Trusta Labs发起清白自证计划:抗击女巫投毒
最近 Connext 猎巫计划引起了社区的不满和热烈讨论,个别社区成员扬言要用 Connext 女巫地址投毒,尤其是 zkSync 上交易量前 10% 的地址。虽然多为口嗨,但现实中有用户表示自己被投毒了。链上数据分析和安全平台 Trusta Labs 讨论了女巫投毒攻击的两种主要策略,强制聚类和标签传播策略,并详细分析了一个在 Polygon 上发生的 Connext 真实女巫投毒案例。
这类投毒行为可能使许多无辜的地址被错误的标记为女巫,会伤害到用户和整个社区,也会影响社区与项目方之间的信任。因此 Trusta Labs 发起了 “ Proof of Innocence Program”(PoIP),跟社区和项目方联合起来对抗投毒,让被投毒地址证明自己的清白。在 PoIP 计划中,用户提交相关信息由 Trusta 结合手工和 AI 分析验证,用户在 1 天内获得反馈。这些数据将分享给项目方和反女巫团队,以防止女巫识别误杀行为,更好的保护用户。
Connext 猎巫计划与女巫投毒
Connext 是一个L2开放协议,使开发者能够构建可在任何链上使用任何代币的应用程序。上周 Connext 更新空投规则并宣布了女巫猎人计划,引起了社区的不满和热烈讨论,个别社区成员扬言要用 Connext 女巫地址投毒,尤其是 zkSync 上交易量前 10% 的地址。让我们先来概述一下 Connext 空投的时间表:
1. 8 月 18 日,Connext 宣布对其 xERC 20 $NEXT 代币进行跨链空投。
2. 8 月 24 日,Connext 像 HOP 和 SAFE 一样推出了社区举报女巫计划。
3. 从 8 月 24 日到 9 月 1 日,社区成员识别并举报了女巫攻击者,在 Github 提交举报报告。
4. 截至 9 月 1 日,该社区举报女巫计划从 62, 070 个候选地址中收集了约 600 份报告,涉及约 20 K 个地址(35% )(https://github.com/connext/community-sybil-reports/issues)。
虽然选择和奖励有价值的真实用户的初衷是好的,但我们看到社区内对女巫举报计划存在很多争议。其中“投毒”成为了一个热门话题,有一些被举报的女巫地址用户威胁要给其他钱包地址下毒,他们的目的是要搅乱整个女巫举报工作和空投计划,并且有 KOL 展示了利用机器人进行投毒的短视频,不过事后证明只是为了进行嘲讽,虽然这些投毒多为口嗨,但现实中有用户表示自己确实被投毒了。
女巫投毒策略讨论
Trusta Labs 根据链上数据分析和安全风控经验,分析讨论出女巫投毒攻击的两种主要手法和策略:强制聚类和标签传播,并且发现了真实的投毒案例。
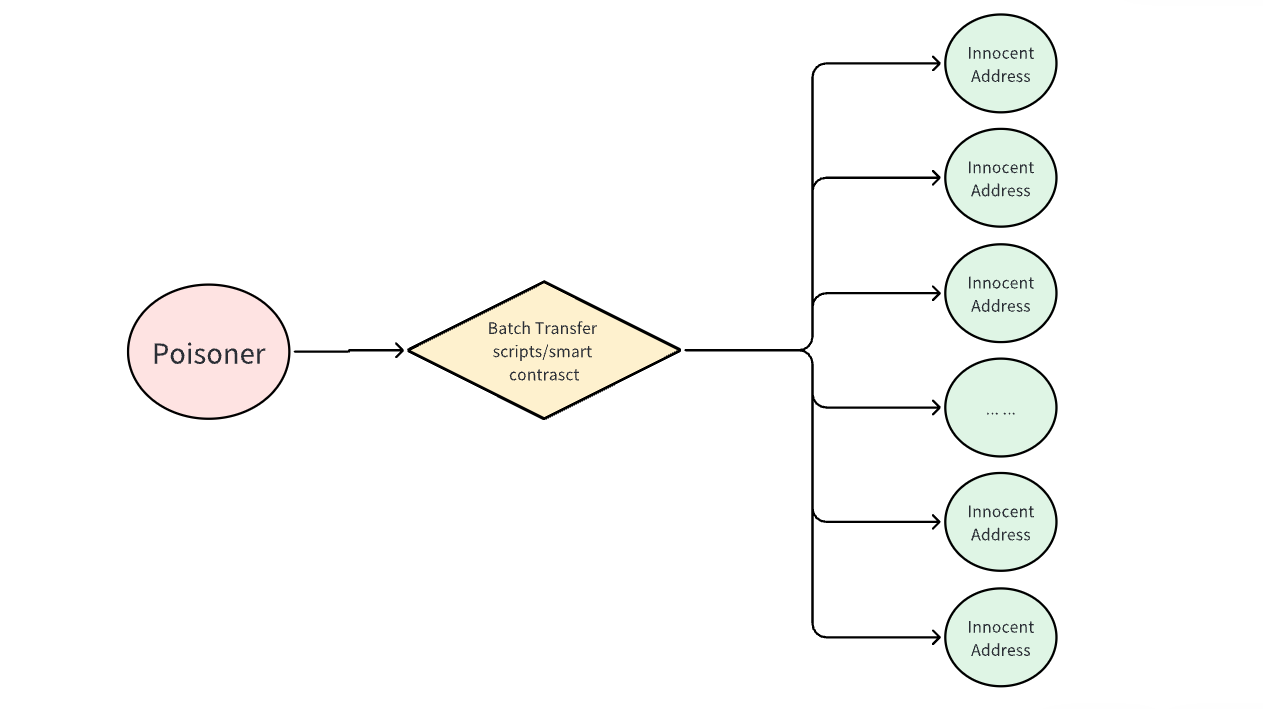
投毒手法 I(强制关联/聚类): 投毒者使用批量操作脚本或 disperse.app 等工具进行批量 Token 转账。他们会在很短的时间内向一组无辜的地址进行许多小额转账。所有伪造的转账都是以极小的金额发送相同的 Token。
通过投毒者的大量 Token 转账,所有不相关的地址都被强行关联到一起,形成一个聚类,由于投毒的地址有批量的转账关系并属于一个聚类,一些女巫识别算法会把聚类中的所有地址标识为女巫地址。这种强制聚类完全是基于这些地址与投毒地址有批量转账关系,尽管这些地址实际上互不关联。
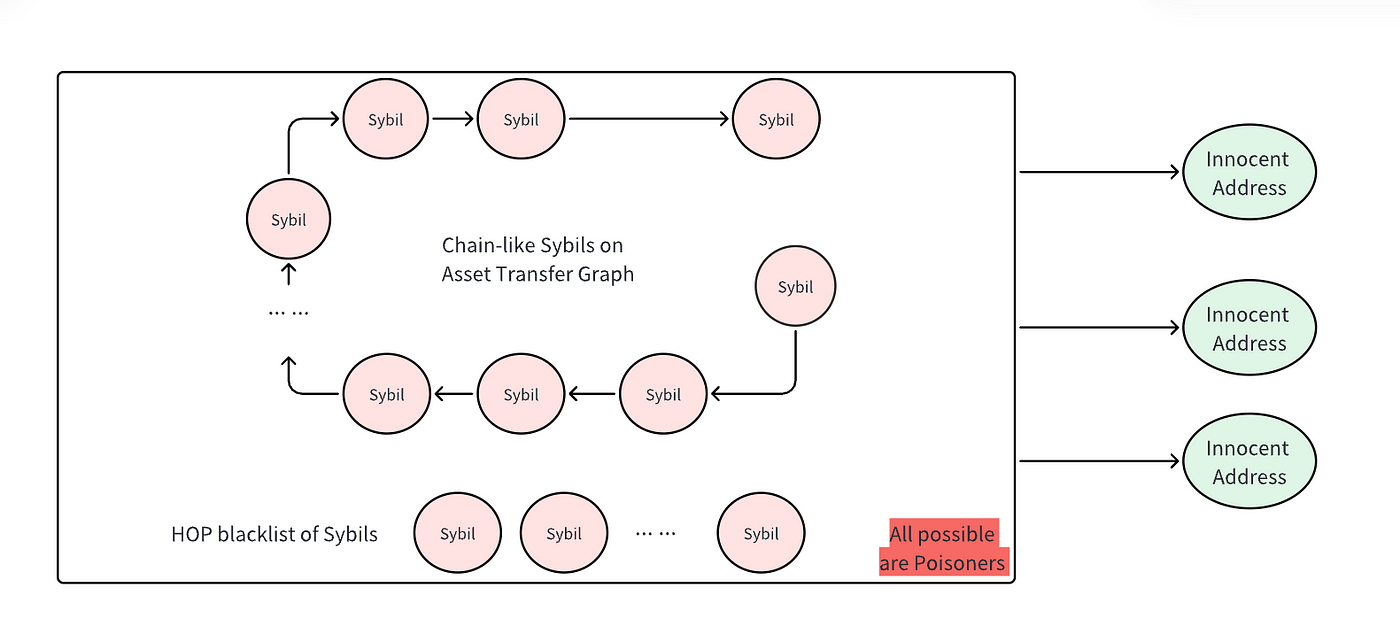
投毒手法 II(女巫标签传播): 标签传播是一种图挖掘算法,它基于图中紧密相连的节点往往具有相同标签的规则。在图中,方框中的地址由于具有链式资金转账关系已经被标记为女巫地址,攻击者可以利用这些女巫地址作为 “投毒者”地址,故意向无辜地址进行转账,形成拓展的链式结构,从而将女巫标签传播给其他无辜地址。
女巫标签传播依靠现有的女巫地址通过资金转账关系将其标签传播到其他地址。这就要求投毒者自身必须是已经被标记为女巫标签。相比之下,强制关联不需要预先存在的女巫地址。任何地址都可以用作投毒者,人为制造虚假的女巫地址批量行为模式。这样,执行起来就更容易,成本也更低。
Trusta 在对链上数据分析的过程中,发现了一个在 Polygon 上 Connext 投毒案例,通过对这个案例的详细分析,解释了上述的投毒手法。
真实 Connext 女巫投毒案例
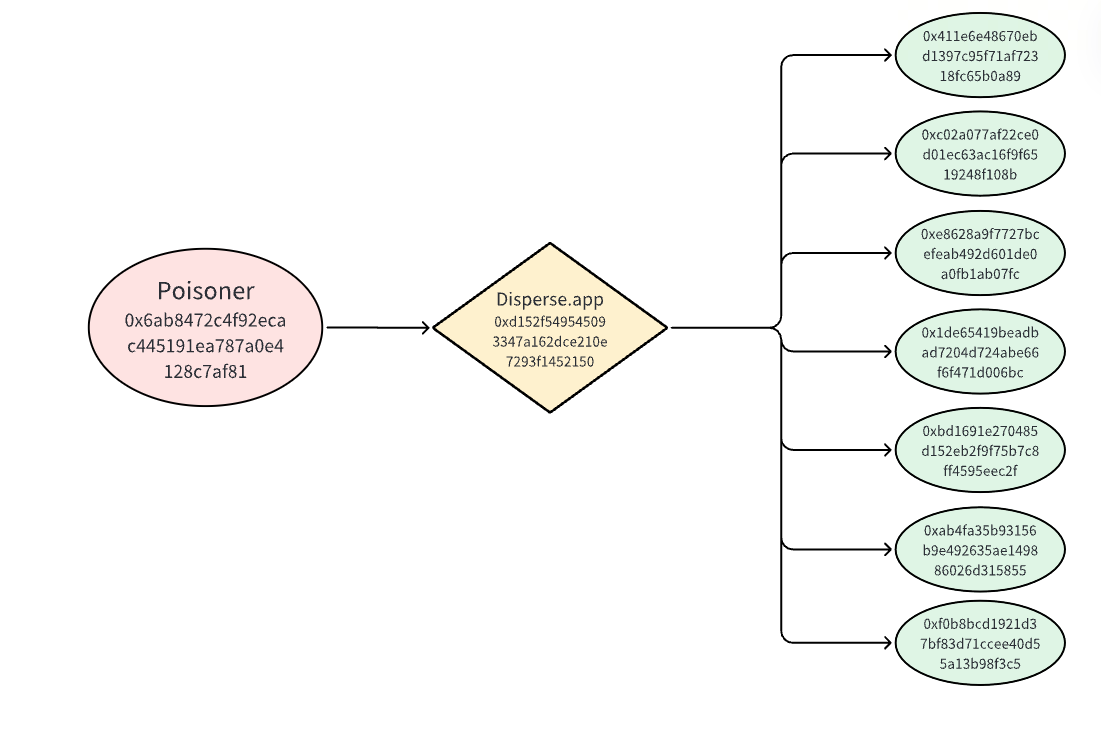
如图所示,投毒者地址0x 6 ab 使用 disperse.app 向七个无辜地址批量转账。我们通过如下证据详细分析了这个 Connext 女巫投毒案例:
Polygon Scan 显示投毒者交易记录,投毒者从 OKX 存入 1 Matic 后,它唯一的行动就是向这 7 个地址批量转账。(https://polygonscan.com/address/0x6ab8472c4f92ecac445191ea787a0e4128c7af81)
投毒转账发生在 2023 – 08 – 25 05: 49: 40 至 2023 – 08 – 25 05: 52: 12 期间,即 Context 社区女巫举报计划期间。
投毒者进行了 7 轮转账,每轮向 7 个地址中的每个地址发送 0.0001 MATIC。由于投毒者可以在某一轮向同一地址进行多次转账,因此在所有 7 轮转账中总共进行了 180 次转账。180 次投毒转账的完整列表可在如下提供的谷歌文档链接中找到。(https://docs.google.com/spreadsheets/d/ 1 dR 9 wVZN 1 o 0 _vBixKrxg 6 JSycHj 7 ADQlo /edit?usp=sharing&ouid= 117000940990722879540 &rtpof=true&sd=true)
所有 7 个地址都是 Connext 空投发放候选地址。女巫举报报告 #589 (https://github.com/connext/community-sybil-reports/issues/589)以这些转账为证据,指控这七个地址是女巫聚类团伙。
这 7 个地址之间没有检测到任何直接转账。除投毒地址的直接转账外,它们之间没有任何交易。
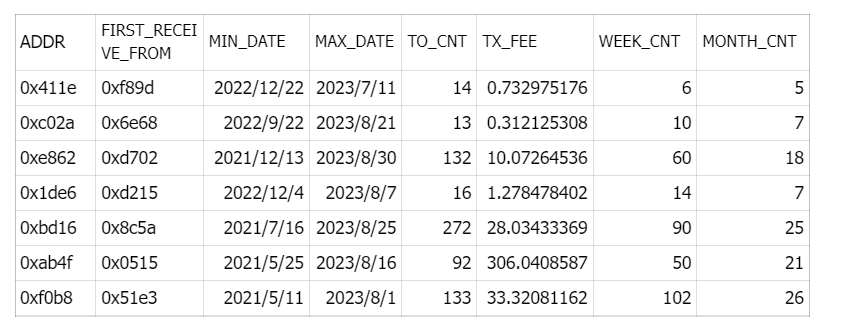
我们分析了这些地址的 Polygon 活动统计。如表所示,这 7 个地址在首次资金来源、首次和最后一次交易日期、交互合约数目、交易费用和活跃周/月等指标上完全不同。这种极端差异意味着它们不可能属于一个人控制的女巫团伙。
通过分析,我们得出结论,这是一个与 Connext 空投有关的实际投毒案例,采用了强制关联/聚类的投毒策略。
Trusta 发起 “Proof of Innocence”计划(PoIP)
Trusta 通过链上分析发现,由于女巫投毒攻击行为,许多不相关的地址被错误地标记为女巫,这不仅出现在 Connext 空投中,而且还出现在其他各种对无辜钱包的无差别攻击中。这类投毒攻击已经伤害到了用户和整个社区,同时影响了社区与项目方之间的信任。
Trusta 一直致力于在Web3和加密世界建立更多信任,为了更好的保护无辜地址被女巫投毒,联合起来打击投毒攻击行为,Trusta 发起了 “Proof of Innocence”计划(PoIP)。这个计划可以让被投毒的无辜地址证明自己的清白。如果你的地址被投毒,你可以选择:
1. 访问 PoIP 入口(如下链接)并提供被投毒详情,如你的钱包地址、被投毒地址、交易哈希值和所在链等。(https://docs.google.com/forms/d/e/ 1 FAIpQLSe_ 1 dl 6 ocyhnDWUtm 9 BBvmWDGL_rDjhc 9 NNpfHXff 2 XhXL 5 eg /viewform)
2. Trusta 将结合人工和 AI 分析算法共同判断是否投毒攻击。
3. 你将在一天内通过电子邮件收到判断结果。
4. 这些数据将共同形成一个数据库,证明你的地址与投毒地址无关!
Trusta 已推出并被 Gitcoin Passport 等多个头部社区所使用的真实用户识别服务 TrustScan 和链上价值评分产品 TrustGo(https://www.trustalabs.ai/),都将结合这些数据不断提升用户识别结果的准确率。同时 Trusta 也将向所有项目方和反女巫团队提供这些数据,以防止因投毒攻击而错误地将这些无辜地址识别为女巫地址。



