Đọc một bài báo để hiểu về học máy không kiến thức (ZKML): ZK và AI sẽ va chạm với loại tia lửa nào?
Biên dịch nguyên văn: Deep Tide TechFlow
Biên dịch nguyên văn: Deep Tide TechFlow
Zero-Knowledge Machine Learning (ZKML) là một lĩnh vực nghiên cứu và phát triển đang tạo nên làn sóng trong cộng đồng mật mã gần đây. Nhưng nó là gì và nó tốt cho cái gì? Trước tiên, hãy chia thuật ngữ thành hai thành phần và giải thích chúng là gì.
ZK là gì?
Bằng chứng không kiến thức là một giao thức mật mã trong đó một bên (người chứng minh) có thể chứng minh cho bên kia (người xác minh) rằng một tuyên bố đã cho là đúng mà không tiết lộ bất kỳ thông tin bổ sung nào ngoài tuyên bố đó là đúng. Đây là một lĩnh vực nghiên cứu đang đạt được những tiến bộ vượt bậc về nhiều mặt, bao gồm mọi thứ từ nghiên cứu đến triển khai và ứng dụng giao thức.
Hai "nguyên tố" chính (hoặc khối xây dựng) do ZK cung cấp là khả năng tạo bằng chứng về tính toàn vẹn tính toán cho một tập hợp tính toán nhất định, trong đó bằng chứng dễ dàng hơn nhiều so với việc tự thực hiện tính toán. (Chúng tôi gọi thuộc tính này là "sự đơn giản"). Bằng chứng ZK cũng cung cấp tùy chọn để ẩn một số phần của phép tính trong khi vẫn duy trì tính chính xác của phép tính. (Chúng tôi gọi thuộc tính này là "không kiến thức").
Việc tạo ra một bằng chứng không có kiến thức đòi hỏi rất nhiều tính toán, đắt hơn khoảng 100 lần so với tính toán ban đầu. Điều này có nghĩa là không thể tính toán bằng chứng không kiến thức trong một số trường hợp vì thời gian cần thiết để tạo ra chúng trên phần cứng tối ưu khiến chúng không thực tế.
Tuy nhiên, những tiến bộ gần đây về mật mã, phần cứng và hệ thống phân tán đã làm cho bằng chứng không kiến thức trở thành một lựa chọn khả thi cho các tính toán ngày càng mạnh mẽ. Những tiến bộ này đã cho phép tạo ra các giao thức có thể sử dụng các bằng chứng chuyên sâu về tính toán, mở rộng không gian thiết kế cho các ứng dụng mới.
Trường hợp sử dụng ZK
Mật mã không kiến thức là một trong những công nghệ phổ biến nhất trong không gian Web3 vì nó cho phép các nhà phát triển xây dựng các ứng dụng có thể mở rộng và/hoặc riêng tư. Dưới đây là một số ví dụ về cách nó được sử dụng trong thực tế (mặc dù lưu ý rằng nhiều dự án trong số này vẫn đang tiếp diễn):
1. Mở rộng quy mô Ethereum thông qua ZK rollup
Starknet
Scroll
Polygon Zero,Polygon Miden,Polygon zkEVM
zkSync
2. Xây dựng các ứng dụng bảo vệ quyền riêng tư
Semaphore
MACI
Penumbra
Aztec Network
3. Bản gốc nhận dạng và nguồn dữ liệu
WorldID
Sismo
Clique
Axiom
4. Giao thức lớp 1
Zcash
Mina
Khi công nghệ ZK trưởng thành, chúng tôi tin rằng sẽ có sự bùng nổ của các ứng dụng mới vì các công cụ được sử dụng để xây dựng các ứng dụng này sẽ yêu cầu ít chuyên môn về miền hơn và các nhà phát triển sẽ dễ dàng sử dụng hơn.
học máy
Học máy là một lĩnh vực nghiên cứu trong lĩnh vực trí tuệ nhân tạo ("AI") cho phép máy tính tự động học hỏi và cải thiện từ kinh nghiệm mà không được lập trình rõ ràng. Nó sử dụng các thuật toán và mô hình thống kê để phân tích và xác định các mẫu trong dữ liệu, sau đó đưa ra dự đoán hoặc quyết định dựa trên các mẫu này. Mục tiêu cuối cùng của học máy là phát triển các hệ thống thông minh có thể học một cách thích ứng mà không cần sự can thiệp của con người và giải quyết các vấn đề phức tạp trong các lĩnh vực khác nhau như chăm sóc sức khỏe, tài chính và giao thông.
Gần đây, bạn có thể đã thấy sự tiến bộ của các mô hình ngôn ngữ lớn như chatGPT và Bard cũng như các mô hình chuyển văn bản thành hình ảnh như DALL-E 2, Midjourney hoặc Stable Diffusion. Khi các mô hình này trở nên tốt hơn và có thể thực hiện nhiều nhiệm vụ hơn, điều quan trọng là phải hiểu mô hình nào thực hiện các hoạt động hoặc liệu các hoạt động đó có được thực hiện bởi con người hay không. Trong các phần tiếp theo, chúng ta sẽ khám phá dòng suy nghĩ này.
Động lực ZKML và những nỗ lực hiện tại
Chúng ta đang sống trong một thế giới mà nội dung do AI/ML tạo ra ngày càng khó phân biệt với nội dung do con người tạo ra. Mật mã không kiến thức sẽ cho phép chúng tôi đưa ra các tuyên bố như: "Cho một phần nội dung C, nó được tạo bởi một mô hình M được áp dụng cho một số đầu vào X." Chúng tôi sẽ có thể xác minh xem một đầu ra nhất định có được tạo bởi một ngôn ngữ lớn hay không mô hình chẳng hạn như chatGPT) hoặc mô hình chuyển văn bản thành hình ảnh (như DALL-E 2 ) hoặc bất kỳ mô hình nào khác mà chúng tôi đã tạo biểu diễn mạch không kiến thức. Các thuộc tính không kiến thức của các bằng chứng này sẽ cho phép chúng tôi cũng ẩn đầu vào hoặc các phần của mô hình nếu muốn. Một ví dụ điển hình là việc áp dụng mô hình học máy trên một số dữ liệu nhạy cảm, không tiết lộ đầu vào cho bên thứ ba, người dùng có thể biết kết quả dữ liệu của mình sau khi suy luận mô hình (ví dụ trong ngành y tế).
Lưu ý: Khi chúng tôi nói về ZKML, chúng tôi muốn nói đến việc tạo bằng chứng không có kiến thức về các bước suy luận của mô hình ML, chứ không phải về đào tạo mô hình ML (bản thân nó đã rất chuyên sâu về tính toán). Hiện tại, các hệ thống không kiến thức tiên tiến nhất kết hợp với phần cứng hiệu năng cao vẫn còn cách rất xa so với việc chứng minh các mô hình khổng lồ như các mô hình ngôn ngữ lớn (LLM) hiện có, nhưng một số tiến bộ đã đạt được trong việc tạo ra các bằng chứng về mô hình nhỏ hơn.tiến bộ.
Chúng tôi đã thực hiện một số nghiên cứu về trình độ nghệ thuật của mật mã không kiến thức trong bối cảnh tạo bằng chứng cho các mô hình ML và tạo một bộ sưu tập các bài báo tổng hợp nghiên cứu, bài báo, ứng dụng và kho lưu trữ mã có liên quan. Bạn có thể tìm thấy các tài nguyên dành cho ZKML trong kho lưu trữ awesome-zkml của cộng đồng ZKML trên GitHub.
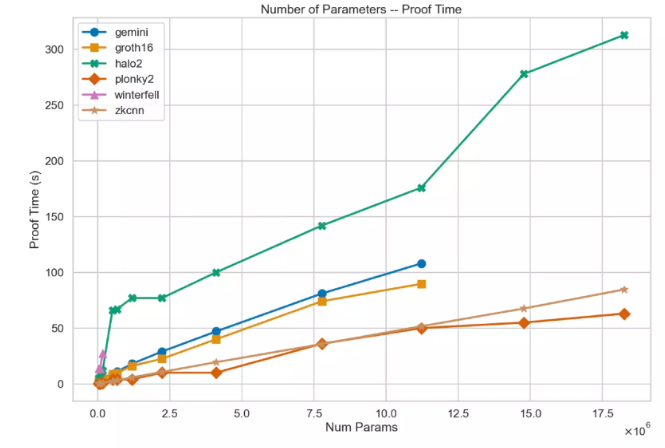
Nhóm Modulus Labs gần đây đã xuất bản một bài báo có tên "Chi phí thông minh", đánh giá các hệ thống bằng chứng ZK hiện có và liệt kê nhiều mô hình có kích thước khác nhau. Hiện tại, có thể tạo bằng chứng cho các mô hình có ~18 triệu tham số bằng cách sử dụng hệ thống bằng chứng như plonky 2 trong ~50 giây trên máy AWS mạnh mẽ. Đây là một sơ đồ từ bài báo:
Một sáng kiến khác nhằm cải thiện trạng thái nghệ thuật của các hệ thống ZKML là thư viện ezkl của Zkonduit, cho phép bạn tạo bằng chứng ZK về các mô hình ML được xuất bằng ONNX. Điều này cho phép bất kỳ kỹ sư ML nào tạo bằng chứng ZK cho các bước suy luận trong mô hình của họ và chứng minh đầu ra cho bất kỳ trình xác thực nào được triển khai chính xác.
Có một số nhóm đang làm việc để cải thiện công nghệ ZK, tạo phần cứng được tối ưu hóa cho những gì xảy ra bên trong bằng chứng ZK và xây dựng các triển khai tối ưu hóa các giao thức này cho các trường hợp sử dụng cụ thể. Khi công nghệ hoàn thiện hơn, các mẫu lớn hơn sẽ được chứng minh ZK trên các máy kém mạnh hơn trong một khoảng thời gian ngắn. Chúng tôi hy vọng những tiến bộ này sẽ cho phép xuất hiện các ứng dụng và trường hợp sử dụng ZKML mới.
trường hợp sử dụng tiềm năng
sự định nghĩa:
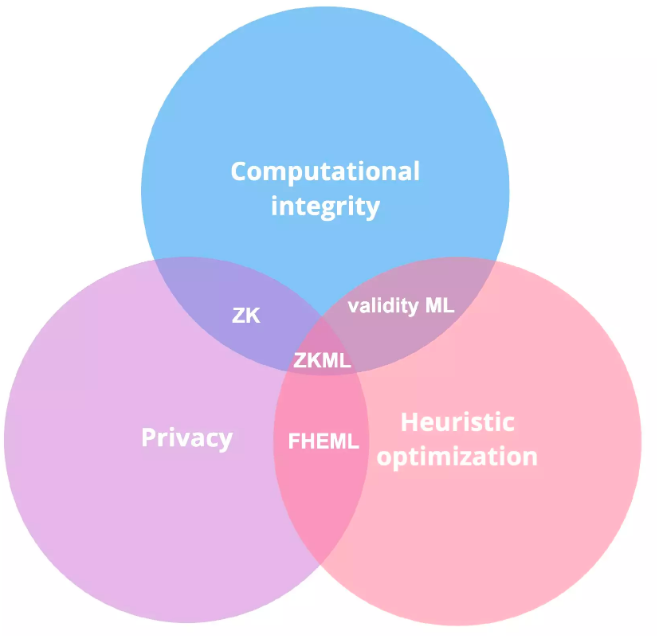
sự định nghĩa:
1. Tối ưu hóa heuristic - một phương pháp giải quyết vấn đề sử dụng các quy tắc ngón tay cái hoặc "heuristics" để tìm giải pháp tốt cho các vấn đề khó khăn, thay vì sử dụng các phương pháp tối ưu hóa truyền thống. Thay vì cố gắng tìm một giải pháp tối ưu, các phương pháp tối ưu hóa heuristic nhằm mục đích tìm ra các giải pháp tốt hoặc "đủ tốt" trong một khoảng thời gian hợp lý dựa trên tầm quan trọng tương đối và độ khó tối ưu hóa của chúng.
2. FHE ML - ML mã hóa đồng nhất hoàn toàn ML cho phép các nhà phát triển đào tạo và đánh giá các mô hình theo cách bảo vệ quyền riêng tư; tuy nhiên, không giống như bằng chứng ZK, không có cách nào để chứng minh bằng mật mã tính đúng đắn của các tính toán được thực hiện.
Các nhóm như Zama.ai đang làm việc trong không gian này.
3. ZK so với Tính hợp lệ — Trong ngành, các thuật ngữ này thường được sử dụng thay thế cho nhau, vì bằng chứng tính hợp lệ là bằng chứng ZK không che giấu một số phần tính toán hoặc kết quả của nó. Trong ngữ cảnh của ZKML, hầu hết các ứng dụng hiện tại đều tận dụng khía cạnh bằng chứng về tính hợp lệ của bằng chứng ZK.
4. Hiệu lực ML - ZK chứng minh các mô hình ML trong đó không có tính toán hoặc kết quả nào được giữ bí mật. Họ chứng minh tính đúng đắn của các tính toán.
Dưới đây là một số ví dụ về các trường hợp sử dụng ZKML tiềm năng:
1. Tính đầy đủ tính toán (ML hợp lệ)
Modulus Labs
Bot giao dịch ML có thể xác minh trên chuỗi - RockyBot
Chuỗi khối trực quan tự cải thiện (ví dụ):
Tăng cường các tính năng thông minh của giao thức tùy chọn tài chính AMM của Lyra
Tạo một hệ thống danh tiếng minh bạch dựa trên AI (ZK oracle) cho Astraly
Sử dụng ML cho Giao thức Aztec (zk-rollup với các tính năng bảo mật) để làm việc dựa trên các đột phá công nghệ cần thiết cho các công cụ tuân thủ cấp hợp đồng.
2. Máy học dưới dạng Dịch vụ (MLaaS) minh bạch;
3. Phát hiện bất thường/gian lận ZK:
Trường hợp sử dụng này cho phép tạo bằng chứng ZK chống lại khả năng khai thác/gian lận. Các mô hình phát hiện bất thường có thể được đào tạo trên dữ liệu hợp đồng thông minh và được các DAO đồng ý làm thước đo thú vị để có thể tự động hóa các quy trình bảo mật, chẳng hạn như đình chỉ hợp đồng một cách chủ động hơn, phòng ngừa hơn. Hiện đã có những công ty khởi nghiệp đang tìm cách sử dụng các mô hình ML cho mục đích bảo mật trong bối cảnh hợp đồng thông minh, vì vậy bằng chứng phát hiện sự bất thường của ZK dường như là một bước tiếp theo tự nhiên.
4. Bằng chứng có giá trị chung cho suy luận ML: Khả năng dễ dàng chứng minh và xác minh rằng đầu ra là sản phẩm của một mô hình và cặp đầu vào nhất định.
5. Quyền riêng tư (ZKML).
6. Kaggle phi tập trung: Chứng minh rằng mô hình chính xác hơn x% trên một số dữ liệu thử nghiệm mà không hiển thị trọng số.
7. Suy luận bảo vệ quyền riêng tư: Đưa các chẩn đoán y tế trên dữ liệu bệnh nhân riêng tư vào mô hình và gửi các suy luận nhạy cảm (ví dụ: kết quả xét nghiệm ung thư) cho bệnh nhân.
8.Worldcoin:
Khả năng nâng cấp của IrisCode: Người dùng World ID sẽ có thể tự quản lý sinh trắc học của họ trong bộ nhớ được mã hóa trên thiết bị di động của họ, tải xuống mô hình ML được sử dụng để tạo IrisCode và tạo cục bộ bằng chứng không cần biết rằng IrisCode của họ đã được tạo thành công. IrisCode này có thể được chèn mà không cần sự cho phép của một trong những người dùng Worldcoin đã đăng ký, vì hợp đồng thông minh nhận được có thể xác minh bằng chứng không có kiến thức và do đó tạo ra IrisCode. Điều này có nghĩa là nếu Worldcoin nâng cấp mô hình máy học của mình trong tương lai để tạo IrisCode theo cách phá vỡ khả năng tương thích với phiên bản trước đó, thì người dùng sẽ không phải truy cập lại Orb mà có thể tạo bằng chứng không kiến thức này cục bộ trên thiết bị.
Bảo mật Orb: Hiện tại, Orb triển khai một số cơ chế phát hiện gian lận và giả mạo trong môi trường đáng tin cậy của mình. Tuy nhiên, chúng tôi có thể tạo bằng chứng không cần biết rằng các cơ chế này đã hoạt động khi hình ảnh được chụp và Mã Iris được tạo, để đảm bảo tính sống động tốt hơn cho giao thức Worldcoin, vì chúng tôi có thể hoàn toàn chắc chắn rằng các cơ chế này sẽ hoạt động trong suốt quá trình tạo IrisCode.
liên kết gốc



