SharkTeam:Tornado.Cash提案攻击原理分析
北京时间 2023 年 5 月 20 日,Tornado.Cash 遭受提案攻击,攻击者已获利约 68 万美元。

SharkTeam对此事件第一时间进行了技术分析,并总结了安全防范手段,希望后续项目可以引以为戒,共筑区块链行业的安全防线。
一、事件分析
攻击者地址:
0x092123663804f8801b9b086b03B98D706f77bD59
0x592340957eBC9e4Afb0E9Af221d06fDDDF789de9
攻击合约:
0xAF54612427d97489707332efe0b6290F129DbAcb
0x03ecf0d22f9ccd21144a7d492cf63b471916497a
0x7dc86183274b28e9f1a100a0152dac975361353d(部署合约)
0xc503893b3e3c0c6b909222b45f2a3a259a52752d(假提案合约)
被攻击合约:
0x5efda50f22d34F262c29268506C5Fa42cB56A1Ce
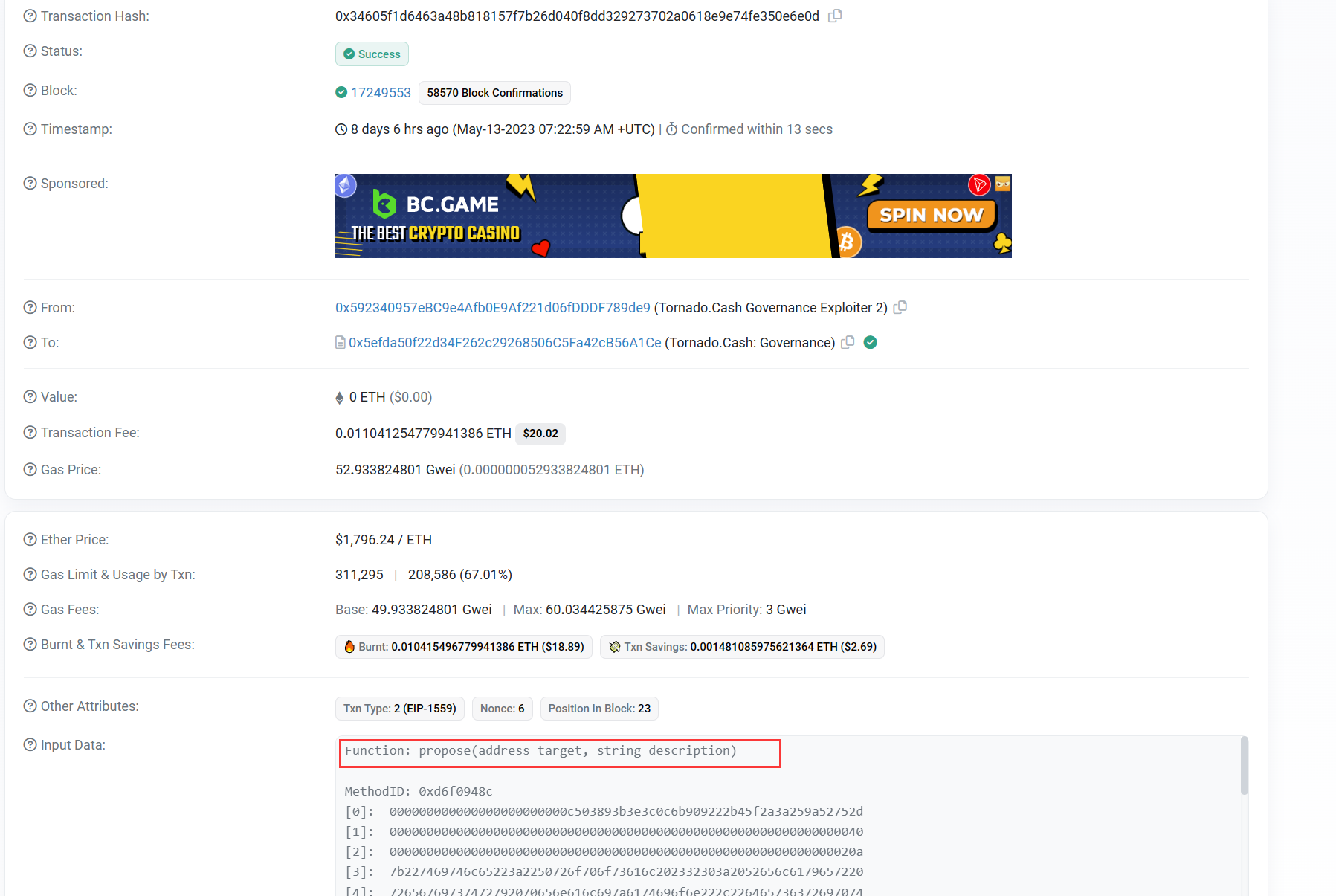
发起提案交易:
0x34605f1d6463a48b818157f7b26d040f8dd329273702a0618e9e74fe350e6e0d
攻击交易:
0x3274b6090685b842aca80b304a4dcee0f61ef8b6afee10b7c7533c32fb75486d
攻击流程:
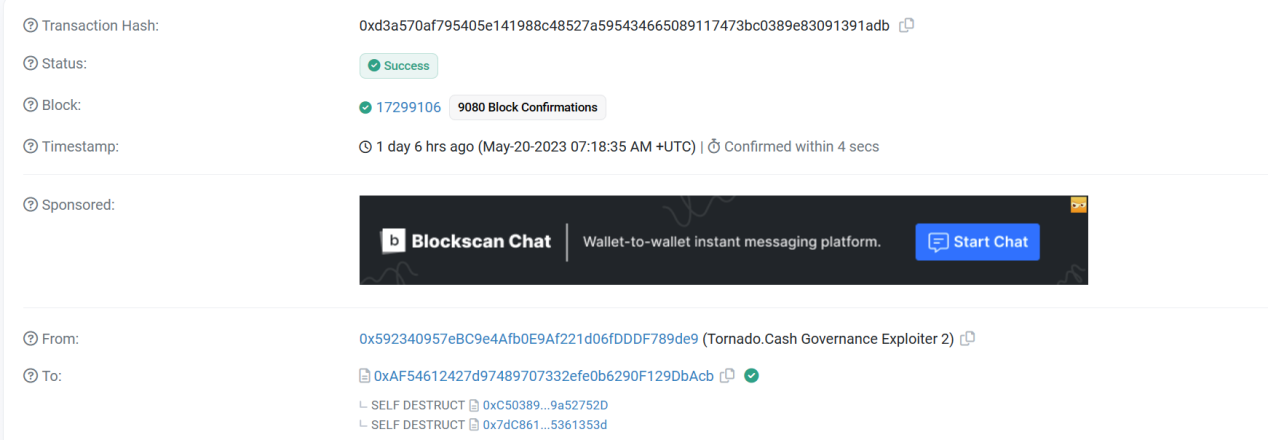
(1 )首先,攻击者(0x 59234095 )先向被攻击合约(0x5efda50f)发起了一个提案,并宣称此提案是 16 号提案的补充
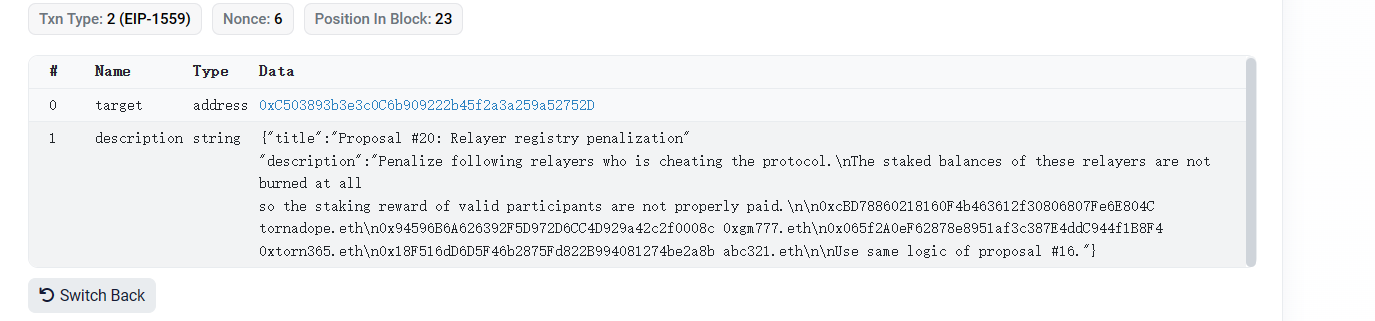
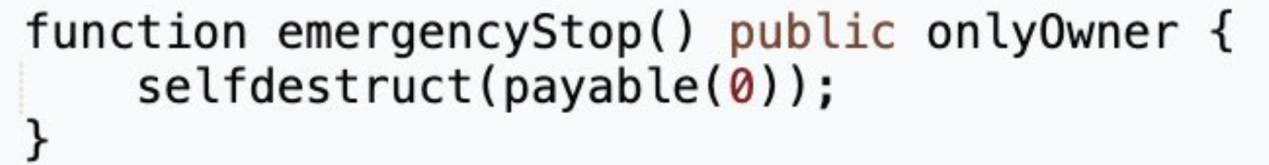
(2 ) 但提案中实际上存在一个额外的自毁函数。
(3 )很遗憾的是社区并没有发现此提案中存在问题,大多数成员都投票通过了这次提案。
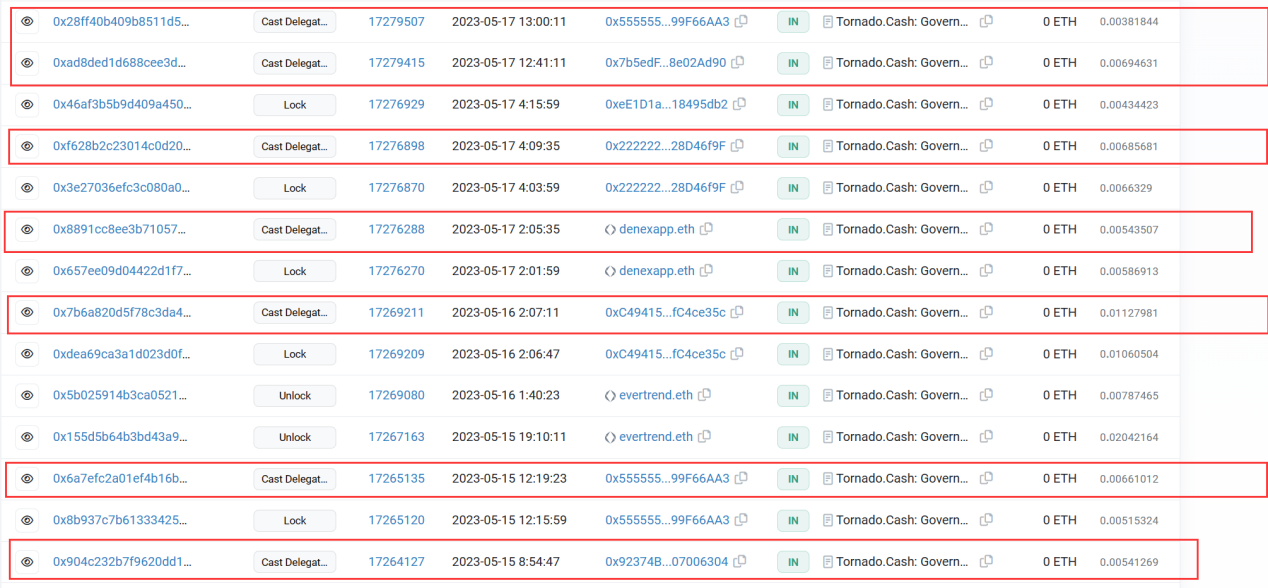
(4 )攻击者创建了很多个合约来实行代币的转移
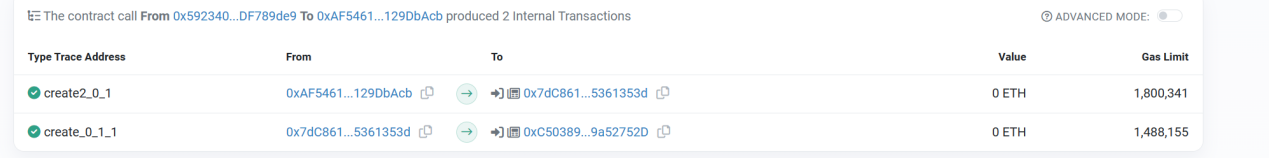
(5 )攻击者(0x 59234095 )销毁了提案合约(0xc503893b)和他的创建合约(0x7dc86183)。随后在相同的地址重新部署了攻击合约(0xc503893b)。
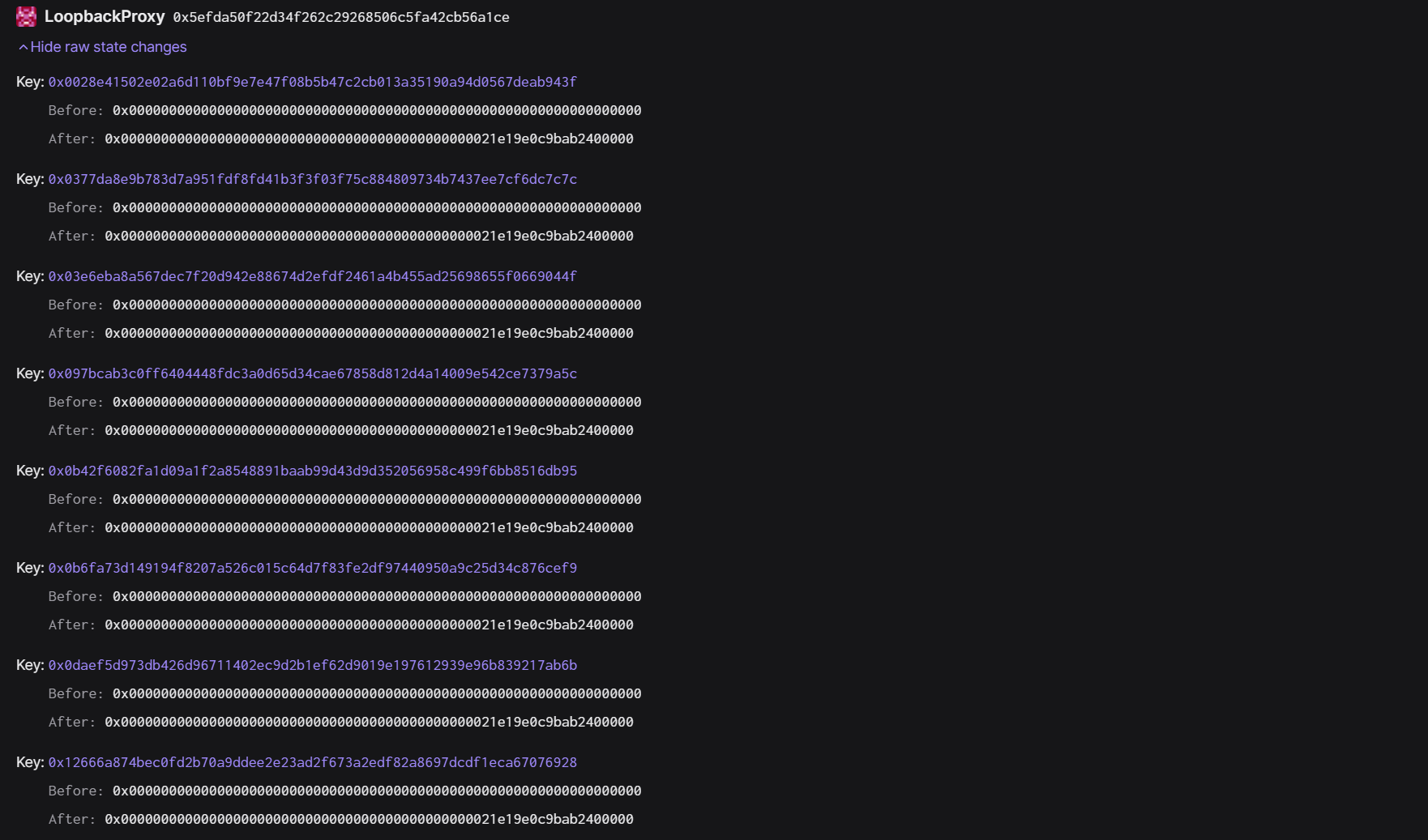
(6 )修改完提案合约后,攻击者(0x 59234095 )执行提案并将自己所控制的合约地址的代币锁定量都修改为 10000 。
(7 )提案执行完成后,攻击者(0x 09212366 )将代币转移到自己的地址,并获得被攻击合约的所有权。
漏洞分析:
由于提案合约(0xc503893b)的创建合约(0x7dc86183)是通过creat 2 进行部署的,所以两个合约销毁之后,在同一地址上可以部署新的逻辑合约,并且提案执行是通过delegatecall的形式调用,攻击合约可任意修改被攻击合约中的值。
事件总结:
本次事件发生原因是由于社区在检查提案时未能发现提案中存在的风险,并没有认真核实提案合约的代码是否存在安全漏洞。
二、安全建议
针对本次攻击事件,我们在开发过程中应遵循以下注意事项:
(1 )在进行提案设计时充分考虑提案机制的安全性并尽量降低提案被中心化控制的风险,可以考虑通过降低攻击的价值,增加获得投票权的成本,以及增加执行攻击的成本等方式结合实际妥善设计。
(2 )在进行提案的投票前,社区应慎重检查合约代码是否有后门。
(3 )在提案通过前,可联系第三方安全审计公司对合约逻辑代码进行安全审计。
About Us
SharkTeam的愿景是全面保护Web3世界的安全。团队由来自世界各地的经验丰富的安全专业人士和高级研究人员组成,精通区块链和智能合约的底层理论,提供包括智能合约审计、链上分析、应急响应等服务。已与区块链生态系统各个领域的关键参与者,如Polkadot、Moonbeam、polygon、OKC、Huobi Global、imToken、ChainIDE等建立长期合作关系。



