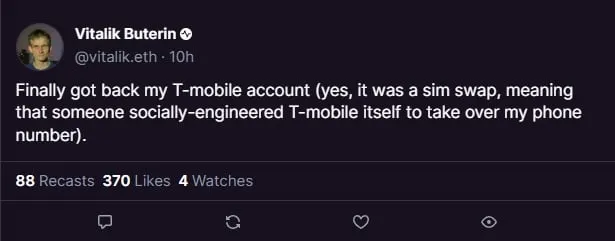
In order to increase credibility, phishers will also steal the official Twitter/Discord of the project party or KOL and publish phishing links in the official name, so many users are easily fooled. For example, Vitaliks Twitter account and the TON projects official Twitter account were stolen, and phishers took the opportunity to publish false information or phishing links.
3. Google search ads
Phishers sometimes use Google search ads to post malicious links. The name displayed by the users browser appears to be an official domain name, but the link that jumps to after clicking is a phishing link.
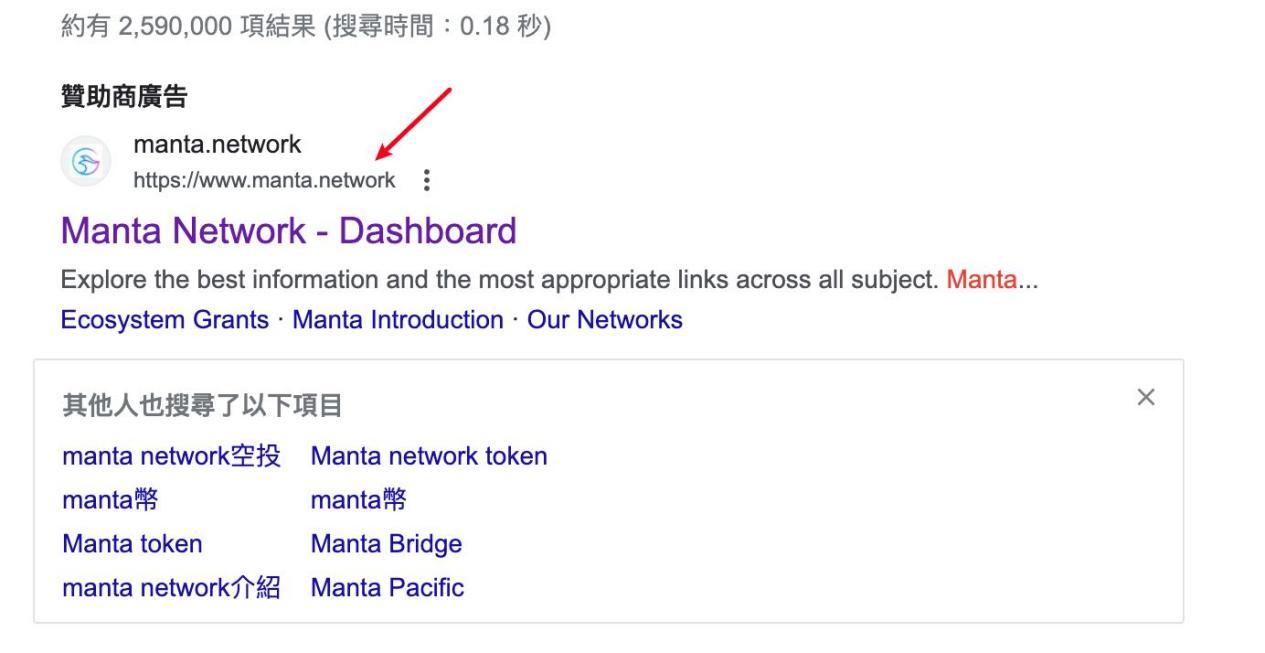
4. Fake applications
Anglers will also passFake apps to lure users. For example, when a user downloadsInstalling a fake wallet posted by phishers can lead to leakage of private keys and loss of assets. Some phishers have modified the Telegram installation package, thereby changing the on-chain addresses for receiving and sending tokens, resulting in the loss of user assets.
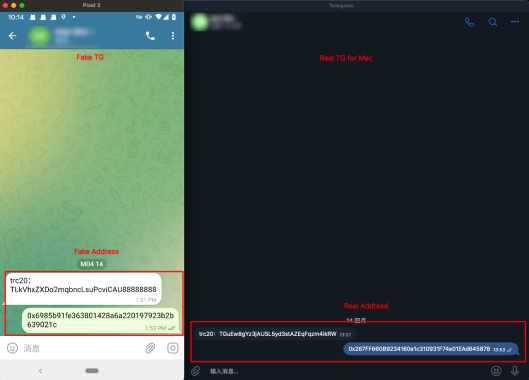
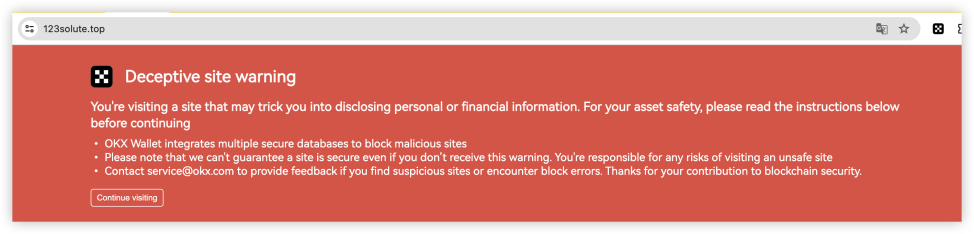
5. Countermeasures: OKX Web3 wallet supports phishing link detection and risk reminders
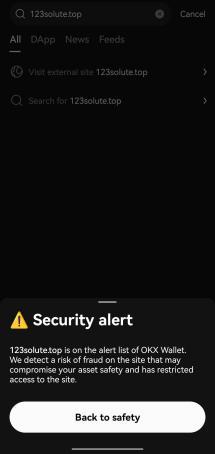
Currently, OKX Web3 wallet supports phishing link detection and risk reminders to help users better deal with the above problems. For example, when users use a browser to access a website through the OKX Web3 plug-in wallet, if the domain name is a known malicious domain name, they will receive an alert as soon as possible. In addition, if the user uses the OKX Web3 APP to access a third-party DAPP on the Discover interface, the OKX Web3 wallet will automatically perform risk detection on the domain name. If it is a malicious domain name, an interception reminder will be issued and the user will be prohibited from accessing.
Wallet private key security
1. Conduct project interaction or qualification verification
Phishers will disguise themselves as plug-in wallet pop-up pages or any other web pages when users are interacting with projects or verifying qualifications, asking users to fill in mnemonic phrases/private keys. These types of websites are generally malicious, and users should improve their Be vigilant.
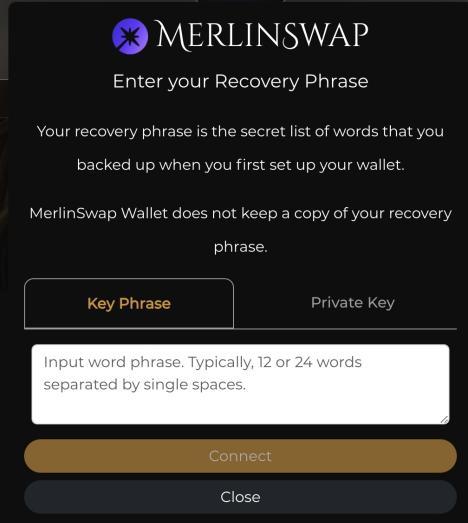
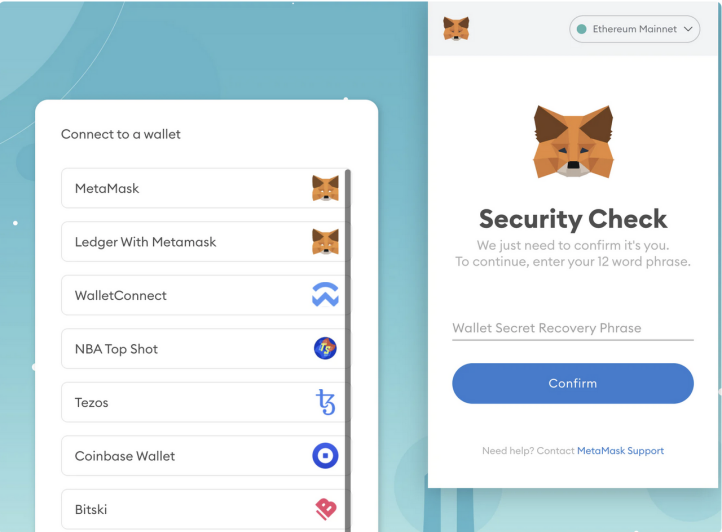
2. Impersonating project party customer service or administrator
Phishers often pretend to be project customer service or Discord administrators and provide URLs for users to enter mnemonic phrases or private keys. In this case, the other party is a phisher.

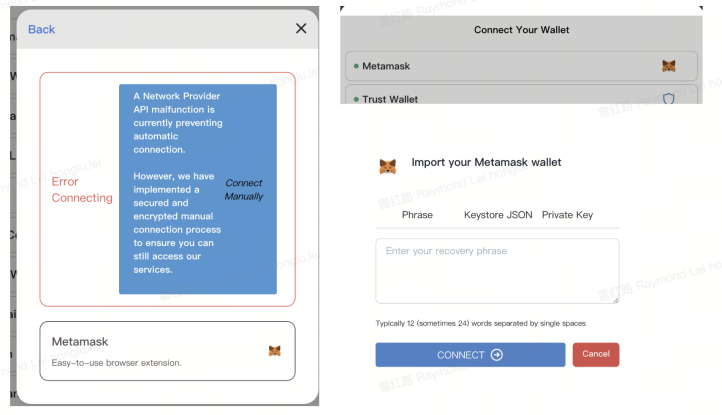
3. Other possible paths for leakage of mnemonic phrases/private keys
userThere are many possible ways for mnemonic words and private keys to be leaked.Common ones include computers being implanted with Trojan virus software, computers using fingerprint browsers for hair-raising, computers using remote control or proxy tools, mnemonic words/private keys taking screenshots to save photo albums, but being uploaded and backed up to the cloud by malicious APPs. , but the cloud platform was invaded, the process of entering the mnemonic phrase/private key was monitored, people around you physically obtained the mnemonic phrase private key file/paper, and developers pushed the code including the private key to Github, etc.
In short, users need to store and use mnemonic words/private keys safely to better ensure the security of wallet assets. For example, as a decentralized self-hosted wallet, OKX Web3 wallet is now available in iCloud/Google Drive cloud, manual, hardware and other mnemonic/private key backup methods. It has grown into the most comprehensive private key backup method on the market. Wallet provides users with a more secure way to store private keys. Regarding the problem of user private keys being stolen, OKX Web3 wallet has supported relatively comprehensive mainstream hardware wallet functions such as Ledger, Keystone, and Onekey. The private keys of the hardware wallet are stored in the hardware wallet device and are controlled by the user themselves, thereby ensuring asset security. That is to say, OKX Web3 wallet allows users to safely manage assets through hardware wallets, and at the same time, they can freely participate in on-chain token transactions, NFT markets, and various dApp project interactions. In addition, OKX Web3 wallet has now launched MPC private keyless wallet and AA smart contract wallet to help users further simplify private key issues.
4 classic fishing scenes
Scenario 1. Stealing main chain tokens
Phishers often name malicious contract functions with misleading names such as Claim and SeurityUpdate, while the actual function logic is empty, thereby only transferring the users main chain tokens. Currently, the OKX Web3 wallet has launched a transaction pre-execution function, which displays the asset and authorization changes after the transaction is uploaded to the chain, thereby further reminding users to pay attention to security. In addition, if its interactive contract or authorized address is a known malicious address, a red security reminder will be issued.
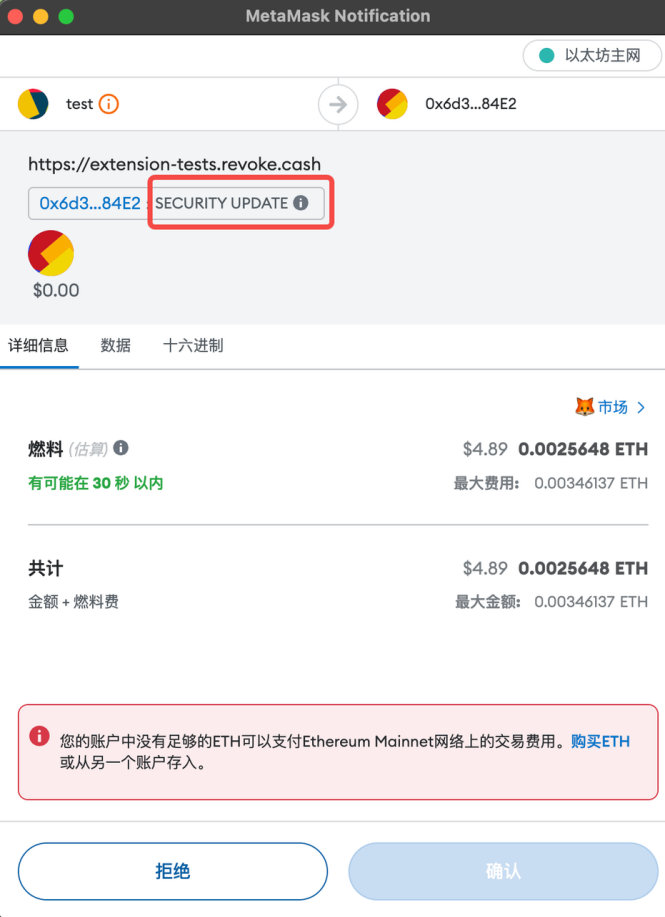
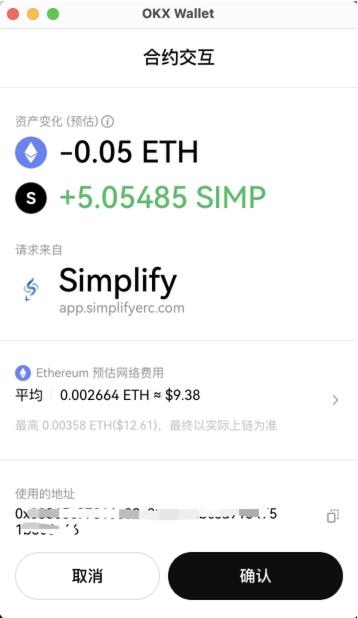
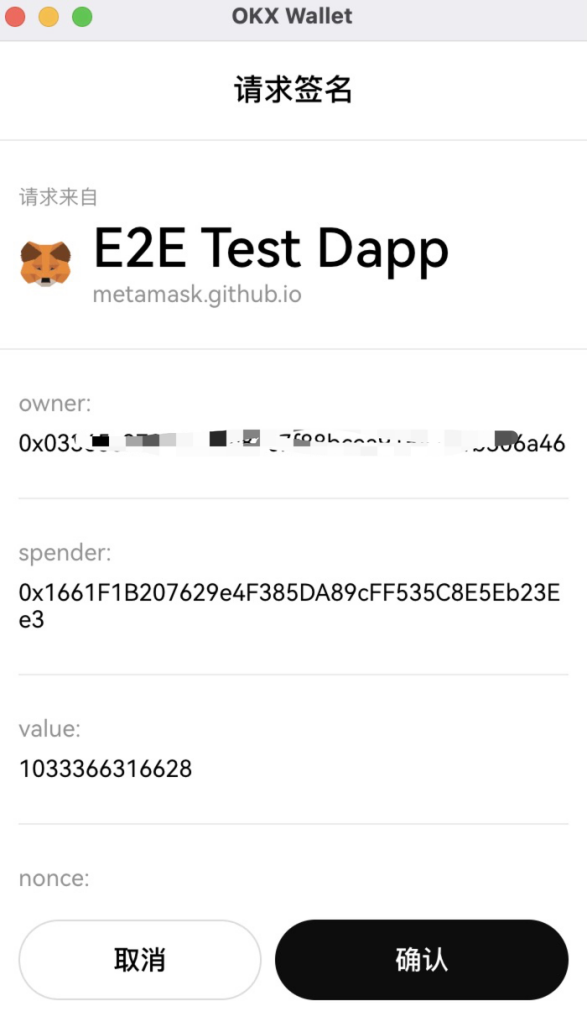
Scenario 2. Transfer with similar address
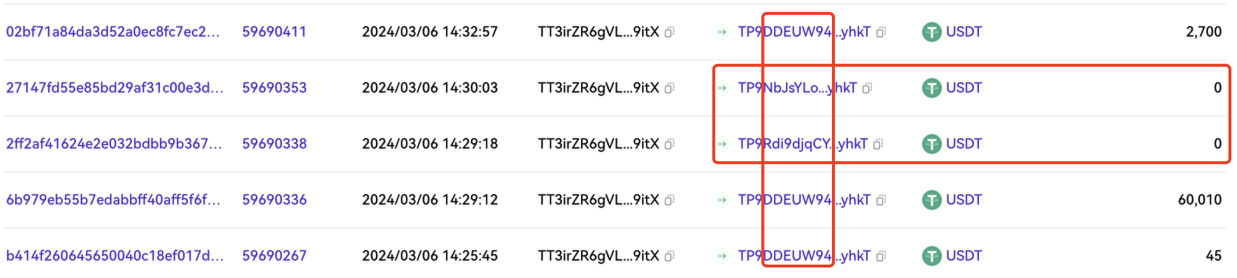
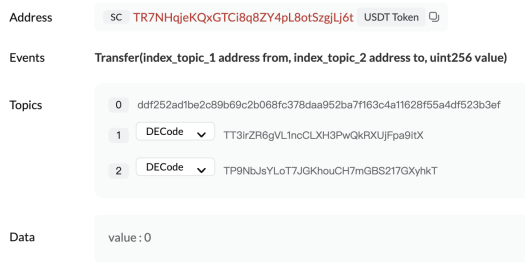
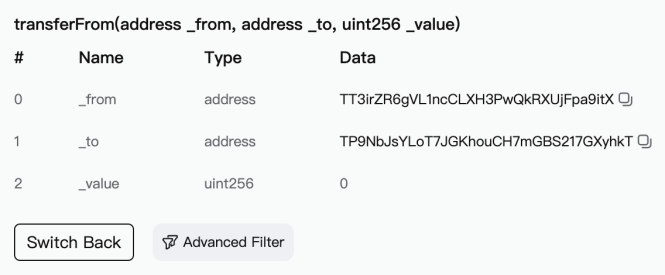
When a large-amount transfer is detected, the phisher will generate an address with the same first few digits as the receiving address through address collision, use transferFrom to transfer an amount of 0, or use fake USDT to transfer a certain amount, contaminating the users transaction history and expecting the user to follow up. The transfer copies the wrong address from the transaction history to complete the fraud.
https://www.oklink.com/cn/trx/address/TT3irZR6gVL1ncCLXH3PwQkRXUjFpa9itX/token-transfer
https://tronscan.org/#/transaction/27147fd55e85bd29af31c00e3d878bc727194a377bec98313a79c8ef42462e5f
Scenario 3. On-chain authorization
Phishers usually induce users to sign approve/increaseAllowance/decreaseAllowance/setApprovalForAll transactions, and upgrade using Create 2 to generate a pre-calculated new address, bypassing security detection, thereby defrauding user authorization. OKX Web3 Wallet will issue security reminders for authorized transactions. Users are advised to note that this transaction is an authorization-related transaction and be aware of the risks. In addition, if the transaction authorization address is a known malicious address, a red message will be displayed to prevent users from being deceived.
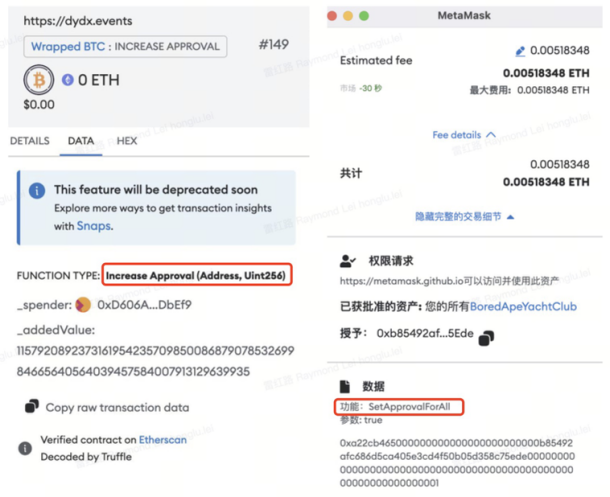
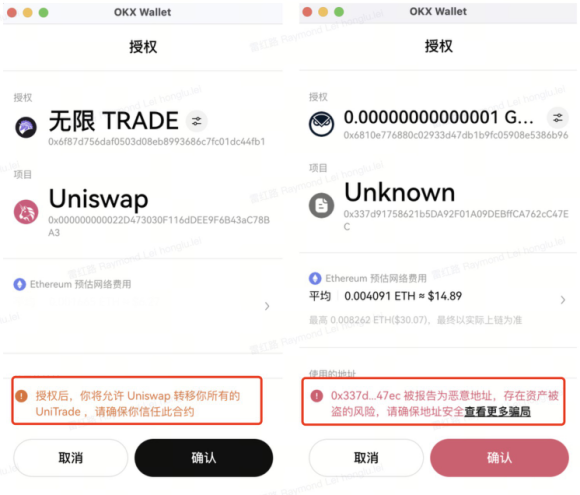
Scenario 4. Off-chain signature
In addition to on-chain authorization, phishers will also engage in phishing by inducing users to sign off-chain. For example, ERC 20 token authorization allows users to authorize a certain amount to another address or contract. The authorized address can transfer user assets through transferFrom. Phishers use this feature to commit fraud. The OKX Web3 wallet is currently developing a risk warning function for such scenarios. When a user signs an offline signature, by parsing the signature authorization address, if a known malicious address is hit, a risk warning will be given to the user.
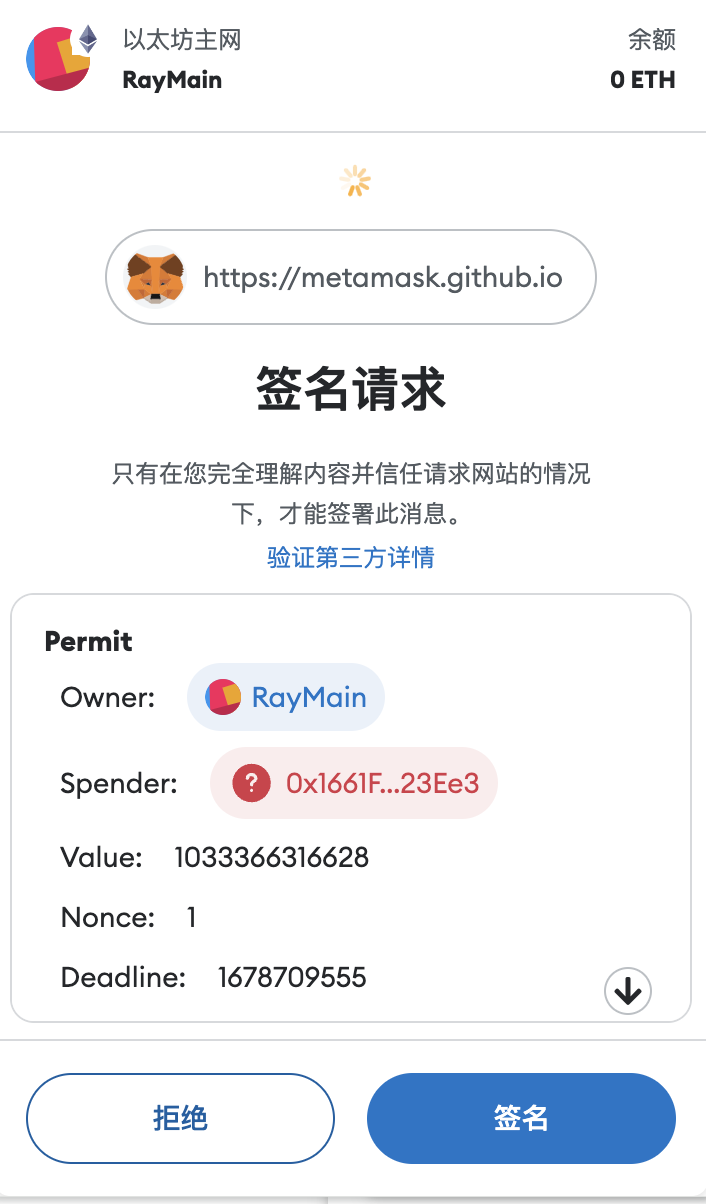
Other fishing scenes
Scenario 5. TRON account permissions
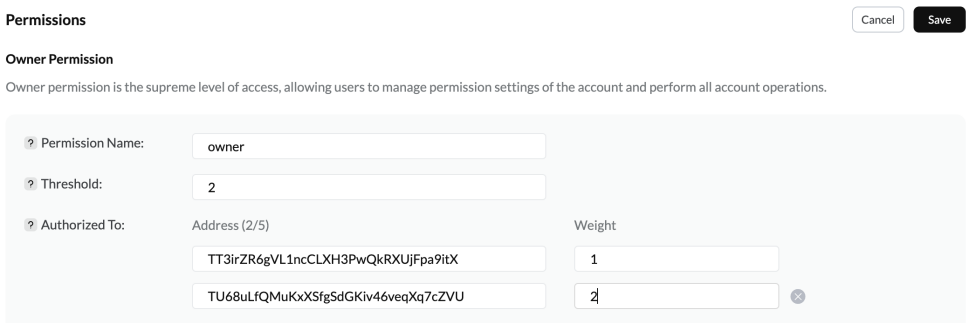
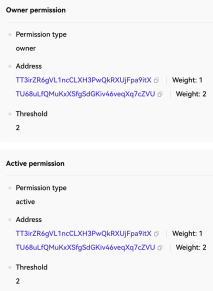
This type of scenario is relatively abstract. Usually, phishers obtain users byTRON account permissions to control its assets. TRON account permission settings are similar to EOS, divided into Owner and Active permissions, and can be set up in a similar multi-signature form for permission control. The following permissions set the Owner threshold to 2, the weights of the two addresses are 1 and 2 respectively, and the first address is the user The address has a weight of 1 and the account cannot be operated alone.
https://tronscan.org/#/wallet/permissions
https://www.oklink.com/trx/tx/1fe56345873425cf93e6d9a1f0bf2b91846d30ca7a93080a2ad69de77de5e45f
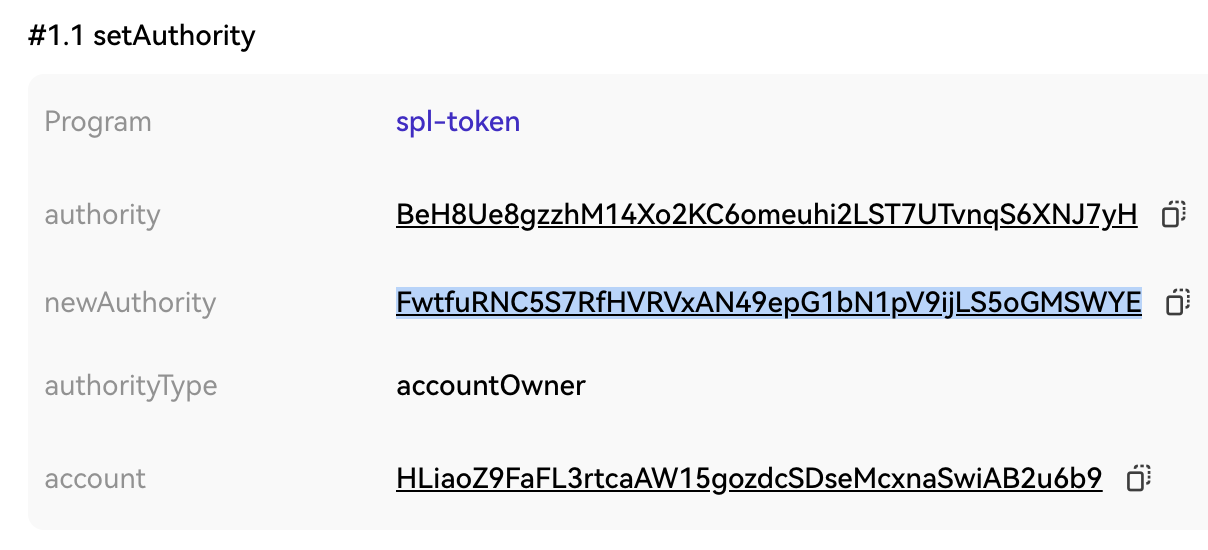
Scenario 6. Solana tokens and account permissions
The phisher modifies the token ATA account Ownership through SetAuthroity, which is equivalent to transferring the token to the new Owner address. After the user is phished by this method, the assets are transferred to the phishing party and so on. In addition, if the user signs the Assign transaction, the Owner of his normal account will be modified from System Program to a malicious contract.
Scenario 7. EigenLayer calls queueWithdrawal
Due to issues such as the design mechanism of the protocol itself, it is also easily exploited by phishers. The queueWithdrawal call of EigenLayer, a middleware protocol based on Ethereum, allows specifying other addresses as withdrawers, and the user was phished into signing the transaction. After seven days, the specified address obtains the users pledged assets through completeQueuedWithdrawal.
Explore the world on the chain, safety first
Safe use of Web3 wallets is a key measure to protect assets, and users should take practical precautions to guard against potential risks and threats. You can choose the industry-renowned and security-audited OKX Web3 wallet to explore the world on the chain more safely and conveniently.
As the most advanced and comprehensive wallet in the industry, OKX Web3 wallet is completely decentralized and self-hosted, allowing users to play with on-chain applications in one stop. It now supports 85+ public chains, and the three terminals of App, plug-in and web page are unified. , covering 5 major sectors including wallet, DEX, DeFi, NFT market, and DApp exploration, and supports Ordinals market, MPC and AA smart contract wallets, gas exchange, connection to hardware wallets, etc. In addition, users can increase the security of their wallets by securely protecting private keys and mnemonic phrases, regularly updating wallet apps and operating systems, handling links and information with care, and enabling multi-factor authentication features.
In short, in the on-chain world, asset security is more important than anything else.
Users need to remember these 3 Web3 security rules: do not fill in mnemonic words/private keys on any web page, be careful when clicking the confirmation button on the wallet transaction interface, and links obtained from Twitter/Discord/search engines may be phishing links.