Value discovery and psychoanalysis for DID in the context of DeSoc (Part 2)
Author: Spike, researcher at ThePrimedia
Creating a shared, flexible, and resilient identity layer is imperative: the DID is the backbone through which all digital elements flow. As DID is adopted by more users and Dapps, the processing authority of all digital elements must be in the hands of individual users. Users will not be limited to a single application ecosystem, and users do not need to be trapped in multiple applications. In the mist of individual account and password records; and only on the basis of DID empowerment, Web3 applications such as DeFi, GameFi, NFT and DAO, as well as grand future scenarios such as DeSoc and Metaverse, will bloom more exciting and even are great narratives—a topic to be discussed in the next article.
DID:Decentralized Identity❎
DID:Dissociative Identity Disorder✔️
When we search for the word DID in Google, the first thing that pops up is its medical explanation - "multiple personality disorder", not the concept of decentralized identity that we are familiar with. Compared with concepts such as DeFi, GameFi, NFT, and DAO, DID is an extremely neglected field that has not attracted enough attention from investment institutions and technology developers.
In the context of calling the richer and more diverse ecosystem based on Web 3 a decentralized society (DeSoc), we believe that DID is a key link in building DeSoc—realizing Web 3 native applications. Previously, we had hoped that the unique characteristics of NFT "Non-homogeneous Token" could complete the identity and asset confirmation of users in Web 3. But in fact, some NFT artists and creators are suffering from plagiarism and fraud. Not Web 3.
Creating a shared, flexible, and resilient identity layer is imperative: the DID is the backbone through which all digital elements flow. As DID is adopted by more users and Dapps, the processing authority of all digital elements must be in the hands of individual users. Users will not be limited to a single application ecosystem, and users do not need to be trapped in multiple applications. In the mist of individual account and password records; and only on the basis of DID empowerment, Web3 applications such as DeFi, GameFi, NFT and DAO, as well as grand future scenarios such as DeSoc and Metaverse, will bloom more exciting and even are great narratives—a topic to be discussed in the next article.
first level title
Medium Part: History of DID Development
secondary title
Where It All Started: The First Emergence of the Internet
Web 1.0: World Wide Web WWW and browsers. First of all, we have to admit a basic fact. It is the concept of Web 2.0 that first existed, which gave the World Wide Web this "respectful title" like respecting its ancestors.
secondary title
Web 2.0 and UGC, blogging, iPhone, 5G, XR
Web 2.0 and UGC, blogging, iPhone, 5G, XR
From blogging to Tik Tok, starting from the right of personal expression, going through a continuous decentralization stage, from the initial establishment of elites to universal media, from middle-aged social elites to teenagers accessing the Internet, the Internet has become a priori existence in the Z era, and its status is unquestionable , like water, electricity and coal, has become a ubiquitous infrastructure like air.
Facebook’s reselling of personal data broke out in the 2016 U.S. election, and Cambridge Analytica used the data to “sway” the U.S. election to some extent. There are two prerequisites for this to be possible. The first is that people will leave a large number of digital traces about their privacy on the Internet; the second is that people will leave their personal data on certain applications, such as Facebook, Twitter.
To be clear, the concept of personal data emerged first, and the debate over privacy came second. At this time, IDs are gradually migrating to social tools. This does not mean the demise of mailboxes, but the change of people’s usage habits. It is more appropriate to say that Facebook has also become an optional login tool other than mailboxes. The implicit premise here is Everyone uses Facebook by default.
secondary title
DID under Web 3: a portal
Web 3.0 is the intersection of concepts where the self is still being found. Since the concept was proposed in 2004, it has experienced the transformation of the traditional Internet and gradually got in touch with the blockchain. This connection is not achieved in one step, at least after the era of (public chain) Bitcoin, Ethereum and EOS, trying to replace the WWW World Wide Web with a public chain. At present, this is actually a failure. The so-called parallel chain in the Polkadot era is actually admitting that it is not feasible to unify all chains.
When we talk about the blockchain, the direction of each era is different. From the initial Bitcoin to the later DeFi, NFT, and now to Web 3.0, it does not mean that the latter replaces the former. It is mostly a relationship of gradual superposition and development.
Just as ordinary people don’t need to understand the TCP/IP protocol, compiling principles, and computer composition principles to use devices to access the Internet, we don’t know which ones will become the final components and which ones will be eventually discarded during the technology incubation stage of building Web 3.0. Become the wheel of history to run over the floating dust. But human beings will eventually advance and grow towards the digital age in the process of using Web 3.0, so we will now firmly believe in the importance of DID-there will always be an entrance, and it will not be an entrance.
In Satoshi Nakamoto's vision, it is better for people to use one address for each transaction, which can ensure privacy to the greatest extent. But in fact, except for hackers and people who forget the mnemonic, no one will do this every day. This is really too anti-human logic-we are used to using a single address for a long time, rather than using a single address every time; more importantly What's more, the development of blockchain has surpassed Satoshi Nakamoto's "blockchain".
But in the coordination of interactivity and decentralization, the number must be limited. This is similar to social tools, real infrastructure will form a strong user stickiness, especially the aforementioned importance of the value and meaning carried by an identity in the decentralized world.
text
L1: Identifiers and Standards
Standards, identities, and namespaces (namespces) work together to build a common layer of trust that ensures standardization, portability, and interoperability.
image description
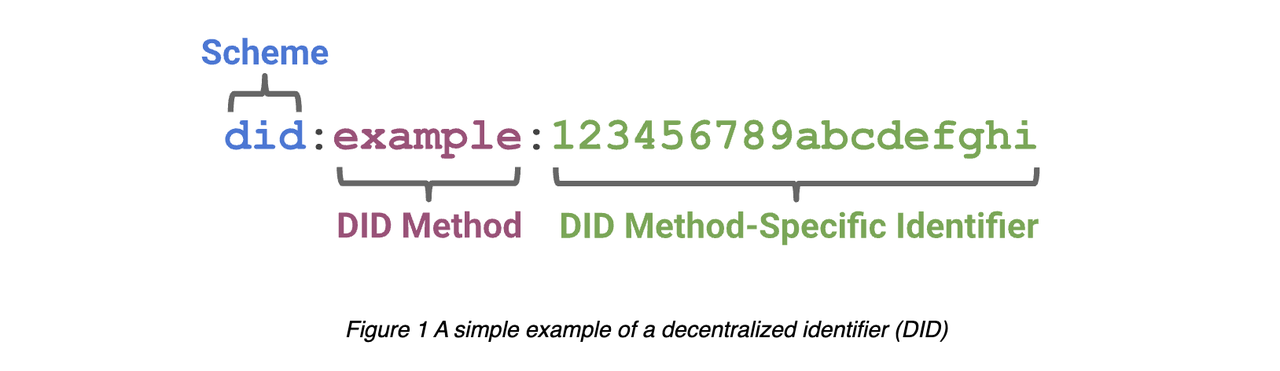
Source: W3C
The most typical here is the DID standard drafted by W3C, which can be traced back to 2019. The draft document stipulates that "each DID document can represent encryption material, authentication method or service endpoint (service endpoint). These documents provide a The group enables the DID controller (DID controller) to prove the system controlled by the DID. And, the service endpoint realizes the trusted interaction with the DID."
text
L2: Infrastructure
After realizing the importance of DID, we began to explore how to design DID, but one thing is certain, DID will become a basic construction, closer to the underlying concept of API or SDK.
This is because, as an infrastructure and proxy framework, DID can allow two-way or even multilateral interaction between applications, and even DID can interact with each other, interconnected, and open up data and information from the protocol level. It can also make applications Interact directly with a verifiable data registry.
DID under this concept must at least include communication, storage, and key management. If it goes further, it can "de-encrypt" while retaining login and authentication functions.
image description
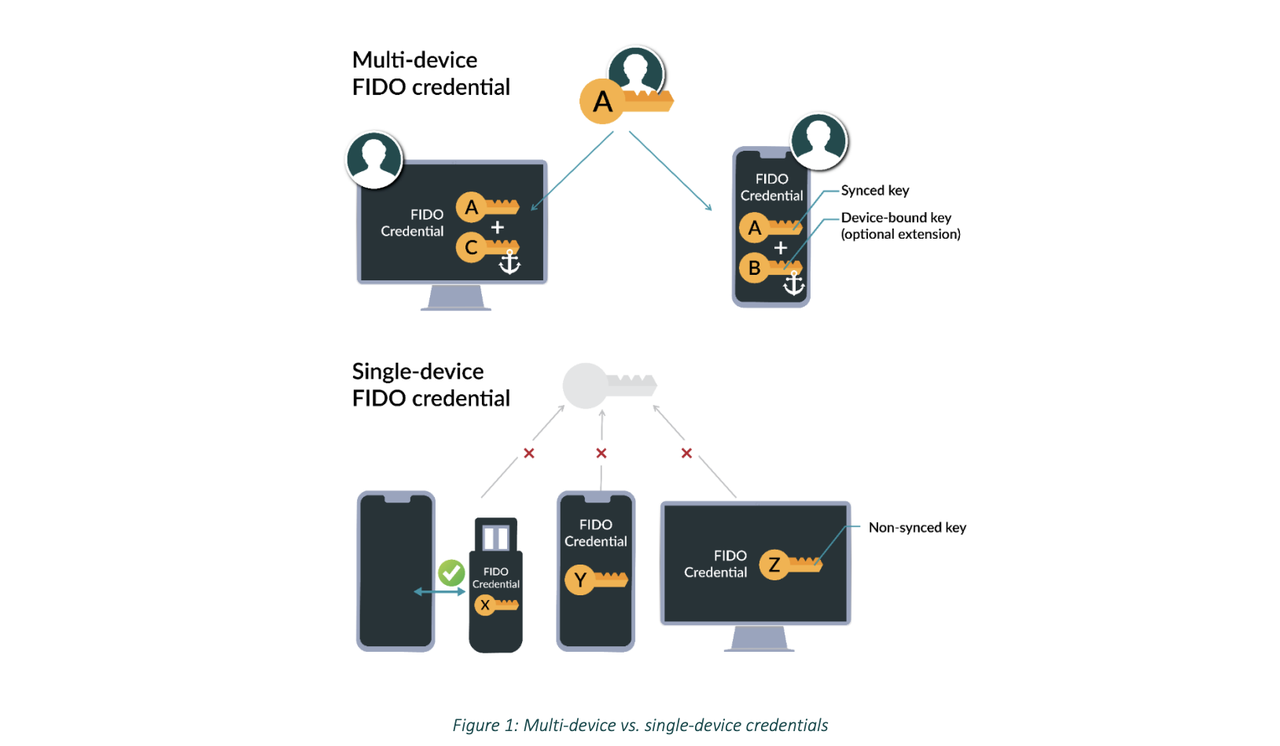
Source: FIDO
For example, FIDO, Apple also officially began to support this concept at WWDC 2022, we briefly introduce the steps to use it:
1. Use your phone as a roaming authenticator Using your phone as a roaming authenticator
2. Multi-device FIDO credential
Theoretically, FIDO can also be used in the future Web 3.0 network. This kind of encryption technology with one-time authentication, password abandonment, and multi-device transfer is very suitable as the future network infrastructure.
L3: Credentials
After all, FIDO is a product thinking in the Web 2 era, and does not necessarily fully meet the needs of the Web 3.0 era. We need to manage and update identity credentials, and they need to be interchangeable - this layer aims to solve how DID determines the "proof of control" and "proof of authentication" ( proof of authentication), and how to securely pass data between identity owners.
In fact, some explorers are already trying this concept, such as DAS (Decentralized Account Systems), a decentralized account system that does not depend on a specific public chain and supports multi-public chain and multi-protocol interaction.
image description
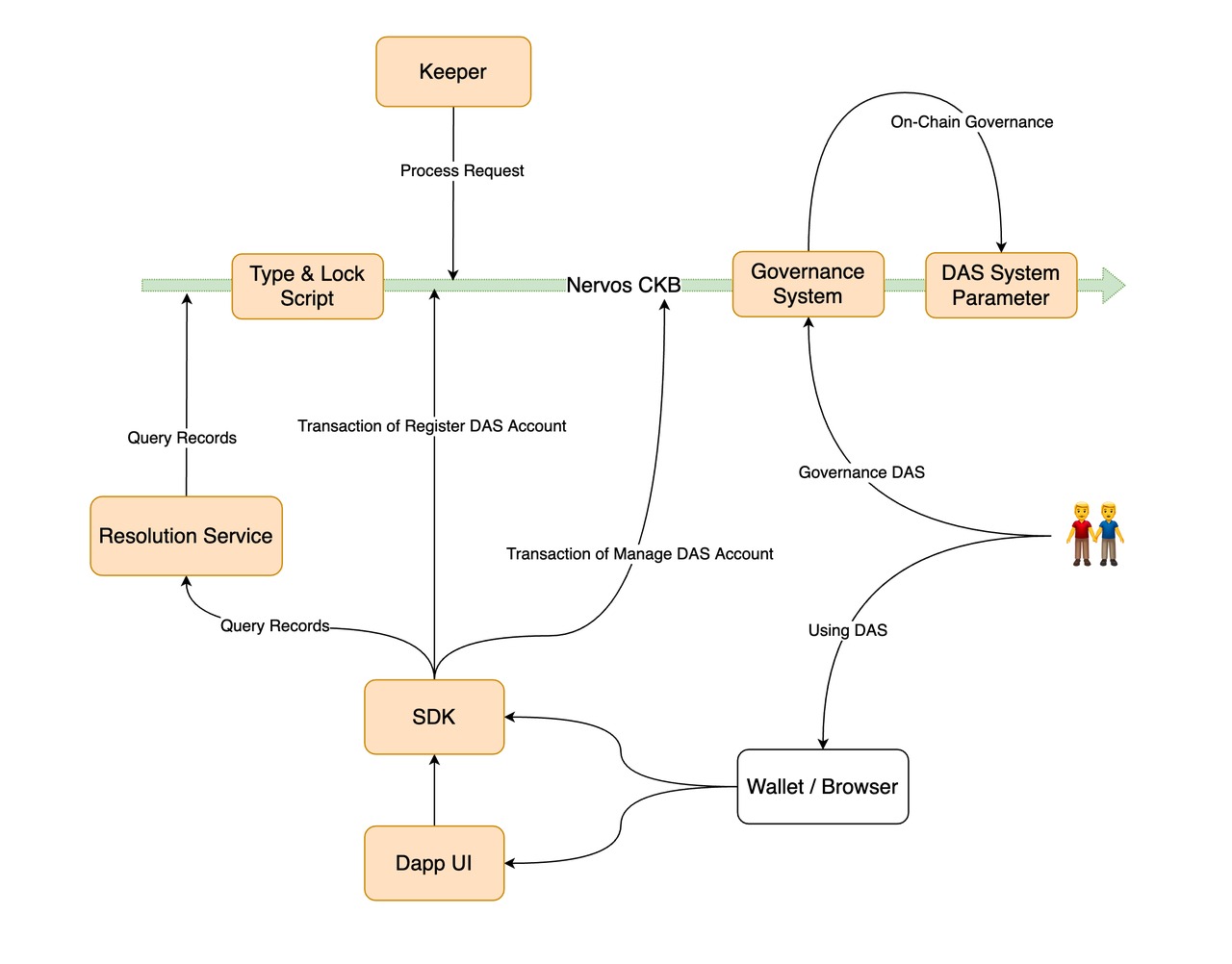
Source: DAS
But there will be a problem, is this a DID, or what is the difference between this and a wallet? You should know that although the wallet address is difficult to remember, the Dapp login and interaction in the wallet are very smooth. Therefore, this can be used as a reference for ideas, but it is difficult to become mainstream.
L4: Wallets and Dapps
image description
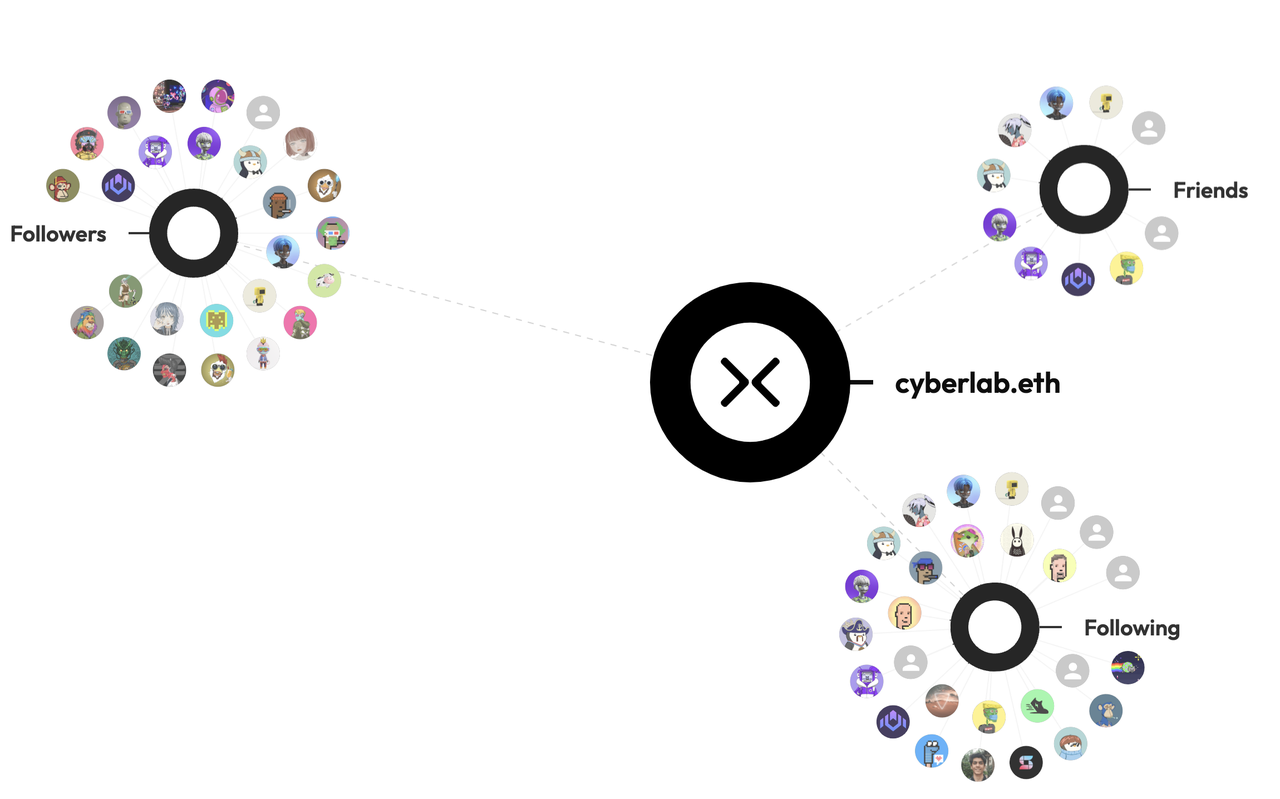
Source: CyberConnect
A more feasible idea is CyberConnect, which is well-known. This is a development idea similar to WalletConnect for wallets. "What if I can't beat MetaMask, but there are other wallets at the same time?" Very simple, gather them at the protocol level Together, Dapp developers only need to reserve development time for MetaMask and WalletConnect.
CyberConnect is exactly this way of thinking, "I don't know what social products people will use in the future Web 3.0 era, and what they will do on the Internet, but in short, they need such a protocol."
In this way, it will become a DID + aggregator to form the social graph information of a certain address, and these information come from the data on the chain and finally become a more advanced aggregator, while avoiding competition with specific Dapps, for example, We can use address and ENS to retrieve a person's information, and we can also check our own situation.
Is that all there is to it?
secondary title
LX:DID for DeSoc
Going beyond the scope of a single layer and having an impact on applications on multiple layers may be a direction worth looking forward to in the future. A current reference is Europe's GDPR General Data Protection Regulation, which affects all areas of the ecosystem.
In the field of Web 3.0, the more intuitive may be "soul binding", and DID will be its direct instance. Regarding this part, ThePrimedia will elaborate in the next part, so please look forward to "Part 2: Another Attempt to Find Yourself".



