ArkStream Capital: Explain in detail the investment opportunities of zk in the expansion and privacy protection track (2)
Original Author: Ray
Related Reading
Related Reading
Zero Knowledge Proof and Scaling
Currently,The starting point of all blockchain designs is essentially around blocks.Transactions constitute block data, and the consensus mechanism determines block generation, verification, and order. Thinking from the perspective of transactions, the transaction is initiated through the signature of the user's private key, and enters the transaction memory pool of the entire network through network broadcasting.Block Builder/MEV Searcher/SequencerPick a transaction and submit the transaction list toblock builder, block builder/block producerSubmit blocks to the network,block validatorAfter verifying that the block is legal and valid, it will be confirmed on the chain. Thinking from the perspective of the block, the block must be completedConstruct, submit and confirm on-chainThree steps.The decentralized design mechanism will increase the cost and security of the entire network for each link of the transaction or block, so as to achieve machine trust.The legal longest blockchain, we call it the main chain/layer network/basic chain/Layer1.
In the field of software design and development, the design pattern has a single responsibility, the design architecture has a layered architecture, and the design principles have high cohesion and low coupling.All of these theories and guidance are aimed at refactoring software with modular thinking.The modularity of the blockchain can be obtained fromData availability (data layer), logic execution (execution layer) and consensus mechanism (consensus layer)divided into three main levels. If the expansion corresponds to these three levels, then there will be data layer expansion, execution layer expansion and consensus layer expansion respectively. For simplicity, we followmain chainWhether it is changed or not, it is divided into on-chain expansion and off-chain expansion. The expansion scheme on the chain includes increasing the block size, sharding, and adjusting the consensus mechanism. Off-chain expansion solutions include segregated witness, state channel, side chain, Plasma, and Rollup. The explosion of DeFi and the prevalence of NFT have increased the demand for expansion of the Ethereum network. In December 2021, Vitalik released "Endgame", depicting theThe future of Ethereum will be the coexistence of centralized block generation, decentralized verification, and multiple Rollups.With the strong support of Vitalik, Rollup has become the mainstream solution for Ethereum off-chain expansion. Among the many Rollup subdivision schemes,by technology type, can be divided into Optimisitc Rollup (ORU) and ZK Rollup (ZKR),The main difference between them isThe transaction validity guarantee scheme is different, Optimistic uses game fraud proofs, and ZK Rollup uses mathematical zero-knowledge proofs.
Whether it is Optimistic Rollup or ZK Rollup, they must handle a large number of transactions and support general-purpose computing for smart contracts on the premise of inheriting the security and data availability of Ethereum.Optimistic Rollup is to compress a large amount of transaction data, and then submit the compressed transaction data and state root to Ethereum.In addition, the Optimistic Rollup network has a challenger role, which can prove the fraud of the data submitted to Ethereum, and then roll back invalid transactions through the consensus of the Optimistic Rollup network.As for ZK Rollup, when processing transaction data in batches, zero-knowledge proof technology is used. On the basis of ensuring the validity of transaction data, the proof is directly submitted to Ethereum, and the final consistency of the state is achieved immediately.In terms of smart contract general computing, Optimistic Rollup directly uses the Ethereum EVM, while ZK Rollup’s team either develops zkVM or adopts the path of zkEVM. Therefore, dApp projects can be seamlessly migrated to Optimistic Rollup, while ZK Rollup Much of the Rollup network will require minor and minor changes.
Different types of Rollup, with special network participants, ORU has fraud proofchallenger, ZKR has the ability to perform calculations and aggregate zero-knowledge proofsCompute Provers and Aggregators. Layer 2 processes the transactions of the two-layer network in batches(Rollup)Later, submitted to the layer networksmart contractsmart contract, thus obtaining the security and data availability of a layer network. At this time, a layer of networkDegree of decentralization, block verification mechanismIt will become an endorsement of the validity of the second-tier network transactions.
In the Layer2 network technology scheme and architecture, compared with the game modelORU adopts zero-knowledge proof, and ZKR, which can carry out mathematical verification, will have more technical advantages, but the latter develops relatively slowly and requires more time. Therefore, there are also a large number of projects conducting forward-looking explorations in this field.Next, we will explore several ZKR related projects.
Starkware:Based on the self-developed STARK protocol, the technical service provider who invented the Cairo circuit programming language and its zkVM. The product line includes special-purpose StarkEx and general-purpose StarkNet. StarkEx is positioned as a layer-2 network expansion engine that serves specific application needs. It has served many customers, such as Sorare, Immutable, dYdX (V3), DeversiFi (rhino.fi), Celer, etc., and now has a TVL of more than 600 million US dollars, 2 More than 100 million transaction volume and other business data.
StarkNet is positioned as a universal, composable, and decentralized ZKR.image description
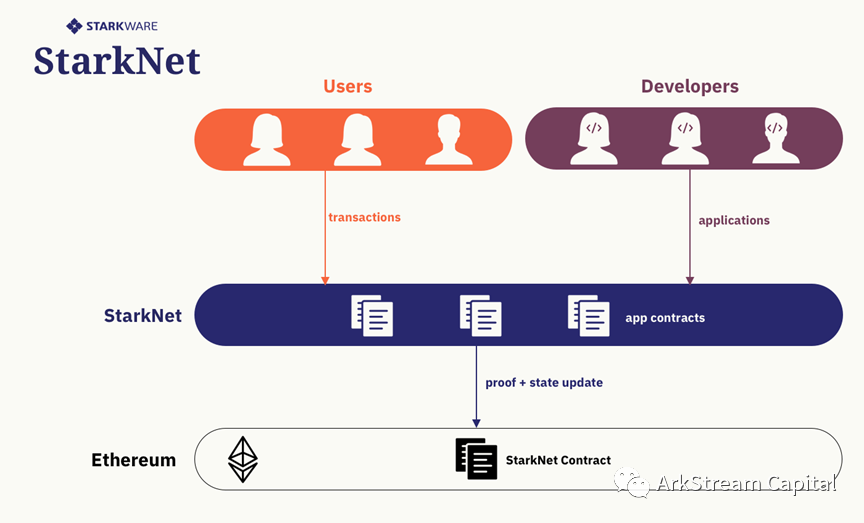
Figure1: StarkNet Intro
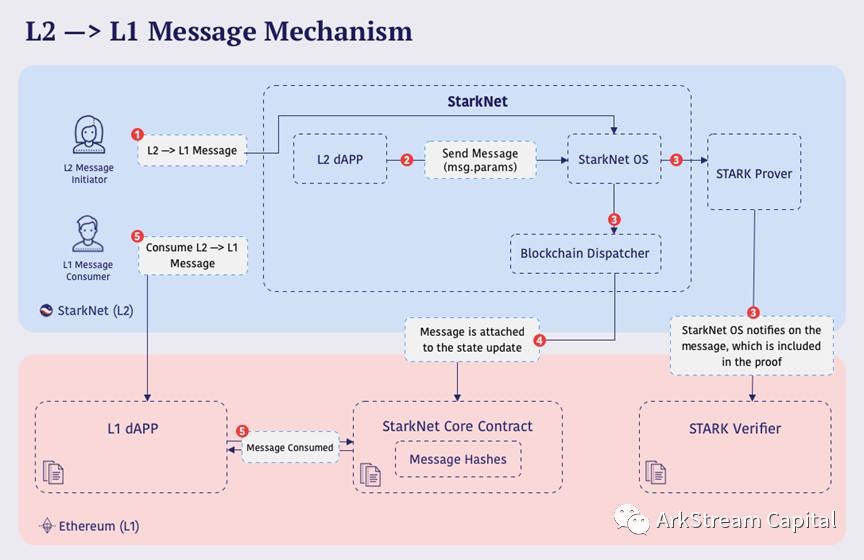
Figure2: StarkNet Messaging Mechanism L2->L1
The official gateway of StarkNet, StarkGate, has been released and launched, and will open the deposit and withdrawal experience with a limited amount from time to time. Now the total number of bridged assets is about 775 ETH. The Cairo language style is biased between Golang and Python, and a new native type of circuit programming language: Field Element (felt). There are few general-purpose libraries developed, mainly provided by the official. It does not support zkEVM, that is, it does not support the direct compilation and deployment of Solidity code. It needs to be converted into Cairo code through the Warp translator before deployment. Some features of Solidity are clearly not supported, and the most influential one is SHA256. StarkNet's ecological projects cover wallets, DEX, DAO and other tracks, mainly native projects, and have a low degree of overlap with Ethereum dApp projects. For details, please refer to the official ecological website. From the block explorer, we can see that there are currently no frequent transactions, and the average number of transactions per block is about 115.
image description
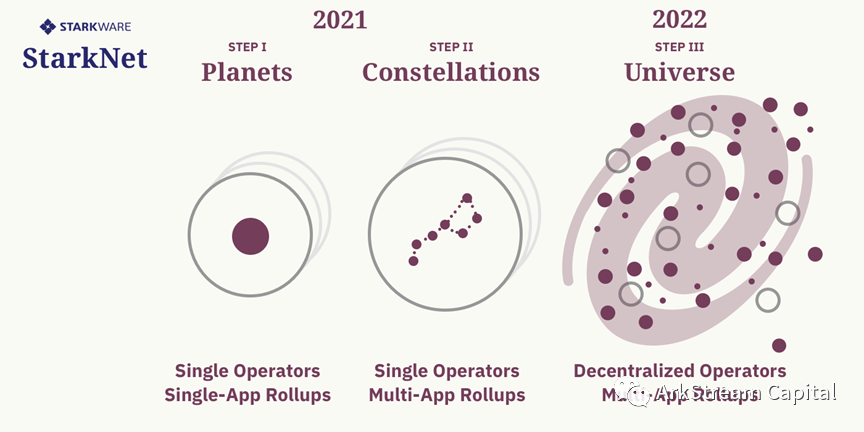
Figure3: StarkNet Decentralization Roadmap
zkSync: Based on the PLONK protocol (version 1.0) and the self-developed transparent RedShift protocol (version 2.0/future), which supports Solidity/Vyper programming, ZKR of zkEVM.Before zkSync 1.0, the Zinc circuit programming language and the corresponding SyncVM (zkVM) were launched, but now they are basically stagnant, and changed to zkEVM that supports Solidity/Vyper programming, that is, zkSync 2.0. Now in the iterative stage of the zkSync 2.0 test network, the main network will be released in the next 100 days and zkEVM will be open sourced. In addition to the zkRollup solution for data on-chain, zkSync also launchedThe zkPorter solution where data is not uploaded to the chain.For zkSync 2.0Operator operator and System Contracts system contractThe design completes L2 to L1 contract deployment functions, L2/L1 communication functions, etc. The current Operator is run by the zkSync team and will be decentralized in the future. Since zkSync claims the compatibility of EVM bytecode and as a community-driven project, zkSync has received support from many well-known Ethereum dApp projects, such as 1inch, Yearn Finance, Aave, Chainlink, and The Graph. The ecological projects of zkSync can be queried through the official ecological website. Live status includes wallets, derivatives exchanges, and bridges. As can be seen from the block explorer, there are nearly 100,000 blocks submitted for confirmation, and the total number of transactions exceeds 10 million, with an average of 100 transactions per block.image description
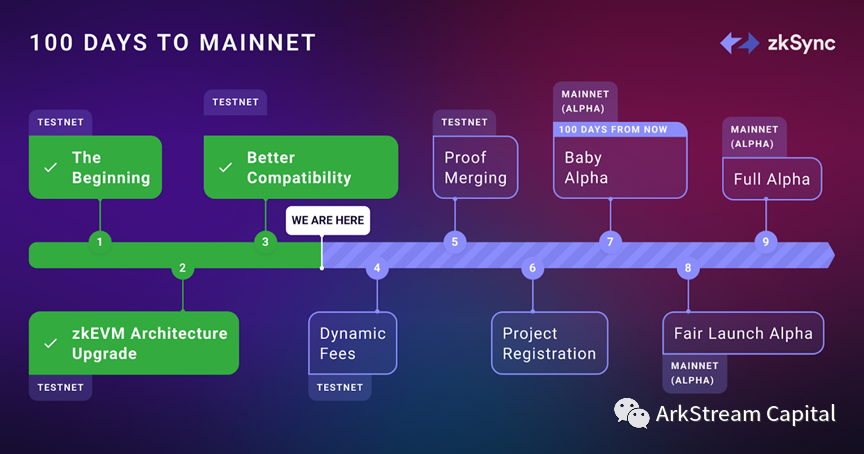
Figure4: zkSync 2.0 100 Days to Mainnet
Scroll: native zkEVM solution, integrated ZK's previous research technologies (polynomial commitment, Lookup Table, recursive proof) and ZKR accelerated by GPU/ASIC hardware.Scroll's L2 network consists of Node (Replayer, Sequencer, Coordinator) and Roller, as well as the corresponding Bridge and Rollup smart contracts on L1. It is recommended that you read the official architecture explanation article directly, which is very easy to understand. Here we briefly talk about: Sequencer receives L2 transactions, processes L2 transaction lists, constructs blocks and state roots, Coordinator monitors blocks and distributes block execution stacks to Roller, Roller calculates zkEVM circuit and generates aggregation circuit proof, and then returns to Coordinator, Coordinator passes Replayer submits to the Rollup contract of L1, and Replayer also assumes the function of L1/L2 communication bridge.Since Scroll and the Ethereum Foundation PSE (Privacy & Scaling Explorations) have been working on privacy and scaling issues for more than a year, Scroll's zkEVM solution is very native. From the code warehouse disclosed by Scroll, it can be seen that the zkEVM solution is consistent with the PSE, and the L2 Node will be implemented based on Go-Ethereum (Geth).image description
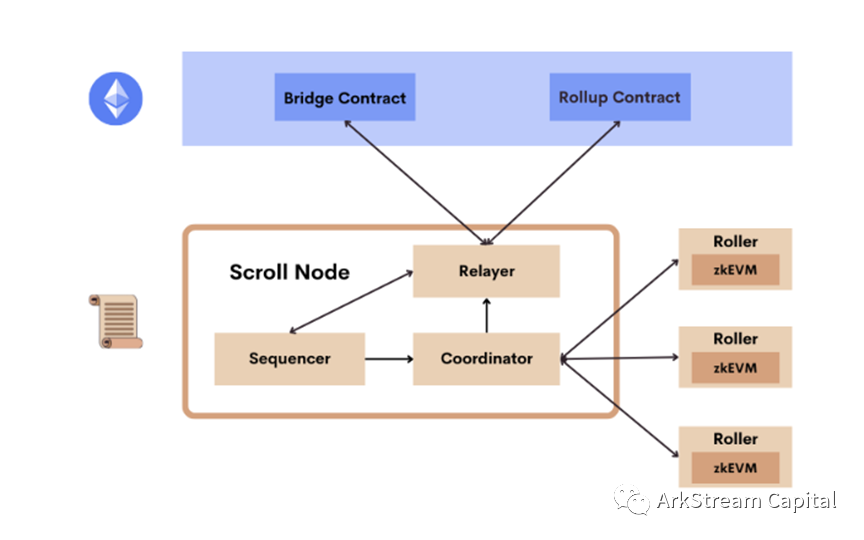
Figure5: Scroll Architecture
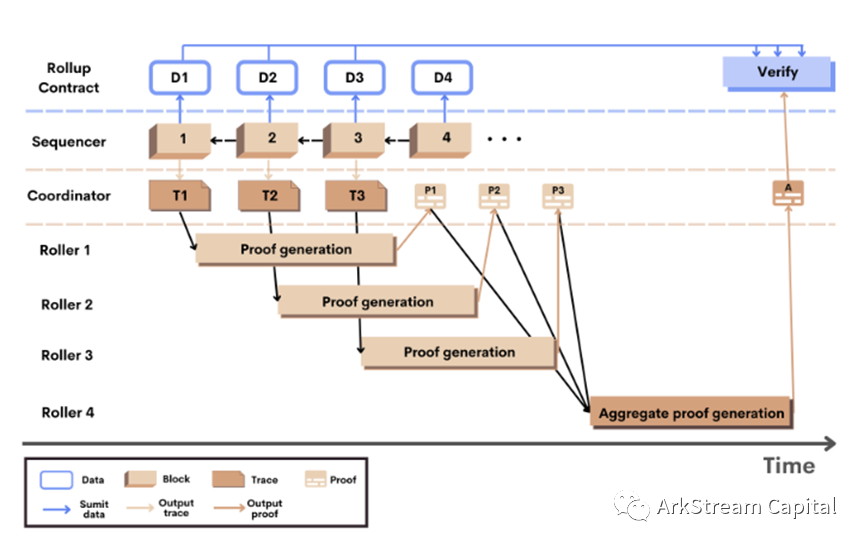
Figure6: Scroll Workflow
Polygon(MATIC):image description
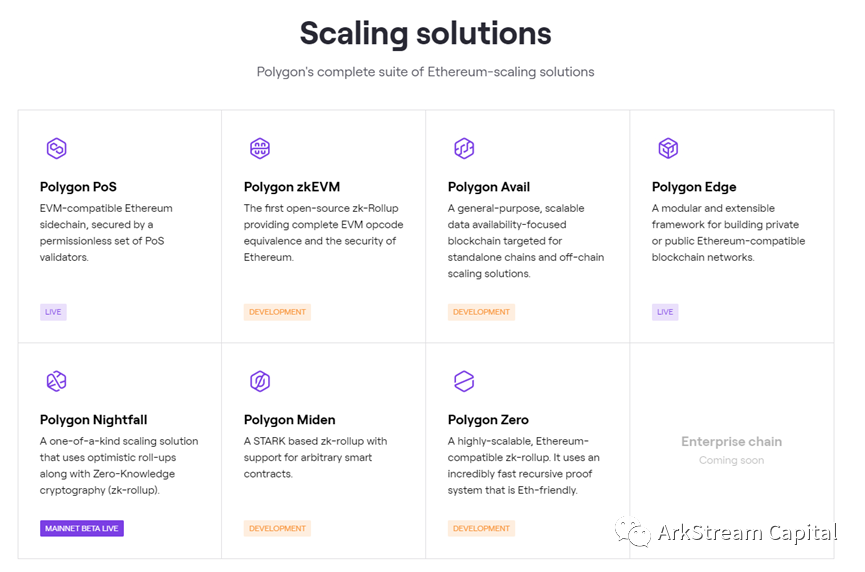
Figure7: Polygon Scaling Solutions
Polygon zkEVM(Hermez):Hermez 1.0 adopts the PoD (Proof of Donation) consensus mechanism of the decentralized bidding model and the main payment function L2 made by ZKR. The main network was launched in March 21, and the block browser has batch-generated transactions intermittently. Hermez 2.0 is adjusted to the L2 of the zkEVM solution, and the consensus mechanism is upgraded to PoE (Proof of Efficiency). The L2 architecture diagram of Hermez 2.0 is as follows. It can be seen that it is very similar to the Scroll architecture, so we will not repeat the basic process and functions of the interaction between the L2 parties. The core role of zkEVM is zkProver (compared to Scroll's Roller). Let's take a look at the internal composition of zkProver.zkEVM expresses state flow in polynomial formimage description
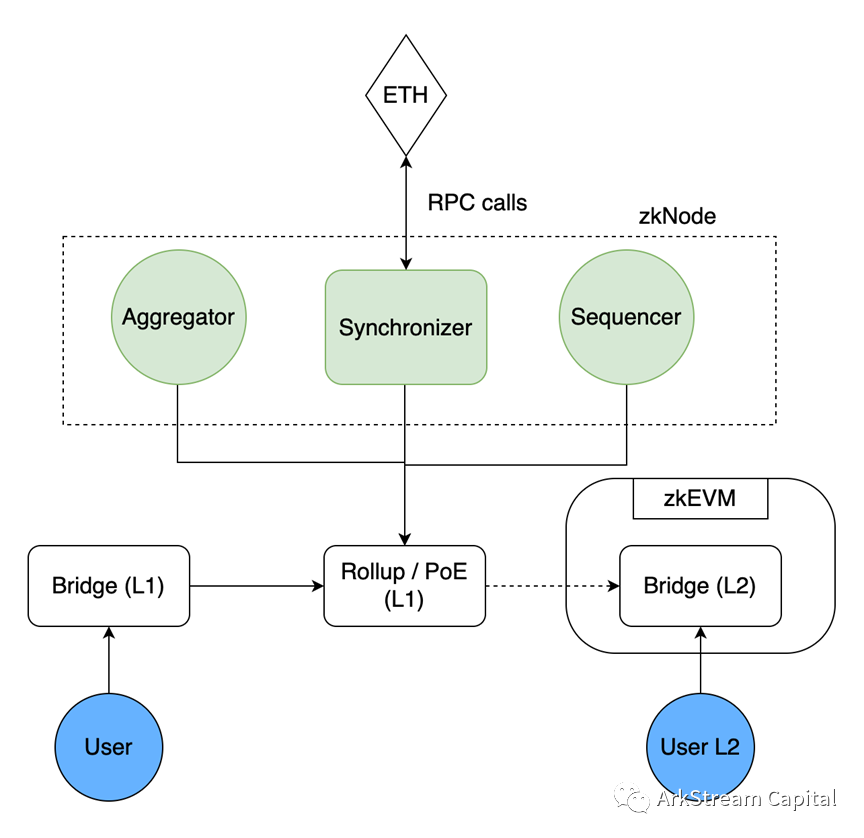
Figure8: Skeletal Overview of zkEVM
zkProver contains Main State Machine Executor (Executor), Secondary State Machines(STARK Recursion Component), STARK Builder(CIRCOM Library)and SNARK Builder(zk-SNARK Prover), brackets are another way of understanding, refer to the figure.
1. Main State Machine Executor: It uses zkASM (zero-knowledge Assembly language) to interpret the EVM bytecode of the transaction and set polynomial constraints. At the same time, Polynomial Identity Language (PIL) is used to encode polynomial constraints.
2. Secondary State Machines: Split the state flow corresponding to the zkEVM transaction, and use the corresponding multiple state machines to calculate and verify the correctness of the transaction.
3. STARK Proof Buidler: Calculate and generate proofs that meet the STARK polynomial constraints(calculation speed is fast)。
4. SNARK Proof Builder: Calculate the SNARK proof of STARK(reducing the size of the proof)image description
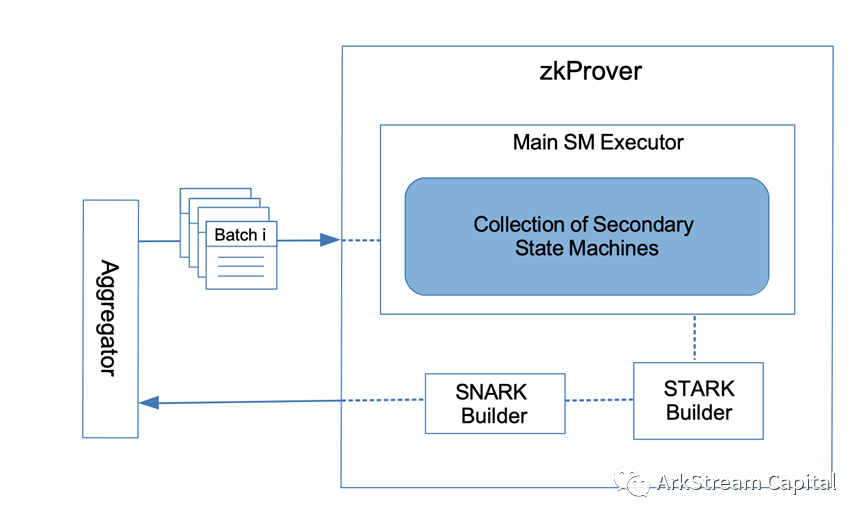
Figure9: A Simplified zkProver Diagram
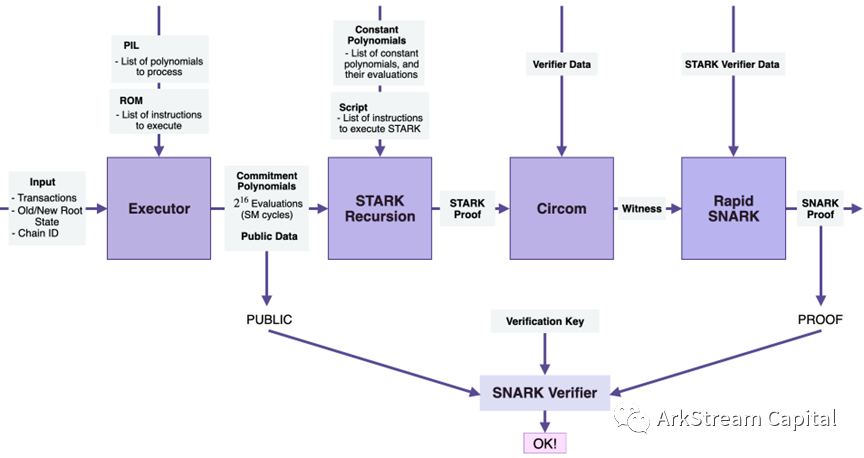
Figure10: Simplified Data Flow in the zkProver
image description
Figure11: Polygon zkEVM Open Source
In a nutshell, Hermez 2.0 is a zkEVM-type, decentralized PoE consensus L2 that combines Plonkup Lookup and Starkware's STARK protocol with a new assembly scheme. It is planned to release the testnet in Q3 in 2022 and the mainnet in 2023.
Polygon Zero:Self-developed Plonky2 based on Plonk protocol and FRI technology, zkEVM compatible L2. The Mir project acquired by Polygon for $400 million was renamed. Zero's information is mainly viewed on Mir's official website and Polygon's blog. The features claimed by Zero are support for recursion, high efficiency and fast, and small proof size. The project code warehouse has been updated, and it contains evm modules.image description
Figure12: Polygon Zero Processing A Block
Polygon Miden:Based on the STARK protocol, it supports multi-language development (including Solidity), compatible with EVM, and launched the circuit programming language Miden Assembly and L2 of Miden VM. Miden VM is an evolution of Distaff VM, which integrates Facebook's open source proof system library Winterfell. From the architecture diagram of the official website, Miden has the design of Operator, but there is no official document for this part of content, EVM compatibility, L2 route and progress.image description
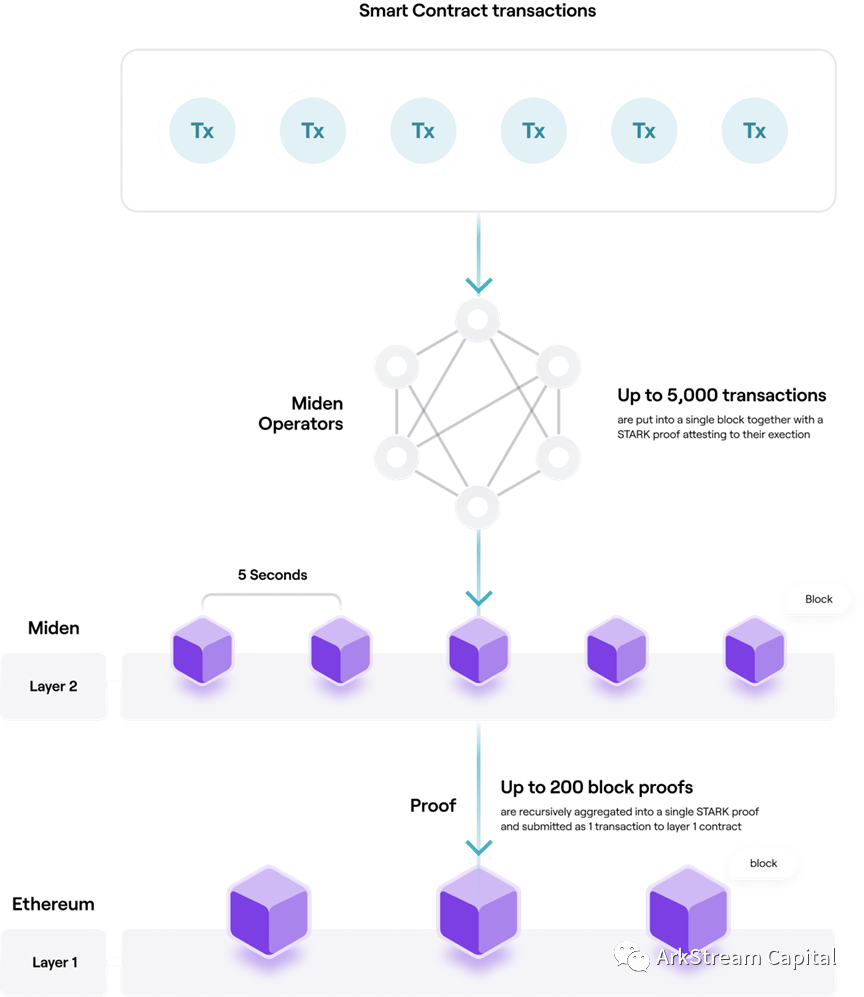
Figure13: Polygon Miden Intro
Polygon Nightfall:image description
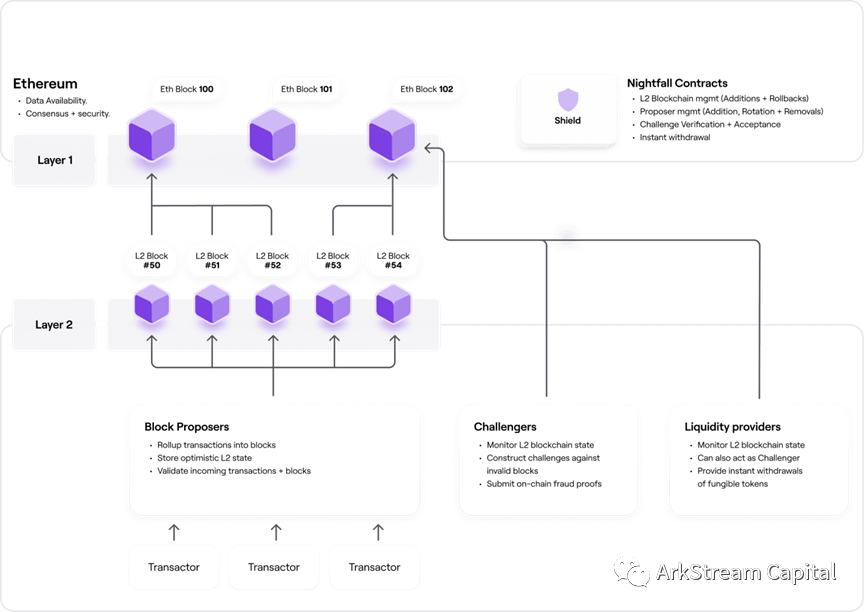
Figure14: Polygon Nightfall Intro
Mina: In addition to L2, there are some projects that explore L1 expansion based on ZKP, such as Mina, a lightweight blockchain (L1) developed based on recursive SNARK.The entire blockchain network maintains the SNARK proof of the latest block to ensure the correctness of the entire blockchain, and the size is maintained at 22KB. The network has the ability to maintain complete dataArchive Node, execute the consensus mechanism to produce blocksblock producerand handle zero-knowledge proof calculationsSNARK producer. Mina proposed that zkApp written in TypeScript, if the corresponding zkApp business logic is to be implemented, developers need to implement internal Prover and Verifier functions. The Mina main network will be launched in March 2021. The network architecture is similar to L2 batch transactions. Archive Node is equivalent to the maintainer of the data availability layer, block producers are equivalent to sequencers, and SNARK producers are similar to Roller and Hermez of Scroll. 2.0's zkProver role, but zkApp's application positioning is relatively limited, neither has the versatility of zkVM nor supports zkEVM.You can continue to follow up on the iterative progress of Mina's zkApp.
In summary, the technical development of ZK in the field of capacity expansion is still in full swing, especially the realization of zkEVM, the realization of L2 network architecture and the transformation of decentralization.Judging from the top 20 most gas-burning contracts on ETHGasstation in the past 30 days, they are mainly Opensea, DeversiFi, Uniswap, USDT, USDC, Metamask Swap, Axie Infinity, NFT Worlds and other projects. In order for L2 to be widely used, it is necessary to obtain these DEX, NFT MarketPlace, GameFi, and financial derivatives, etc.High Frequency Trading Scenarioproject support.first level title
Zero-knowledge proofs and privacy
If Web3 represents the awakening of individual sovereignty, then privacy will be an indispensable part of Web3.With the development of the industry, the composability of DeFi and the social changes brought by NFT have made us more and more aware of the safety and convenience of asset ownership compared to centralized custody, and the completely transparent information on the chain has further inspired us. The need for privacy protection. However, in the face of the escalating regulatory policies of various countries, how to protect privacy and to what extent is a question worth discussing.
Recently, the U.S. Department of the Treasury issued a policy to directly impose sanctions on Tornado Cash, a privacy payment platform in the Ethereum ecosystem, which led to the blacklisting of addresses that have interacted with Tornado Cash by USDC issuer Circle, as well as Tornado website pages, code warehouse Github, official Telegram, official Discord, etc. were shut down.We believe that everyone has the appeal and right to protect their privacy, and the abuse of privacy products does not mean that they themselves have original sin, the original intention of the design of privacy products is to protect the privacy of users' routine transfer payments. It is undeniable that criminals/hackers use it to cause many problems, but the key is not to ban privacy products, but to find ways to balance privacy and legal compliance, such as ZCash's attempt to be compatible with global AML/CFT anti-money laundering standards as well asAsset compliance certification tool provided by Tornado Cash.
Now the privacy implementation schemes involved in the encryption industry are different because of their different usage scenarios(private payment, private transaction and private general computing), there are many differences in the selected schemes, mainly involving the following six categories:
1. CoinJoin/Mixer: Mainly used for hidden payment, based on the UTXO model, the essence is to create multiple token transfers with the same input and output to achieve hidden payment. Concealed payments can be achieved to a certain extent. However, if you really want address analysis and control, the big deal is to control the withdrawal addresses of all outputs. In order to overcome the problems of the currency mixing scheme, Dash proposes the concept of a privacy payment layer, allowing the privacy payment layer to participate in the mixing of deposit addresses and reducing the correlation between access addresses. Tornado combines ZKP to cut off the link between access addresses.
2. Ring signature: multiple addresses form a ring, and the signature of an address in the ring can trigger the ring signature without relying on other addresses, and realize the privacy of the address signature in the ring. The earliest proposal of Monero.
3. Homomorphic encryption: directly calculate and output the ciphertext. We believe that this technology is a cutting-edge technology, similar to zero-knowledge proof, but the overhead for ciphertext operations is very high. Sunscreen invested by Polychain Capital and Coinbase Ventures is currently exploring in this technical direction.
4. Secure Multi-Party Computation (MPC): Without the participation of a trusted third party, multiple participants can perform calculations in a secure and non-disclosure manner. PlatON initiated by Dr. Xiao Feng, chairman of Wanxiang Blockchain, has been researching and using it for a long time in this area.
5. TEE (Trusted Execution Environment): Trusted Execution Environment, similar to the concept of a black box, the input is passed into the TEE, and the output is encrypted after the TEE executes the result. The existing ones using this technology are mainly Oasis and Secret Network.
6. ZKP: Use zero-knowledge proof technology to realize private payment and private general computing. New projects for privacy payment include Iron Fish, PoW network + UTXO model + Groth16's zk-SNARK, which is very similar to ZCash in design, and does not mention whether it supports privacy programming. The private general computing projects are best known as Aleo, Aztec, and Espresso.
After talking about the basic implementation plan, we select some projects involving zero-knowledge proofs to study and analyze.
Tornado Cash:The introduction we often see is that the user deposits to Tornado, obtains the deposit certificate, and then when withdrawing money, any user (address) can use the deposit certificate to withdraw funds, thus realizing the private payment transaction. This description is from the perspective of user experience, but it does not go deep into the core of Tornado. Tornado’s technology to achieve privacy has two points: the lump sum deposit and withdrawal fund pool that confuses the inflow and outflow of funds, and the ZKP that cuts off the association of access addresses.
The currency mixing pool is relatively easy to understand, so we focus our analysis on ZKP. Since Tornado’s front-end website and code warehouse are now closed, it is difficult to find official information. Therefore, we directly analyze the transaction and contract code on the chain. There are only two operations that users actually need to do with Tornado:Deposits and withdrawals.This is all done through the routing contract of Tornado Cash, and the routing contract will call the contract for the specific deposit and withdrawal amount (1ETH/10ETH, etc.). Deposit operation Tornado returns userNote, submitted to the chainCommitment. The withdrawal operation is submitted to the chainProof、Root、NullifierHash。These few parameters, they are determined by Tornado'sCentralized code construction generation, is the key to understanding the use of ZKP.
We compare Tornado to a bank responsible for deposits and withdrawals, and Ethereum to a public treasury, so that we can easily understand the user's operation steps in Tornado:
1. Deposit: The user fills in the deposit receipt, and the bank uses a single special safe(Commitment)Manage deposit receipts, and according toRandom numbers generate two passwords, one password is used to lock the safe, and the other password is used to record the access status of funds,ThenLocked, with funds access statusThe safe is placed in a secret random location in the public vault. The bank returns the safe, random number and safe storage location information to the user;(Note)
2. Withdrawal: The user tells the bank the random number and the location of the safe, and the bank can know through calculation: the secret random location of the safe(Root), the access status of funds(NullifierHash), and the code to unlock the safe(Proof). When all checks and verifications are correct, complete the withdrawal and update the status of the deposit and withdrawal of funds;
Through Mixer and zero-knowledge proofs, Tornado isEthereum Mainnetimage description
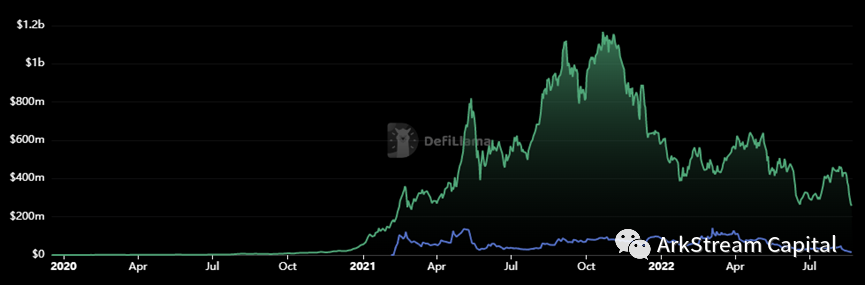
Figure15: Tornado Cash TVL and MarketCap
Aztec:The zk-Rollup Layer 2 network, which focuses on privacy protection and privacy asset interoperability, adopts the self-developed Plonk protocol, launched the zk.money privacy payment product, recently launched the connection bridge Aztec Connect, and will launch Plonk Rollup's expanded layer 2 network in the future . In the Plonk Rollup two-tier network, the circuit programming language Noir will be launched to support privacy smart contracts. The Plonk protocol requires a trusted setting, however, Aztec uses MPC (multi-party secure computing) to solve the trusted setting. The credible setting of MPC is to allow multiple trusted public celebrities to endorse together. Aztec completed the credible setup of the MPC with an ignition ceremony in January 2020. The iterative route of the product is promoted layer by layer. From the early zk.money, to the recent Aztec Connect, and the future Plonk Rollup, the Aztec team is improving its product positioning step by step, as well as the adjustment and optimization of the corresponding Plonk protocol ( TurboPlonk, UltraPlonk). In the Aztec 1.0 period, the Aztec protocol was introduced extensively. Now it is the Aztec 2.0 period, and the official website cannot find too many overall network designs. Therefore, we continue to use the Aztec 1.0 documents for learning.
zkAsset: Privacy asset, proposed in EIP1724, is used to convert the open and transparent assets of Ethereum into private assets. After confirming that the assets are transferred to the Note registry through zero-knowledge proof, the corresponding zkAsset will be minted, similar to the Shield assets of Secret (similar to The deposit process of Tornado Cash, however, Aztec is carried out on the chain to increase the concept of privacy assets).
Aztec Cryptography Engine (ACE): Distribute the proof to the verification and update the state of the Note registry according to the proof verification result.
image description
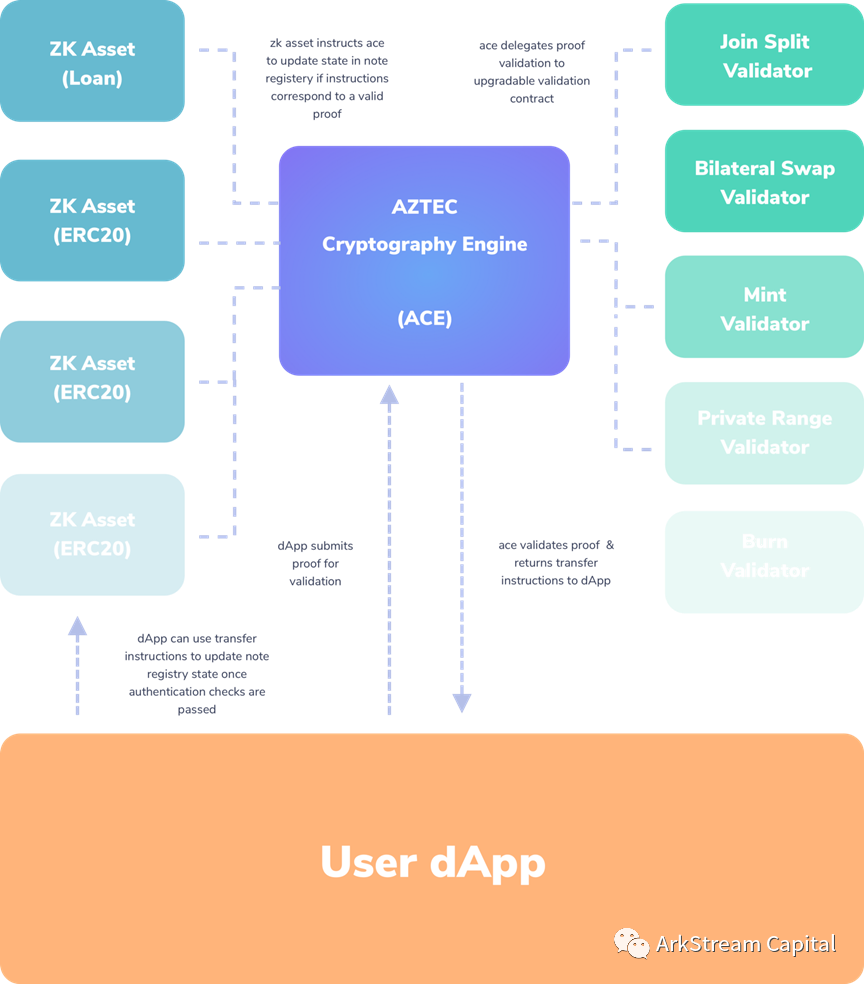
Figure16: Aztec 1.0 Architecture
After going live in June 2021, Aztec's peak TVL once reached 14 million US dollars, but now it stabilizes at around 4 million US dollars. Compared with the size of Tornado, Layer2's privacy network audience seems to be much smaller, which may be limited by its higher threshold to some extent. And affected by the Tornado incident, other privacy products that interact with the Ethereum mainnet have also been implicated. This may be an issue that developers need to discuss in the future.
Aleo:image description
Figure17: The Future of Zero Knowledge with Aleo
Espresso:The respective characteristics of Aleo and Aztec have been studied and improved, based on the L2 of ZK Rollup and the L1 double-layer network with configurable asset privacy. Configurable privacy assets allow asset creators to set privacy viewing rules and asset freezing rules for asset sending and receiving addresses, sending and receiving quantities, holding quantities, etc. Propose your own VERI-ZEXE for the concept of ZEXE, propose your own optimized version of PLONK for Aztec’s TurboPlonk and UltraPlonk, and name the Rust implementation version code as Jellyfish and open source. current,image description
Figure18: Espresso Systems Configurable Asset Privacy for Ethereum
Zecrey:A two-layer network that supports L2 of multi-chain ZKR and L1 with cross-chain function and privacy protection, but does not support zkEVM/zkVM. L1's privacy is based on the BulletProofs protocol improved version (LNCS) / Sigma protocol confusion fund pool, providing users with private transfer and private transaction functions directly at the public chain level. L2's ZKR uses the PLONK protocol. Referring to the architecture diagram of the official white paper, there is a large part of L1/L2 for ZKR design, which we analyze and study.
Layer-2 Commiter: Collect transactions and construct L2 blocks.
Block Monitor: L2 block status updater.
Prover Network: After the L2 transaction Rollup, the computing network for ZKP proof.
TSS-based Verifier Network: The verifier network will collect proofs from the Prover Network and then submit them to the L1 smart contract.
Tx Monitor / Layer-2 State Monitor / Executor: L1/L2 bridge.
The timing design of ZKR from L2 to L1 is basically the same, and some role naming and division of labor are slightly different:
Committer collects transactions, constructs L2 blocks, Prover Network monitors blocks, calculates proofs for committed state blocks, TSS-based Verifier Network collects proofs, submits proofs to L1 smart contracts, Block Monitor monitors L1 block packaging, Update the L2 block status after confirmation.
image description
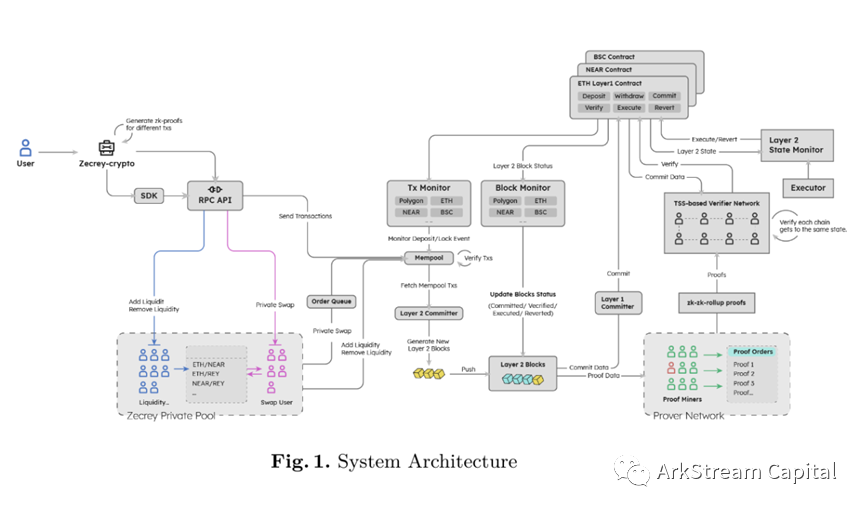
Figure19: Zecrey System Architecture
Manta Network:image description
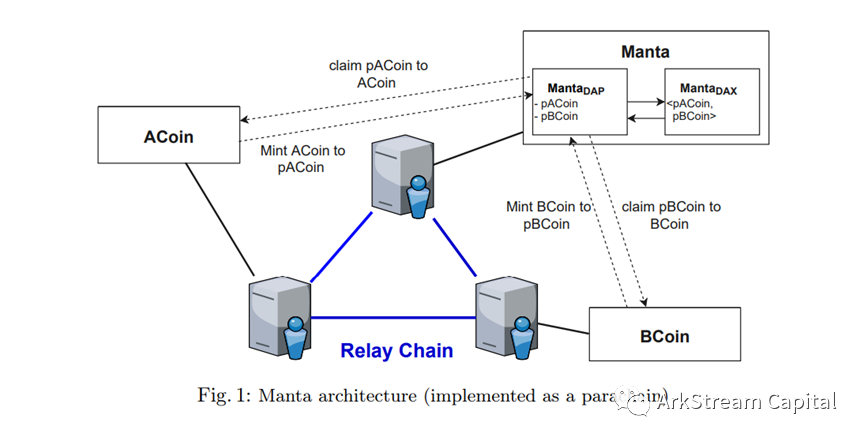
Figure20: Manta Architecture (Implemented as a Parachain)
Anoma Network: Intent (intention)-centered, composable privacy protection, a one-layer network that can decentralize the discovery of counterparties and resolve multi-chain atomic settlement transactions.The Anoma architecture refers to Cosmos, using the Tendermint BFT consensus mechanism, the first sovereign independent chain(Fractal Instance)It's Namada. We use the analogy of an order book to understand Anoma. Anoma's Intent is equivalent to the user's pending order. The pending order can be public (Transparent), hidden (Shielded) or encrypted (Private). The pending order needs to be matched and settled by Anoma's Solver(Settle)image description
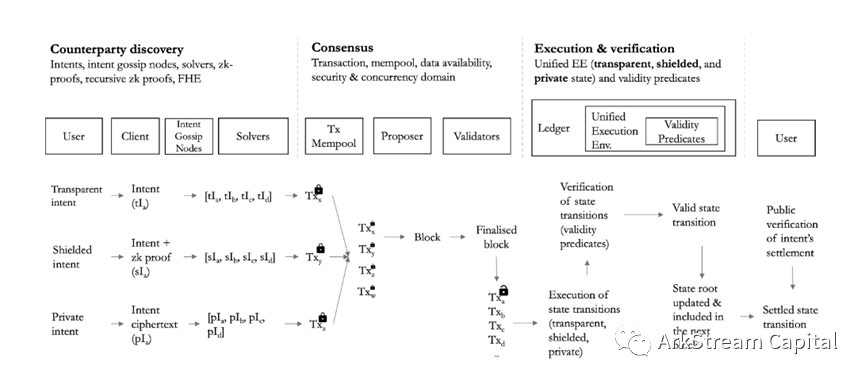
Figure21: The lifecycle of a transparent, shielded, and private intent in the Anoma architecture
Iron Fish:Based on Zcash's Sapling protocol, it uses PoW as a consensus privacy payment public chain. Several rounds of incentive testnets have been carried out, and the mainnet is expected to be launched in Q4 in 2022.
image description

Figure22: Web3 Privacy Ecosystem
There are still many projects in the privacy protection track that are being explored and developed, especially the direction of the ultimate user-oriented privacy application, combined with application scenarios such as DeFi and NFT, there is still a lot of room for expansion, and we will not list them one by one. Back to the original topic, the emergence of privacy products is based on the needs of users. When we move towards Web3, whether it is a decentralized financial system based on blockchain or the social scene of Web3 in the future,We all hope to put more off-chain behaviors on the chain, and the demand for user privacy protection will become stronger.first level title
Investment direction of zero-knowledge proof
image description
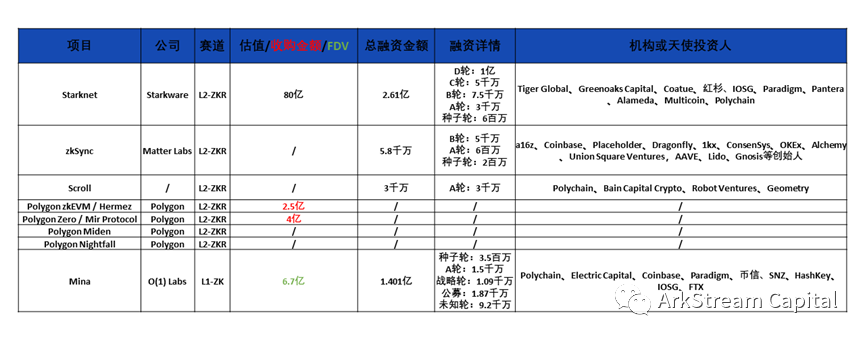
Figure23: Zero Knowledge Investments In Scaling
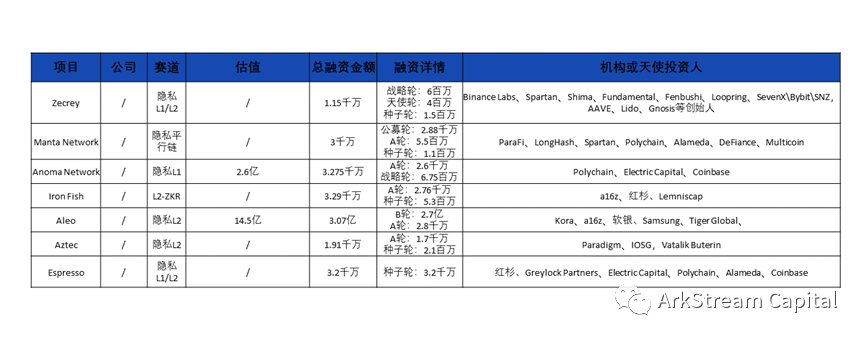
Figure24: Zero Knowledge Investments in Privacy Protection
It can be seen that the ZK expansion project with the highest valuation is Starkware, which is as high as 8 billion, and the ZK privacy project with the highest valuation is Aleo, with a valuation of 1.45 billion. Considering that the privacy and expansion narratives of projects can start in parallel, and even some privacy projects are two-tier networks, it is difficult to compare the average financing amount of the two tracks. From the perspective of the highest valuation alone, the recognition of the expansion track in the primary market is higher than that of the privacy track.Among the expansion tracks, Starkware, which has advantages in protocol, circuit language, zkVM and service items, is undoubtedly the darling of the capital market. In addition, other expansion projects that focus on zkEVM compatibility have also won the love of the capital market. In the privacy track, Aleo, which has advantages in circuit language and developer tool chain, is more popular than Aztec, which develops PLONK and PLookup technologies, which also shows that the capital market is more focused on commercial landing projects.
In terms of the secondary market, due to the large fluctuations in the currency price, the liquidity of ATH is basically insufficient. We simply refer to the range of FDV. The ZKR expansion project has not yet issued coins. We borrowed (ORU) project Optimism for benchmarking. The FDV of OP is 2 billion to 9.5 billion; while in the privacy protection track, ZCash is between 1.5 billion and 4.5 billion, and Oasis is 7 billion. Between 100 million and 5.9 billion, Tornado's FDV has dropped from 3 billion when it was first launched to only 90 million now.It can be seen from this that the secondary market’s recognition of the expansion track project is basically at the same level as the public chain, while the privacy track is relatively conservative.
Since the ZK technology continues to innovate and break through at the level of academic research, and it is also constantly promoted at the level of engineering practice, investment institutions have always been very fond of and enthusiastic about it. Not only that, in addition to the two main tracks mentioned in this article, ZK can also be used in other scenarios, such as lightweight blockchain (Mina), decentralized identity (Polygon ID) and privacy oracle network (Chainlink's Deco) . From many well-known ZK projects, we have observed that these different project development routes and ecological development routes are more or less building a second-tier public chain. Similar to the research and development technology stack of the public chain, the technology stack involved in the ZK project still covers all aspects:Zero-knowledge proof protocol, circuit programming language, language application library/package, language development and debugging tool chain (IDE), zkVM/zkEVM design and implementation, decentralized consensus mechanism, etc.
In the face of expansion and privacy projects using zero-knowledge proofs, we have extracted some simple thinking lists, summarized as follows, for communication and learning with projects.
1. Different zero-knowledge proof protocols have their own advantages and disadvantages. What are the considerations for choosing?
2. Assuming it is a zkVM-type project, how to efficiently and safely design a developer-friendly circuit programming language?
3. Assuming it is a zkVM-type project, how to build a set of developer ecological tool chain products?
4. Assuming it is a zkEVM project, does it support the seamless migration of smart contracts on the EVM chain, and is there any restriction on calls between contracts (combinability)?
5. When ZK calculates Proof, how can FPGA/GPU and other hardware be used for acceleration?
6. In the project, what roles do Prover and Verifier play? Is it centralized control? Will there be any decentralized design changes in the future?
7....consensus mechanism, token economy design, compliance design and other issues
reference link
reference link
https://mirror.xyz/0x8C4d5E90196325FB22Fff37C97D7984a37e51D11/dhOEzNXqotPftpjf2gh7Hz7qZwu3lQRWYmlE_sSe7is
https://docs.starknet.io/docs/intro
https://v2-docs.zksync.io/dev/
https://scroll.mirror.xyz/nDAbJbSIJdQIWqp9kn8J0MVS4s6pYBwHmK7keidQs-k
https://docs.hermez.io/zkEVM/Overview/Overview/
https://mirprotocol.org/blog/Scalability-on-Mir
https://aztec-protocol.gitbook.io/zkproofs-proposal/
https://docsend.com/view/ntcsmt7meu84gcqkZecrey: A Turn-key Solution for Cross-chain and Privacy
https://eprint.iacr.org/2021/743.pdfMANTA: a Plug and Play Private DeFi Stack
https://betterprogramming.pub/understanding-zero-knowledge-proofs-through-the-source-code-of-tornado-cash-41d335c5475f
https://github.com/anoma/whitepaper/blob/main/whitepaper.pdfAnoma: a unified architecture for full-stack decentralized application



