Understanding Cobo Safe in one article: a safe and reliable asset management solution on the chain
foreword
foreword
first level title
Why You Should Take Control of Your Assets
For a long time, because the centralized organization provides an operation experience similar to traditional Web 2.0, many users choose to use the services of the centralized organization to enter the cryptocurrency industry, but there is an old saying in the blockchain world, Not your keys, not you coins (only by mastering your own private key can you control your own assets). After users choose a centralized institution for convenience, they also sacrifice a certain amount of security. Once a crisis occurs in the centralized institution, the user's assets will disappear. Take the recent FTX incident as an example. In this turmoil, FTX’s misappropriation of user assets led to a gap of nearly 6 billion US dollars. After the risk spread, there have been reports that there are other centralized institutions that have a certain interest relationship with FTX. It is estimated that millions of people have been victims of the mine explosion this time around the world. In this turmoil, if users learn to manage assets with their own private keys at the beginning, and store most of their assets in decentralized facilities (hardware wallets, multi-sign contracts, etc.), To avoid their own losses in this incident.
However, managing private keys is not an easy task, which involves security measures and best practices in many aspects such as the generation, storage, management, and use of private keys.
On September 22, 2022, the well-known market maker organization Wintermute used Profanity’s private key generation tool to create a private key, which led to the leakage of the owner’s private key of its related contracts, causing a loss of nearly 160 million US dollars.
Coincidentally, on November 22, 2022, Shen Bo @boshen 1011, a partner of Fenbushi Capital, also tweeted that his wallet was stolen, and the amount involved reached 42 million US dollars at the time of the theft. After analysis by the security company, it was confirmed that the core problem of the incident was the leakage of the mnemonic phrase of the Trust wallet used by the user. From the above two incidents, it is not difficult to see that private key management is actually a very complicated knowledge, but in the current environment, there is a huge crisis of trust in using the services provided by centralized organizations. method, you can safely manage your own assets without worrying about the loss of all assets due to the leakage of a single private key?
Gnosis Safe – a mature multi-signature solution
Since the account structure of Ethereum itself does not support the multi-signature mode, Ethereum users cannot build their own multi-signature addresses like Bitcoin users. However, Ethereum supports smart contracts to implement various complex code logics, so it is possible to build multi-signature wallets on the chain by writing smart contracts. It should be noted that the smart contract code itself may also have security risks. Historically, there have been endless attacks on contract code vulnerabilities. Therefore, when we choose a smart contract wallet, we need to use a solution that has been audited many times and has been verified for a long time. Gnosis Safe is undoubtedly the better choice.
Through Gnosis Safe, users can host assets into multi-signature contracts and choose the appropriate signature rules according to their needs. The assets of the multi-signature wallet are no longer managed by the private key of a single address, but are managed collaboratively by multiple addresses. The initiation of each transaction requires multiple addresses to sign, and requires the total number of effective signatures to reach a preset threshold (for example, the figure below shows that sending a transaction requires 3 users to sign for confirmation). In this way Gnosis Safe can successfully eliminate the risk of total asset loss due to the leakage of a single private key.
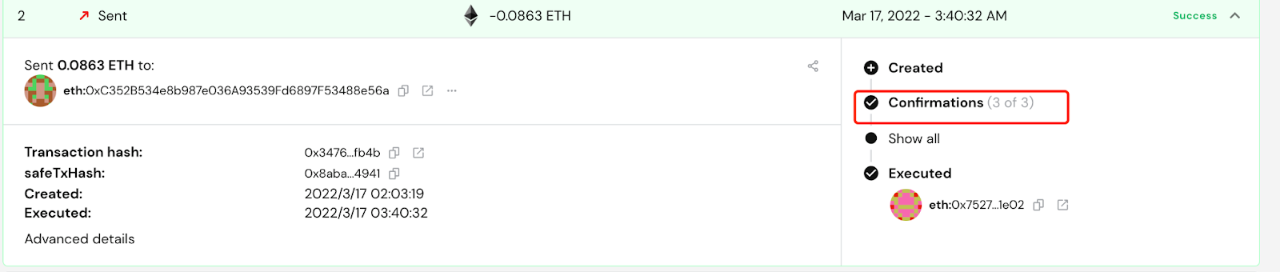
However, while Gnosis Safe improves asset security, it also has certain shortcomings in the convenience of actual use, such as:
Each transaction needs to be confirmed by multiple parties before it can be executed, which reduces the efficiency of execution compared to a single-signature address.
It does not support specific decentralization, and the power of each address in the wallet member is completely consistent.
Does not support configuring specific risk control strategies for interactive contracts
So, is there a better multi-signature product that can solve the above shortcomings while maintaining the original security of Gnosis Safe? Cobo's answer is Cobo Safe.
Cobo Safe – a flexible on-chain decentralization and risk control solution
Cobo Safe is based on Gnosis Safe for secondary development, and uses Gnosis Safe's module extension function to realize flexible customization of interaction between multi-signature wallets and project contracts.
secondary title
single signature
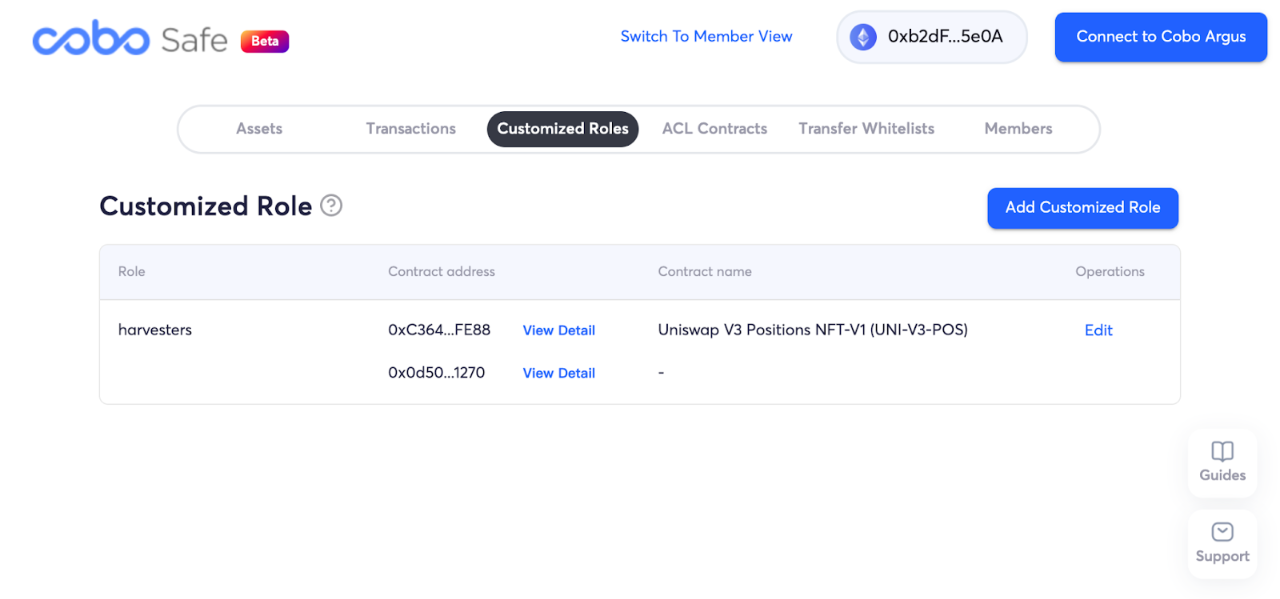
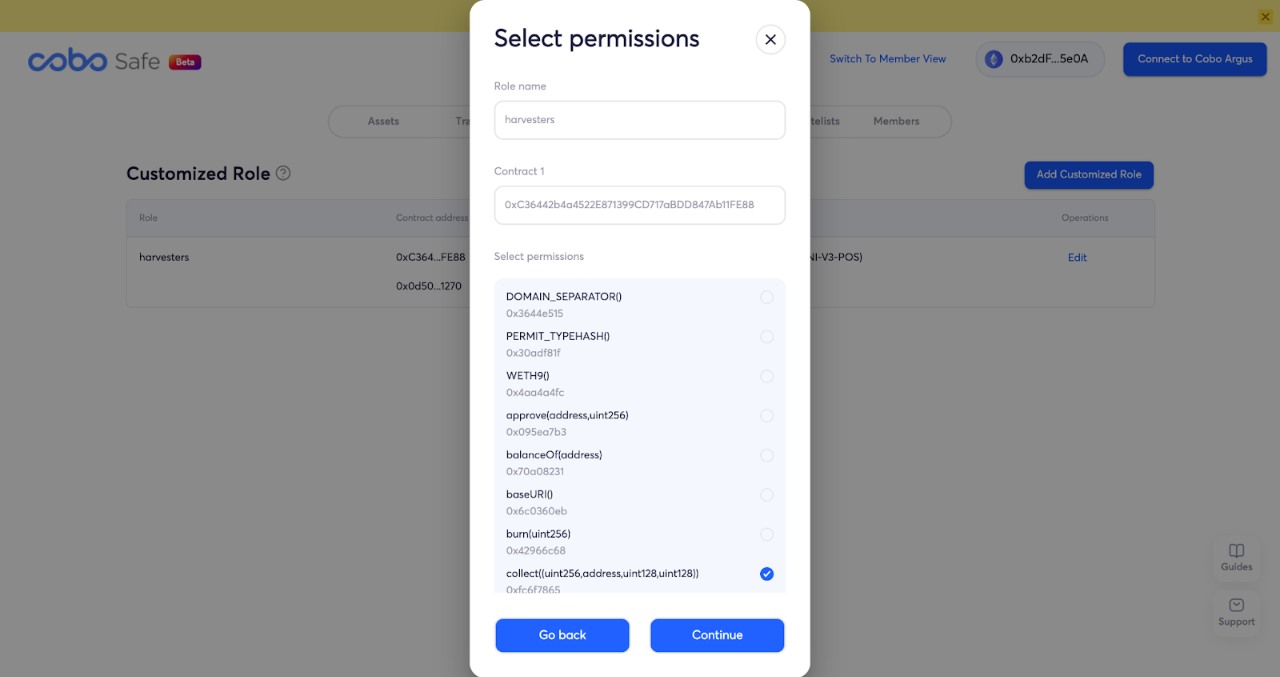
Cobo Safe currently supports decentralized management at the function level, that is, different function interaction permissions can be configured for specific user roles. It only needs to perform simple configuration on the web interface, and the user role (Role) can be given permission to call specific contracts and specific functions. The harvesters role configured as follows can and can only call the collect function of the Uniswap V3 NonfungiblePositionManager contract, that is, it can only complete the withdrawal of Uniswap V3 LP transaction fee rewards.
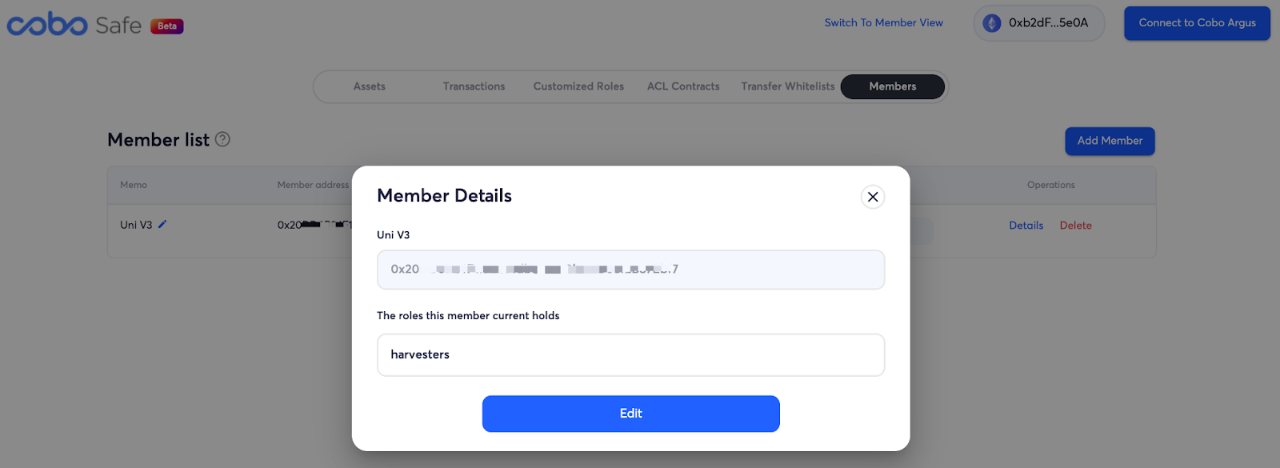
While adding members to Cobo Safe, the aforementioned restricted user roles can be assigned. An address assigned a certain role can enable a multi-signature wallet to execute a specific contract call transaction. The role of harvesters is assigned to the 0 x 20 XX address as follows, allowing the 0 x 20 XX address to act as a multi-signature wallet to initiate the contract transaction of the collect function call.
secondary title
ACL risk control
In addition to the function-grained decentralization mechanism, Cobo Safe also provides a more fine-grained ACL (Access Control List) contract risk control mechanism. Users can customize any decentralization and risk control rules according to their own business scenarios. Through the ACL contract, various decentralization and risk control rules can be flexibly set, such as:
Through the ACL contract, various decentralization and risk control rules can be flexibly set, such as:
Limit the parameter range of the user contract call process (for example, when specifying swap, only certain types of token assets are allowed to be operated)
Limit the number of calls to a contract function
Perform risk checks on contract interactions (such as checking that swap slippage losses are not higher than a certain percentage)
Summarize
Summarize
Recent security incidents have also alerted us to the fact that whether assets are stored in a centralized institution or private key mnemonics are managed by themselves, there are still certain asset security risks.
These security risks drive all parties to seek better asset custody solutions. Major centralized custodians have recently launched MerkleTree-based proof-of-reserve schemes, and Cobo co-founder Dr. Jiang Changhao also published some discussions on the limitations and improvements of existing schemes (https://mp.weixin.qq.com/s/mHydXy-EnZAkrkZppI 3 YzQ)。
Cobo Argus (https://argus.cobo.com/) is a decentralized hosting solution, and its integrated Cobo Safe module extends the industry's mature multi-signature solution Gnosis Safe, providing more flexibility such as decentralization and ACL risk control The customizable function better balances the natural contradiction between asset security and wallet convenience, and is a new choice for institutions and individuals to survive the capital winter and welcome the next round of prosperity as a fund management tool.



