Cobo Security Team: A Guide to Secure Blockchain Transactions
Original author: Cobo Global
The Cobo security team compiled common risk points in the transaction process on the chain and compiled transaction security execution guidelines, aiming to allow users to avoid risks during the transaction process, ensure the safety of funds, and prevent phishing attacks.
Preface
With the passage of the Bitcoin ETF, the blockchain market is starting to pick up. The recovery in currency prices has allowed the industry to gradually return to its former prosperity. At the same time, hacker activities also became active. The Cobo security team has observed an increase in the frequency of phishing cases in the past month or two.
Recently, new application hotspots such as Restaking and BTC L2 have begun to emerge. On-chain transactions have gradually become an indispensable part of Web3 users daily lives, and more and more user funds are being transferred to the chain.
Unlike centralized applications such as exchanges, the account security of on-chain applications needs to be ensured by the users themselves. Conducting blockchain transactions securely is the most basic capability of Web3 natives. Although many infrastructures such as browser plug-in wallets and even the browser itself have certain risk warnings against phishing, incidents of users losing assets due to unsafe transactions still occur from time to time (such as private key leaks, signature phishing, etc.).
The Cobo security team compiled common risk points in the transaction process on the chain and compiled transaction security execution guidelines, aiming to allow users to avoid risks during the transaction process, ensure the safety of funds, and prevent phishing attacks.
Before starting the introduction, the Cobo security team summarizes the core principles of safe transactions for everyone, as follows:
1. Refuse to sign blindly, and do not sign transactions or messages that you do not understand;
2. Take the trouble to verify repeatedly.
How to trade safely
A complete DApp transaction process contains multiple links:Wallet installation, access to DApp, wallet connection, message signature, transaction signature, and post-transaction processing.There are certain safety risks in each link. The following will introduce the precautions in actual operation.
Note: This article mainly introduces the secure interaction process on Ethereum and various EVM-compatible chains. The tools and specific technical details used by other non-EVM chains may be different.
Wallet installation
The current mainstream use of DApps is to use browser plug-in wallets to interact. The mainstream wallets used by the EVM chain include Metamask and Rabby.
After in-depth experience, the Cobo security team recommends using the Rabby plug-in wallet as the main on-chain interactive wallet based on risk warnings. The reason is that compared to the Metamask wallet, the Rabby wallet provides functions such as transaction data analysis, transaction simulation execution, transaction risk warning, authorization query, and historical signature data query. It has greater advantages than the Metamask wallet in phishing prevention.
To install the Chrome plug-in wallet, you need to confirm that it is downloaded and installed from the Chrome App Store. Do not install the wallet from a third-party website to avoid installing wallet software with backdoors.
Qualified users are recommended to use hardware wallets in conjunction with each other, which can greatly improve overall security in private key storage.
Visit DApp
Web phishing is a common attack method in Web3 attacks. A typical case is to induce users to access phishing DApp applications in the name of airdrops. After users connect to their wallets, they are induced to sign token authorization, transfer transactions or token authorization signatures, resulting in losses to user assets.
Therefore, users need to remain vigilant when accessing DApps to avoid entering the trap of web phishing.
You should confirm the correctness of the DApp URL before accessing the DApp. suggestion:
Try not to access directly from the first Google search keyword. Phishing attackers can buy advertising space to put their phishing website search rankings at the top, so the first one is not necessarily the official website.
Avoid directly clicking on x.com and URLs published in comments and messages of other users in various social software. Such URLs are likely to be phishing links.
Repeatedly confirm the correctness of the DApp URL before accessing it. It can be verified based on DApp markets such as DefiLlama, the official X account of the project party, and Google search results.
Websites that are confirmed to be safe have been added to the browsers favorites, and can be accessed directly from the favorites later.
After you have opened the DApp web page, you also need to perform a security check on the address bar:
Check the domain name and URL.Usually DApps use relatively concise domain names and URLs. Such as https://app.uniswap.org/; if you encounter a particularly long domain name, it may be in the form of https://zk-polyhedra.network-8jb.xyz/ or a domain name similar to the name of a well-known website, such as https:// pufffer.fi (note the extra f), it is likely to be a phishing website and should be logged out immediately.When identifying domain names, special attention should be paid to 1 il, oO 0 and other similar characters.
Check the browser https link status.Currently, mainstream DApps all use https links, and the browser should display a 🔒-shaped sign. If it is not an https link or the browser prompts a certificate exception, the website you are visiting may not be an official website or may be subject to a hijacking attack, and you should stop accessing it immediately.
Currently, mainstream browser plug-in wallets on the market have integrated certain risk warning functions, such as Metamask/Phantom, etc. When accessing some risky URLs that are on the blacklist, the browser plug-in wallet or even the Chrome browser itself may display a strong security prompt (see picture below).
Connect wallet
After entering the DApp, the operation of connecting to the wallet may be triggered automatically or after actively clicking Connect. The plug-in wallet will perform some checks, information display, etc. on the current DApp.
The following is the web review information provided by Rabby Wallet, which can be used to assist in judging the authenticity of DApp.
After connecting to the wallet, usually the DApp will not actively activate the plug-in wallet when the user has no other operations. If after logging in to the website, the DApp frequently calls up the wallet to ask for signed messages and transactions, and even signatures continue to pop up after rejecting the signature, then it is likely to be a phishing website and needs to be handled with caution.
Message signature
In extreme cases, for example, an attacker attacks the official website of the protocol or replaces the page content through attacks such as front-end hijacking. It is difficult for ordinary users to screen the security of the website in this scenario.
At this time, the signature of the plug-in wallet is the final barrier for users to save their own assets. As long as malicious signatures are rejected, your own assets will be protected from loss.Users should carefully review the signature content when signing any messages and transactions and refuse blind signing.
Technically speaking, there are currently three common signature types in Ethereum:
Hash signature eth_sign:Sign the original hash of some data. The raw data for the hash could be a message or even an Ethereum transaction.
Message signature personal_sign:Signing data plain text is most common during user login verification or license agreement confirmation.
Structured data signature eth_signTypedData (EIP-712):For signatures of data objects used in DeFi protocols, common ones include ERC 20 Permit authorization signature, NFT pending order signature, etc.
For risk identification of message signatures, users can follow the following guidelines:
Natural language signatures usually pass.This type of signature is usually personal_sign, which is used to confirm login or confirm product instructions. It is a large natural language description (rather than numbers, hexadecimal, etc.). Because such messages include natural language, complex strings, and difficult smart contract processing, they are usually not used for on-chain authentication, but are used by websites to confirm address identity. So the relative risk is low.
It is forbidden to directly sign the original hexadecimal hash.This type of signature is usually an eth_sign signature. This type of signature is the most dangerous because the user cannot determine what the original data content of the hash is. Therefore most wallets have disabled the ability to sign raw hashes (hex data). Metamask wallet, you can confirm that its configuration is turned off in the Settings->Advanced->Eth_sign Request tab. Rabby wallet, related configurations are disabled by default, no additional configuration is required.
Structured data signatures scrutinize signature content.For example, if it is an ERC 20 Permit authorization signature, you need to check whether the spender address meets the expectations. If it is an EOA address, it is likely that you have clicked on a phishing signature and should be rejected immediately.
Regarding message signing, additional attention needs to be paid here. Although the eth_sign operation is prohibited by default in the browser plug-in wallet, the wallet can still sign hash class data through personal_sign. This type of signature does not result in a permit authorizing or initiating a transaction. However, individual protocols (such as some AA wallets) may still use personal_sign signatures for authentication. In principle, in order to avoid losses, hexadecimal data should not be signed. The effect of this type of signature is as follows:
transaction signature
Signature transactions must follow the principle of not signing blindly. Currently, many plug-in wallets will decode the message to be signed and display the relevant content. The following is an example of Rabby wallet parsing a DEX transaction:
Users can view some relevant information about the target address of the transaction, such asWhether it is an EOA address, address balance, contract deployment time, etc.Users can make risk judgments on transactions to be signed based on this information. For example, if the interactive address is an EOA address, or the interactive contract deployment time is less than 7 days, the operation can be considered to be risky and should be fully investigated before proceeding.
For open source protocols, mainstream browser plug-in wallets already support the analysis of transaction data. By viewing the transaction content after ABI decoding, you can have a clearer understanding of what operations are currently being performed. The function name called by the contract can provide some reference to its functions: such as approve, swap, transfer, deposit and withdraw, etc.
Rabby, the imToken wallet also integrates a simulated execution function. Users can directly see the transaction execution results before the transaction is confirmed. Through transaction simulated execution, users can view various fund transfers caused by the current transaction. Users should check carefully and reject signatures that do not meet expected execution results.
For users with certain technical reserves, if automated tools cannot successfully parse transactions, some common manual inspection methods can also be used:
By copying the interactive target contract address to a blockchain browser such as etherscan for review, the review mainly includes whether the contract is open source, whether there have been a large number of transactions recently, and whether Etherscan has labeled the address as official or malicious.
When encountering a transaction that cannot be recognized by the plug-in wallet, you can manually copy the first 8 digits in the original transaction data (raw_data, displayed through hexadecimal data) to https://openchain.xyz/signatures to query and get the original function. Name to roughly determine the behavior of the transaction.
Use trading simulation tools such as Phalcon, Tenderly and Dedaub to simulate execution and view the specific execution details of the transaction.
Post-trade processing
After evading phishing pages and malicious signatures, it does not mean that everything will be fine. Risk management still needs to be carried out after the transaction.
After the transaction, you should promptly check the on-chain status of the transaction to confirm whether it is consistent with the expected status when signing. If an abnormality is discovered, stop loss operations such as asset transfer and authorization cancellation can be carried out in a timely manner.
ERC 20 Approval authorization management is also very important. In some cases, after users authorized tokens for certain contracts, these contracts were attacked many years later. The attackers used the token authorization quota of the attacked contracts to steal user funds.
To avoid such situations, the Cobo security team recommends that users follow the following standards for risk prevention:
Minimize authorization.When authorizing tokens, a limited amount of corresponding tokens should be authorized based on the needs of the transaction. If a transaction requires authorization of 100 USDT, the authorization quantity will be limited to 100 USDT instead of using the default unlimited authorization.
Promptly revoke unnecessary token authorizations.Query the authorization status of the corresponding address through the Approval function of the Rabby wallet or log in to revoke.cash, and revoke the authorization of the protocol that has not been interacted with for a long time to prevent subsequent loopholes in the protocol from causing asset losses due to the use of the users authorization limit.
Other tips
In addition to the risks in the above-mentioned transaction process, some risks can also be avoided by rational use of the functions integrated in certain tools.
Some wallets have built-in wallet import functionality (such as Rabby). The risk of phishing can be mitigated by importing the addresses of other mobile wallets and performing mandatory secondary confirmation when making transactions (requiring waking up the wallet, scanning the code, and entering the password for confirmation). At the same time, you can enjoy the transaction security check of the mobile wallet (whitelist, simulated execution, phishing tips, etc.)
Some wallets support imported observer wallets (such as Rabby, OneKey, TokenPocket, imToken, etc.), and you can enter some unfamiliar websites through the observer wallet. The page for message signature or transaction initiation will still be normally evoked, and you can carefully view the content to be signed at this time. At the same time, because there is no private key, there is no need to worry about misoperation confirmation.
Check the authorization status of the address through the Approvals function of the Rabby wallet and revoke high-risk authorizations in a timely manner. Tips: Rabby uses multiple dimensions in this function (total amount of historical authorization links/number of 24-hour cancellations/authorization time/number of authorized assets) to evaluate authorization risks, which can more effectively help users identify authorization risks.
After signing by mistake, use the Signature Record function of the Rabby wallet to promptly check your signed transactions and text data to troubleshoot authorization risks in a timely manner.
With risk awareness and adequate risk prevention, effective capital isolation is still necessary to reduce the degree of capital damage in extreme circumstances. The Cobo security team recommends that you use the following solutions to store funds:
Use Gnosis Safe multi-signature wallet or cold wallet to store large funds;
Use the address generated by the browser wallet or other EOA wallets to store small funds for user interaction, and change the hot wallet address regularly.
If you accidentally get phished, you can immediately perform the following operations to reduce losses:
Revoke.cash promptly cancels authorization;
If the phishing permit message is signed and the funds are not transferred, immediately sign a new message and initiate a permit call to invalidate the phishing message nonce;
Transfer account funds when necessary.
How to safely receive airdrops
Issuing airdrops is currently a common method used by project parties to attract users, and it is also the hardest hit area for users to be attacked by phishing attacks. To this end, based on the above safe transaction guidelines, the Cobo security team has compiled a set of safe interaction processes for receiving on-chain airdrops:
First use the Rabby observer wallet to test the interaction process and confirm that there are no token authorization or token transfer transactions.
Permit message signatures are not performed during the process of receiving airdrops. No Approve contract call is made.
Try to use small account to receive airdrops.
Check the simulation execution results of the airdrop transaction to confirm that no tokens have been transferred out.
Plug-in tool selection
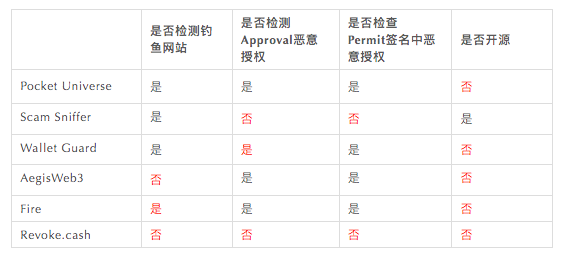
There is a lot of content in the blockchain security code, and it is possible that not every interaction can be carefully checked. So is there a useful browser plug-in to help us make risk judgments?
The Cobo security team has experienced the more mainstream transaction risk checking plug-ins on the market and learned fromPhishing webpage interception, Malicious authorized address check and Whether it is open sourceThe three dimensions are organized into tables, and you can choose to use them according to your own situation, as follows: