深度解读零知识证明技术:点亮DeFi的新星
零知识证明技术:点亮 DeFi 的新星
原文作者:LZ
一、引言
去中心化金融(Decentralized Finance,简称 DeFi)是当前金融创新领域的重要发展方向。在 DeFi 中,对交易信息的隐藏和用户隐私的维护是至关重要的。随着 DeFi 的不断扩展和深化,各类项目层出不穷,充满了活力。而零知识证明(Zero-knowledge proof,简称 ZK)技术的应用,为 DeFi 的隐私保护开辟了新的可能。ZK 技术使得一方可以向另一方证明他们知道某个信息,而无需透露任何关于该信息的具体细节。这种技术在诸如ZigZag、unyfy以及 OKX 的ZK DEX等 DeFi 项目中的应用,极大地强化了 DeFi 的隐私保护能力,尤其是对于交易信息的保护。可以预见,ZK 技术的广泛应用将带来对 DeFi 以及整个加密货币领域处理方式的革新,推动整个领域的未来发展,实现重大突破。
二、DeFi 中的隐私挑战
区块链上没有秘密,DeFi 的数据透明度也是无可争议的。以 Uniswap V3上的某一笔交易为例,我们可以通过 Etherescan 网站轻松查看该交易详情(如图 1 所示)。例如,地址 0 x 3A 4 D...a 6 f 2 在 Uniswap V3上用 2 WETH 兑换了 17, 654, 123, 249, 375 Bonk,交易费用为 0.0046 Ether。这些交易中的发送者(From)、接收者(To)、交易金额(Value)以及手续费(Transaction Fee)等关键信息都是公开可查的。
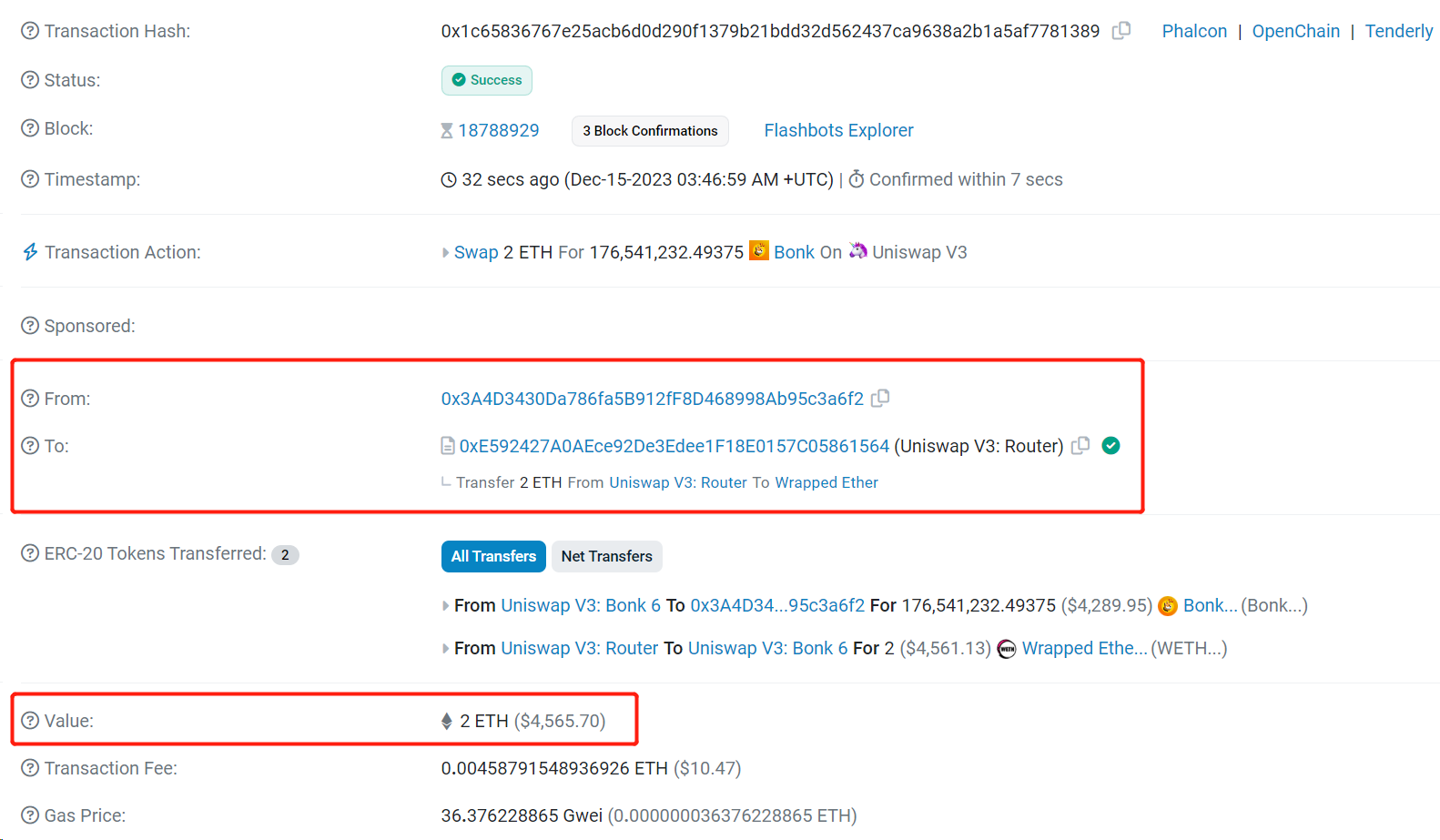
图 1 在 etherescan 上公开的交易细节
我们还可以查看 0 x 3A 4 D...a 6 f 2 地址下的所有交易记录(如图 2 所示),如果条件允许,还可以推测出此地址在现实世界中的真实身份。
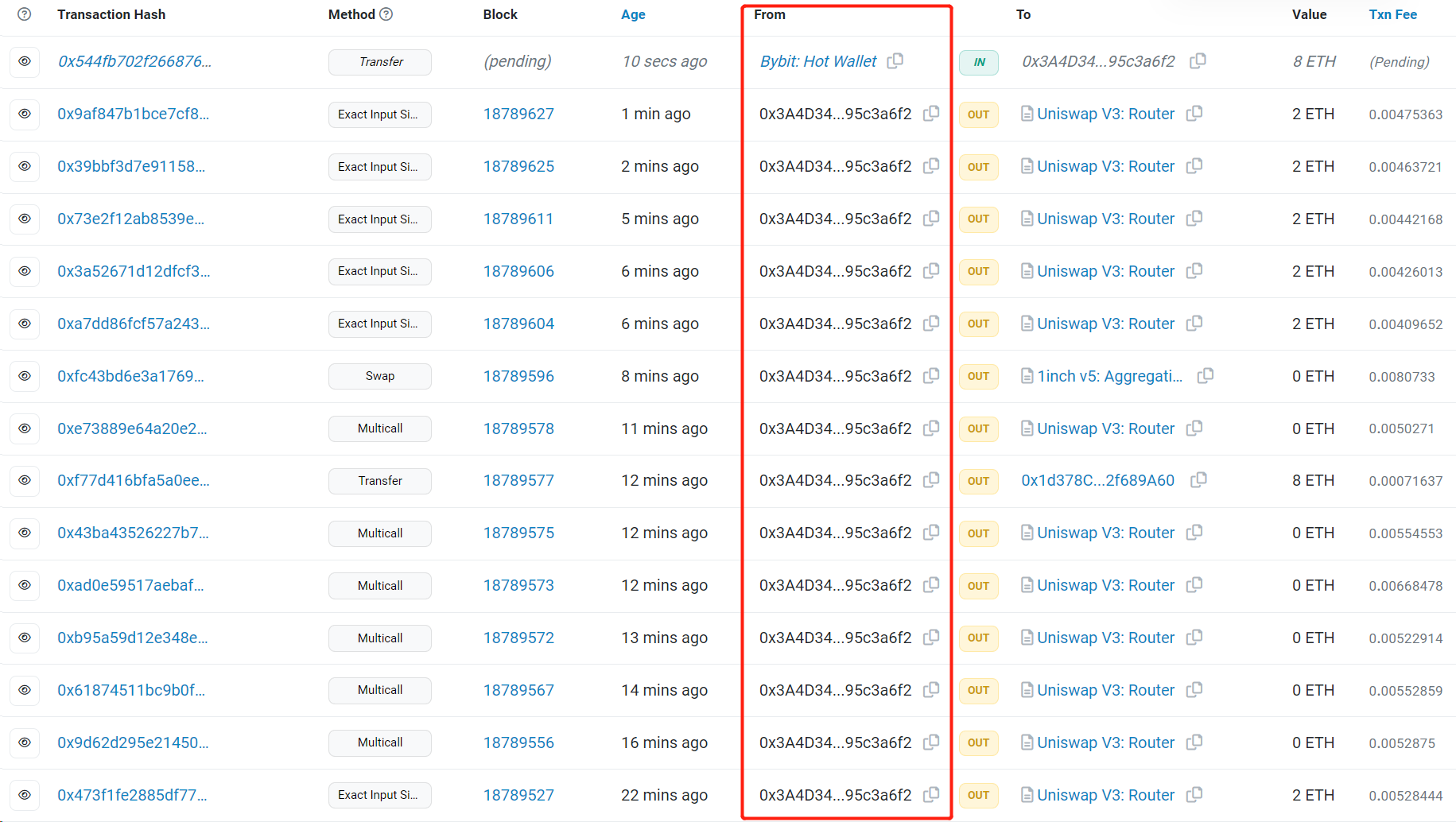
图 2 特定地址的所有交易列表在 etherescan 上是公开的
然而,DeFi 的数据透明度可能会带来一些不利影响。如果你是一个 DeFi 巨鲸,你的每一笔交易都可能会引起市场的关注,比如,当某巨鲸从币安提取1124 万枚 WOO(约合 420 万美元),这笔交易就会引起广泛关注。同样,任何大额支付或机构级的交易行为,也可能引发公众的广泛关注。
市场的其他参与者可能会根据这些交易行为作出买卖决策,从而对你的投资策略产生不利影响。比如,你在某个项目中投入了大量资金,但一旦你的交易被市场察觉,其他投资者可能会紧随其后,导致资产价格上涨,进而增加你的投资成本。此外,你的售出操作也可能引发市场恐慌,导致价格下跌,影响你的投资回报。
这种情况突显了 DeFi 项目和用户对隐私保护的迫切需求。如果我们不希望自己的交易细节被公众知晓,可以选择让 DeFi 交易的某些信息保持私密。
ZK 技术在隐藏交易细节的同时,能确保交易的合法性。用户需要提交两类信息:一是部分隐藏细节(如交易接收方或金额)的交易(即隐私交易),二是关于这些隐藏信息的 ZK 证明。验证一个隐私交易的合法性,实际上是在验证相应的 ZK 证明。
三、解锁 DeFi 潜力:ZK 技术带来的机遇
3.1 ZK 技术在抵御抢跑交易中的作用
假设你有幸得知一家大公司即将购买大量的某种资产,你可能会选择先于这家公司购入这种资产。然后,当这家公司的大量购买行为推高了资产价格后,你再将其卖出,从而获取利润。在这种情况下,你先于大公司进行的交易就构成了抢跑交易。
抢跑交易是一种在金融交易中的投资策略,通常发生在交易所中,比如 Uniswap。这是因为在区块链中的交易是公开的,而且交易确认需要一定的时间。因此,一些恶意的交易者可能会通过提高交易 Gas 费用,让自己的交易优先于其他人的交易被挖矿确认,以此来达到抢跑交易的目的。
抢跑交易会给其他的交易者造成损害,因为它改变了原本的交易环境,使得其他交易者的交易可能无法按照原计划进行。另一方面,攻击者发起抢跑交易的目的也是为自己牟利,他们可以在价格变动前获取利润。因此,很多 DeFi 项目也在尝试通过各种方式来防止抢跑交易的发生。
ZK 技术在抵御抢跑交易中可以发挥关键作用。以下,以去中心化交易所(Decentralized Exchange,简称 DEX)中的三明治攻击为例,这也是一种常见的抢跑交易类型,进行案例分析。
3.1.1 案例分析:DEXs 中的三明治攻击
什么是三明治攻击?
假设在一个 DEX 上,有一个流动性池,其储备状态为 100 ETH / 300, 000 USDT。Alice 发起了一笔购买 USDT 的交易,即以 20 ETH 交换 USDT。当她提交交易时,DEX 会根据当前流动性池的储备状态返回一个结果,告诉 Alice 可以买到大约 50, 000 USDT。但实际上 Alice 最后只拿到了 45, 714 USDT。
这里,我们先来简单了解一下为什么 Alice 能够用 20 ETH 购买到 50, 000 USDT。该 DEX 采用了自动做市商模式(Automated Market Maker,简称 AMM),通过恒定乘积做市商算法(Constant Product Market Maker,简称 CPMM)自动计算买卖价格。CPMM 是目前普及度较高的自动做市商算法,通过保持交易池中两种资产乘积的恒定,以实现流动性供应并自动调整资产价格。在这个例子中,通过公式 50, 000 = 300, 000-( 100* 300, 000)/( 100+ 20)(假设没有手续费)计算出 Alice 能够买到的 USDT 的数量。
Alice 并没有买到预期数量的 USDT,这是因为她遭到了三明治攻击。
三明治攻击主要发生在基于 AMM 的 DEXs 中。在三明治攻击中,攻击者在受害者的常规交易周围放置两笔交易以操纵资产价格并从受害者的损失中获利。这两笔交易分别是抢先交易和追单交易,常规交易之前的交易被称为抢先交易,常规交易之后的交易被称为追单交易。
那么,Alice 遭到的三明治攻击到底是如何进行的呢?如图 3 所示。
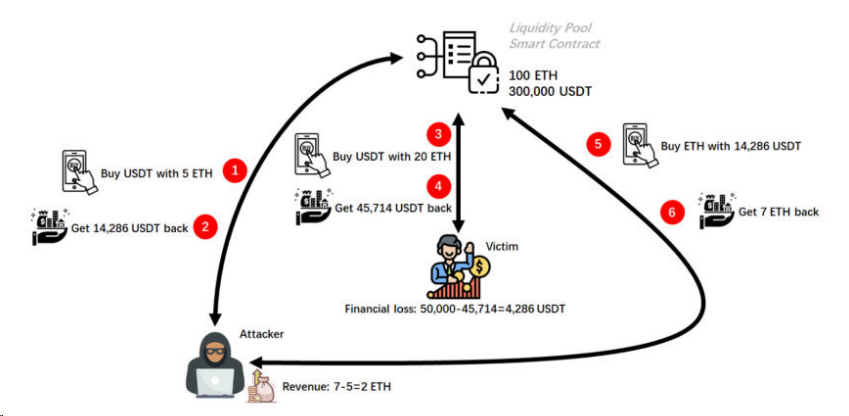
图 3 三明治攻击流程
1. 攻击者的抢先交易:在 Alice 发起的购买 USDT 的交易被执行之前,攻击者也发起了一笔购买 USDT 的交易(抢先交易),即以 5 ETH 交换 USDT。而且,攻击者为这笔交易支付给矿工的 gas 费高于 Alice,所以,攻击者的这笔交易会先于 Alice 被执行。
2. 攻击者购买 USDT 的交易执行后,他从流动性池中拿到了大约 14, 286 USDT, 14, 286 ≈ 300, 000-( 100* 300, 000)/( 100+ 5)。流动性池的储备从初始状态的 100 ETH / 300, 000 USDT 变为 105 ETH / 285, 714 USDT。但是,Alice 在提交交易到她的交易被执行这段时间内,并不知道流动性池的储备状态发生了改变。
3. 受害者的常规交易:随后,Alice 的常规交易开始执行。
4. Alice 购买 USDT 的交易被执行后,她从流动性池中拿到了 45, 714 USDT(根据恒定乘积函数, 45, 714 ≈ 285, 714-( 105* 285, 714)/( 105+ 20))。流动性的储备状态从 105 ETH / 285, 714 USDT 变为 125 ETH / 240, 000 USDT。所以,Alice 用 20 ETH 本应该能买 50, 000 USDT,现在却因为攻击者的交易使流动性池发生的改变,只能买 45, 714 USDT。Alice 亏损了大约 4286 USDT(4286 = 50, 000-45, 714 )。
5. 攻击者的追单交易:最后,攻击者再次发起一笔交易(追单交易),即以 14, 286 USDT 交换 ETH(这 14, 286 USDT 是刚才买的)。
6. 攻击者的追单交易被执行后,他从流动性池拿出了 7 ETH(定乘积函数, 7 ≈ 125-( 125* 240, 000)/( 240, 000+ 14, 286))。流动性池的储备状态从 125 ETH / 240, 000 USDT 变为 118 ETH / 254, 286 USDT。所以,攻击者一开始只是花费了 5 ETH,最后却拿到了 7 ETH,获得了 2 ETH 的收益(2 = 7-5)。
在整个三明治攻击的流程中,攻击者总共发起了两笔交易,即抢先交易和追单交易。抢先交易使 Alice 亏损了大约 4286 USDT。抢先交易和追单交易的组合,使攻击者盈利了 2 ETH。
在 DEXs 中,交易的公开性是导致三明治攻击出现的一个关键因素,尤其是在 AMM 协议中。这些协议将 DEXs 上的实时交易信息公之于众,这种高透明度为攻击者提供了可能,他们可以通过观察和分析交易流动,以便找寻机会进行三明治攻击。
3.1.2 ZK 技术可以抵抗三明治攻击
ZK 技术的应用可以显著减少受到三明治攻击的可能性。通过使用 ZK 技术隐藏交易量、资产种类、用户或流动性池余额、用户身份、交易指令及其他协议相关信息,可以有效提升交易数据的隐私性。这样一来,攻击者难以获得完整的交易信息,从而使得三明治攻击的实施更加困难。
此外,ZK 技术不只能抵御三明治攻击,基于 ZK 的隐私交易还能增加对用户行为模型判断的难度。任何第三方尝试通过收集区块链数据来分析账户历史交易、推断行为模式、探寻活跃周期、交易频率或偏好等,都将面临挑战。这种分析被称为行为模型推断,不仅侵犯用户隐私,还可能为蜜罐攻击和网络钓鱼诈骗铺平道路。
3.2 基于 ZK 技术防止流动性操纵
流动性操纵和抢跑交易都是 DeFi 中的攻击方式,这两种攻击方式都涉及到利用市场信息和交易速度来获取利益,但是它们的具体策略和操作方式是不同的。
抢跑交易是利用信息优势,而流动性操纵是利用市场活动来误导其他交易者。前者主要通过获取并利用未公开的重要信息来获利,而后者则是通过创造虚假的市场活跃度来误导其他投资者,使他们做出不利的交易决策。
ZK 技术不仅可以在抵御抢跑交易中发挥关键作用,它也可以助力于防止流动性操纵。
3.2.1 案例分析:利用预言机进行流动性操纵
假设你正在一个繁忙的水果市场购买苹果。市场的价格通常会根据供应和需求的变化而浮动。你通常会观察一段时间的价格,然后根据平均价格来决定是否购买。现在想象有一个非常富有的买家进入市场,并且他非常想要购买苹果。他开始大量购买苹果,不在乎价格如何。这会导致苹果的价格短时间内暴涨。如果你仍然根据这个价格购买苹果,你就可能会付出比实际价值更高的价格。
这个例子可以更好地理解 TWAP(Time-Weighted Average Price,时间加权平均价格)预言机的工作原理和流动性操纵的概念。根据平均价格决定购买苹果的行为类似于 TWAP 预言机的操作,富商大量购买苹果导致价格上涨则类似于流动性操纵。
TWAP 预言机通过计算一段时间内的平均交易价格确定资产价格。交易的时间越近,对平均价格的影响越大。如果有人短期内进行大量交易或用大量资金交易,可能大幅影响资产的平均价格,这就是流动性操纵。流动性操纵会人为抬高或压低资产价格,导致价格信息不准确。如果有人想利用 TWAP 预言机故意提高资产价格,他可以短期内用大量资金购买该资产,使价格短暂上涨。如果在这个时间窗口内,资产价格出现了显著的增加,TWAP 预言机可能会将这个较高的价格视为资产价格。
对 TWAP 预言机实施流动性操纵会对 DeFi 协议产生重大影响,尤其是流动性较低的新兴代币。这些 DeFi 协议通常会根据资产的价格来做出财务决策,比如清算、借贷等。如果价格信息不准确或不可靠,就可能导致错误的决策,从而给用户带来损失。因此,防止 TWAP 预言机受到流动性操纵是至关重要的。
3.2.2 ZK 技术可以抵抗流动性操纵
基于 ZK 技术可以抵抗 TWAP 预言机当中的流动性操纵。可以设计一个智能合约,使其依赖于 TWAP 预言机来获取资产价格。如果攻击者进行了流动性操纵行为,从 TWAP 预言机获取的价格可能会超出预设的可接受范围。在这种情况下,该合约将会暂时停止其操作。然后,它将基于 ZK 技术重新计算并确认资产价格。
要想使用 ZK 技术计算资产价格,首先需要向 TWAP 预言机添加一个包装合约(wrapper contract)。该合约可以直接访问 N 个价格报告,或者记录价格在任意间隔的 N 个检查点值。一旦给定间隔内有 N 个数据点可用,就可以构建 ZK 证明来证明未排序价格数组的中位数(the median of the unsorted array of prices)。未排序价格数组被标记为列向量 x,长度是 N。以下是基于 ZK 技术计算资产价格的过程:
1. 证明可以用以下两种方式中的任一种进行验证,无论哪种情况,证明者都不能任意选择一个价格数组作为输入。
从合约存储中检索数组值,并将其作为公开输入用于链上验证器;
通过哈希函数逐步形成哈希链,将数组表示为单个哈希值,并在链上验证器中使用该值。
2. 存在一个 N x N 的矩阵 A(square matrix),当该矩阵乘以列向量 x 时,产生列向量 y,使得。A 是一个可逆的排列矩阵,但由于可能存在重复的价格值,A 并不一定是唯一的,且 A 只包含二进制值。
3. y 中的值是有序的,即。再次说明,不能使用<,因为可能存在重复的价格值。
4. 电路的公开输出 m 是 y 的中值(median vaue)。证明显示,其中 N 是电路编译时的静态值,必须为奇数。
根据以上过程,基于 ZK 技术输出了一个价格的中值 m,该值是防篡改的。中值 m 可以在一定程度上防止流动性操纵,为了实现这一点,我们需要限制 y 的值,使得在每个区块中,y 的值只被插入一次,或者被插入的次数在可接受的范围内。
3.3 ZK 技术为借贷平台赋能
如上所述,ZK 技术能够抵御 DEXs 中的抢跑交易和流动性操纵。那么,我们是否可以进一步探究 ZK 技术在其他 DeFi 场景中的应用可能性呢?例如,在 DeFi 项目的重要组成部分——借贷,ZK 技术也能发挥出关键的作用。
3.3.1 借贷的关键:如何评估借款人信用
在传统借贷平台上,贷款申请流程通常涵盖申请、信用评估、贷款审批、贷款发放及偿还等五个步骤。其中,信用评估的环节尤为重要,借款人必须证明其收入达标,并且具备还款能力。在评估过程中,平台会深入调查借款人的信用历史,包括收入、负债以及过去的还款记录等,以确保其有能力偿还贷款。只有在此基础上,平台才会考虑批准贷款申请。
然而,当你转向去 DeFi 借贷平台,如 Aave 或 Compound,情况就会有所不同。大多数 DeFi 借贷平台由于其去中心化的特性,没有传统银行的 KYC(Know Your Customer,了解你的客户)程序和风险评估环节,也无法通过联合征信社来调查借款人的信用状况。在这种情况下,你可能会疑惑,我的信用将如何进行评估呢?
在 DeFi 借贷平台上,你可以通过声誉代币证明来证明自己的信用水平。声誉代币是一种以区块链技术为基础的信用体系,通过数字代币来表征和量化用户的信誉。声誉代币的数量成为评估用户信誉的重要指标,代币数量越多,意味着用户的声誉越好,信用等级也相应提高,从而在 DeFi 借贷平台上有可能获得更多的贷款额度。
然而,声誉代币的生成需要依赖用户的交易历史和财务信息,这可能会侵犯用户的隐私权。
3.3.2 评估借款人信用:基于 ZK 技术的信誉代币
ZK 技术可以保护用户隐私。ZK 技术和声誉代币的结合,能够在保护用户隐私的同时,维护和跟踪其在网络中的声誉。
用户可以借助 ZK 技术,在不公开历史交易的情况下,生成信誉代币。一方面,用户可以基于 ZK 技术来生成历史交易的证明;另一方面,由智能合约(通常被称为信誉代币生成合约)对该证明进行验证,验证通过即可生成信誉代币。
此外,在某些需要超额抵押的 DeFi 借贷平台上,声誉代币可以降低抵押要求,从而解决过度担保的问题,提高市场的流动性。且基于 ZK 技术的声誉代币的应用并不仅限于 DeFi 借贷平台,它还可以广泛应用于保险、医疗补助等领域。
四、总结与展望
本文探讨了 ZK 技术在 DeFi 中实现隐私保护的多种应用场景,特别是在抵御抢跑交易、流动性操纵和借贷方面的潜力。在探索 DeFi 的过程中,我们面临着多项挑战,特别是与隐私和安全相关的问题。DeFi 生态系统中的隐私挑战是一个关键议题,而 ZK 技术提供了独特的解决方案,不仅能增强隐私保护,还能提高交易效率和安全性。如果您想要为自己的 DApp 引入 ZK 技术,欢迎与Salus联系。
展望未来,ZK 技术可能会在更深入的 DeFi 领域得到应用,如流动性质押、衍生品协议、真实世界资产、保险等。Salus 专注于研究和探索 ZK 技术在 DeFi 以及其他以太坊应用层项目的应用。我们诚邀全球的区块链研究者、技术开发者以及web3领域的所有专业人士,与我们共同努力,推动 ZK 技术的深度发展和广泛应用,以带动 DeFi 乃至整个行业的发展。



