オイラー・レゴの連鎖反応:7社が影響を受けたDeFi契約と6社の「不正行為」監査会社
原作者:Jaleel、0x22D,BlockBeats
原作者:
ハッカーはどのようにしてオイラーを攻撃したのでしょうか?現在影響を受けるのはどの契約ですか?オイラー社の監査を行った企業はどこですか? BlockBeats が簡単なレビューを行いました。
最初のレベルのタイトル
攻撃プロセスのレビュー: 「違反者」と「清算者」
Euler Finance の監査パートナーの 1 つである Omniscia は、攻撃を詳細に分析した事後技術分析レポートを発表し、悪用された脆弱性は Euler が寄付アドレスに対して適切なセキュリティ チェックを実行しなかったことに起因すると指摘しました。
このエクスプロイト コードは、オイラー エコシステム全体にいくつかの変更を導入したプロトコルである eIP-14 に導入されました。この欠陥は、EToken 実装 ( EToken: donateToReserves 機能) によって行われた最初の変更に存在します。その後、攻撃者は脆弱なコードを利用して、プロトコルの準備金に資金を寄付することで無担保のトークン負債ポジションを作成し、攻撃者がこれらの口座を清算して清算ボーナスから利益を得ることができるようにしました。
このセキュリティは、ユーザーが DToken 残高に影響を与えることなく EToken ユニットを無担保で寄付することで、レバレッジの形で「不良債権」を生み出すことを可能にする寄付メカニズムによって裏付けられていません。
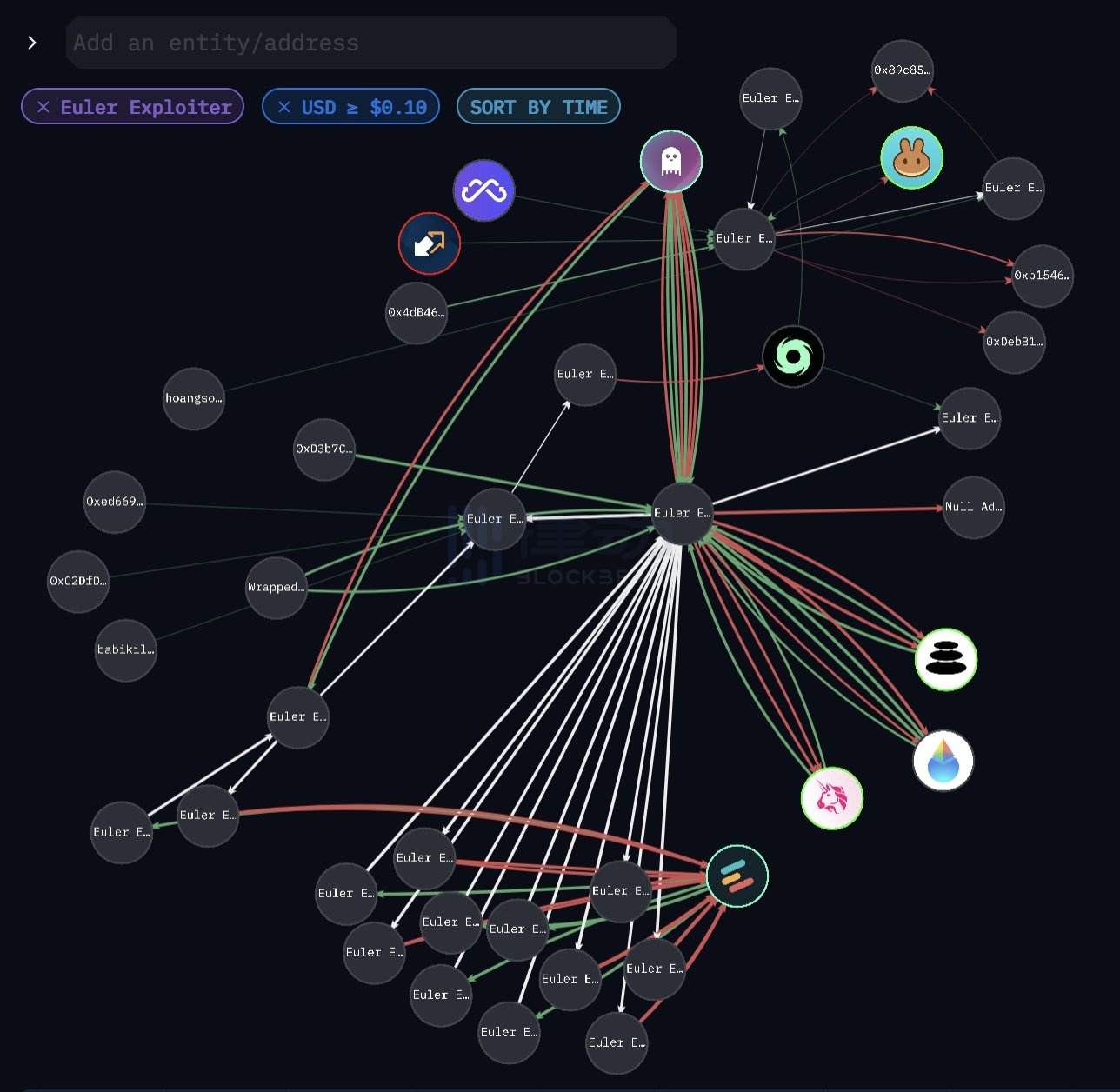
画像の説明
画像ソース: Arkham Intelligence
Arkham の調査によると、攻撃者は 20 以上の異なる契約アドレスを使用して、オイラーからさまざまな暗号化資産を取得しました。ハッカーは資産ごとに、「違反者」と「清算者」という 2 つの契約を導入しました。 「違反者」は寄付機能を利用してオイラーの論理を覆し、「清算者」は残り物を一掃します。
ハッカーの具体的な実行プロセスは次のとおりです。
1) まず、Balancer / Aave v2 からフラッシュローンを利用し、3,000 万 DAI を借ります
2) Violator と Liquidator の 2 つの契約を展開します。 「違反者」によって預けられた場合、「清算人」は同じ取引のポジションを決済する責任があります。
3) 資金の 2/3 を Euler に預け、20 M DAI を Euler に送金し、19.5 M eDAI を受け取ります
4) その後、入金額の 10 倍を借りて、オイラーから 195.6 M eDAI と 200 M dDAI を受け取ります
5) 残りの資金の 1/3 を借金の一部の返済に使用し、1,000 万 DAI を送信し、1,000 万 dDAI を燃やしました
6) ステップ 4 を繰り返して、オイラーから 195.6 M eDAI と 200 M dDAI を受信します。
7) 返済資金の 10 倍を寄付し、1 億 eDAI をオイラーに寄付
9) 次に、3,890 万 DAI の引き出しを含む、オイラーからすべてのトークン金額を引き出します。 10) フラッシュ ローンを返済した後、USDC と WBTC を DAI と ETH に交換します。
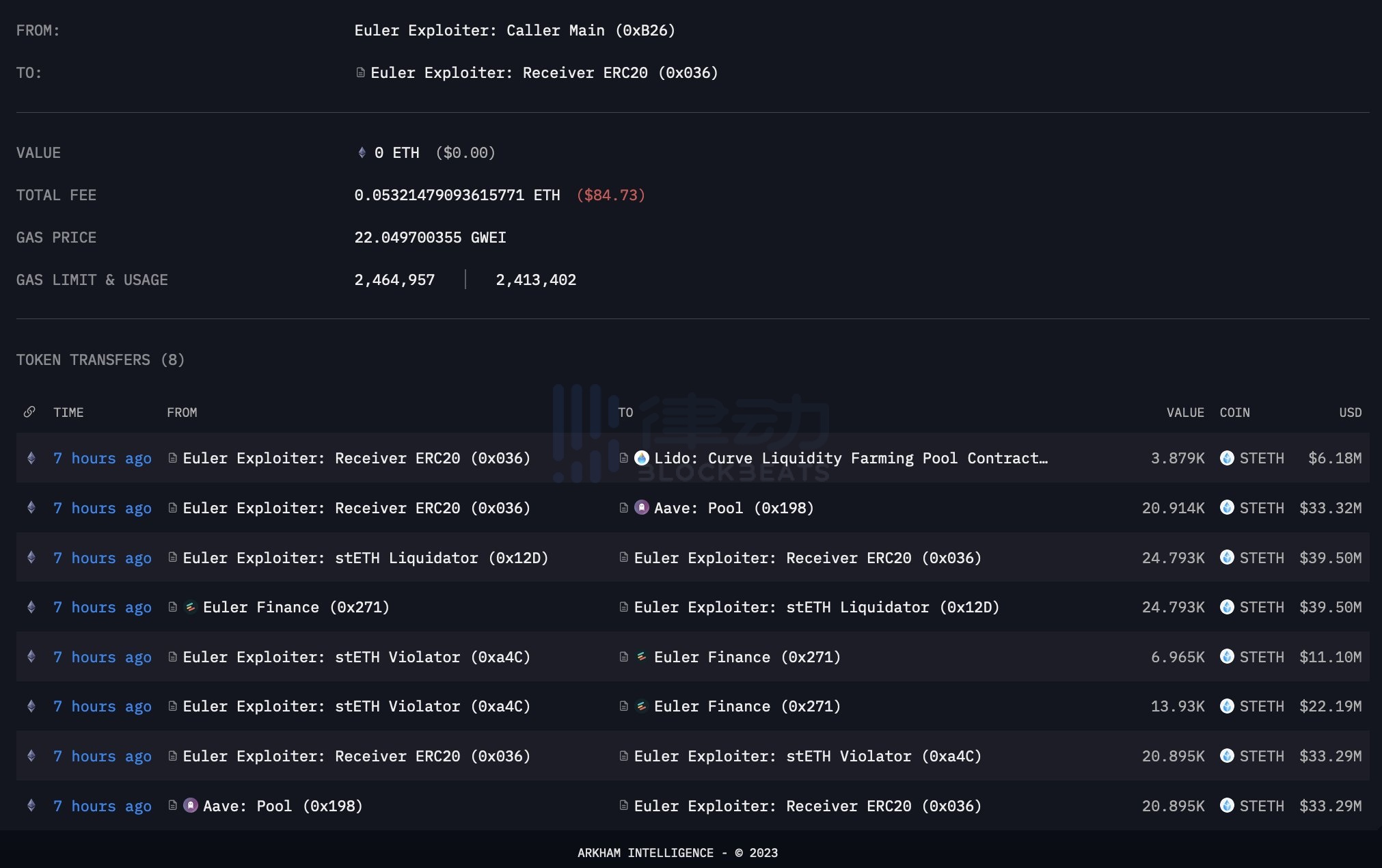
画像の説明
画像ソース: Arkham Intelligence
「受信者」とマークされたアドレスは、エクスプロイトを実行する (その後エクスプロイト資金を受け取る) ために使用されるコントラクトのアドレスです。資金の大部分は「保有者」というラベルが付いた別のアドレスに送られます。このアドレスには現在、1億9,200万ドル相当の暗号通貨が保管されている。
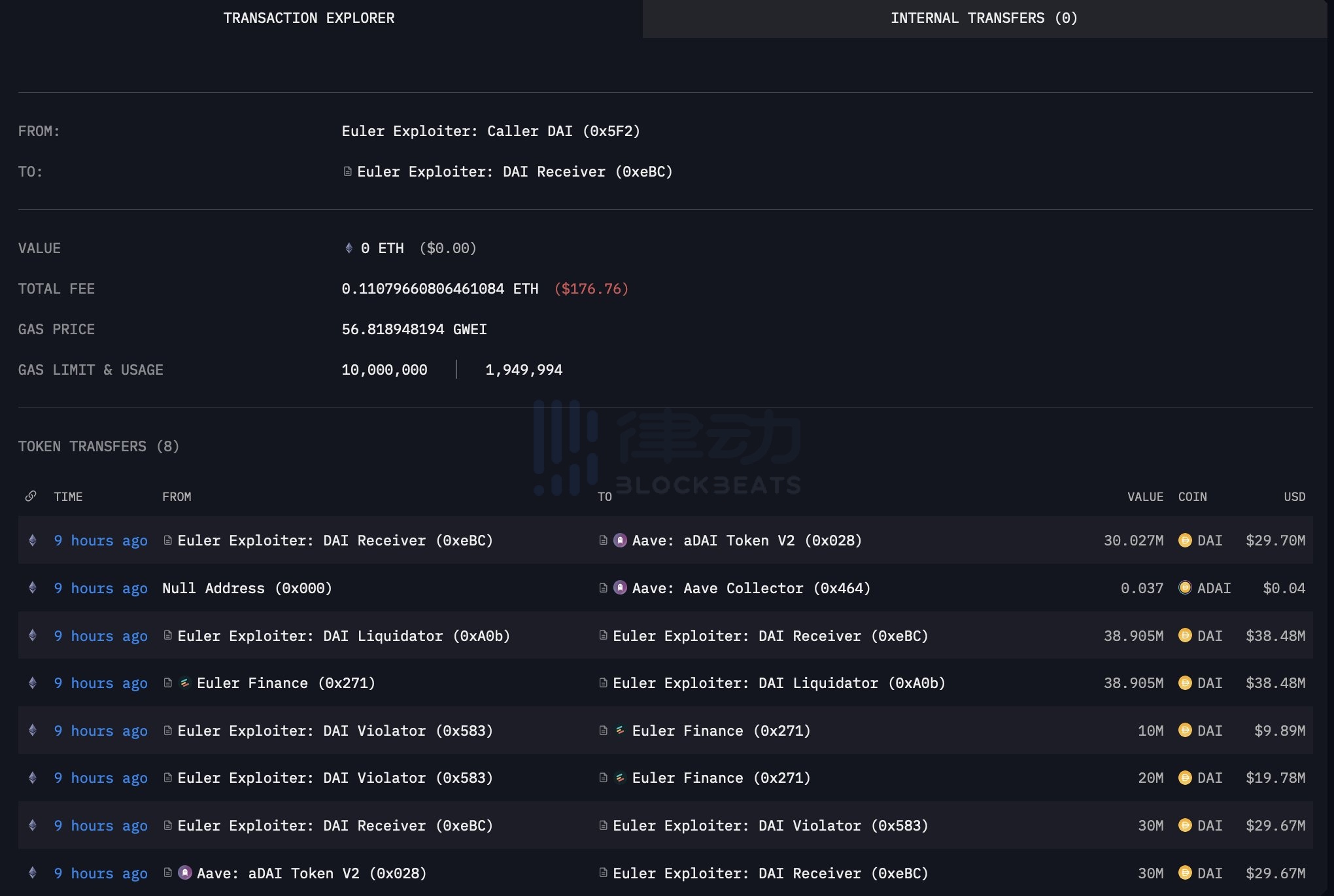
画像の説明
画像ソース: Arkham Intelligence
PeckShield の監視によると、Euler Finance の攻撃者は、0x c 66 d で始まるアドレスを通じて、少なくとも 100 イーサリアムを Tornado Cash に転送しました。同時に、オンチェーン探偵 ZachXBT の分析によると、このアドレスは一部のネットワークを攻撃しました。 BSC のプロトコルに従って、盗まれた資金も Tornado Cash に入金されます。ほとんどの人が推測しているように、攻撃者はほぼ間違いなくブラックハットです。
最初のレベルのタイトル
どのような契約が影響を受けますか?
Aztec
オイラー攻撃は広範囲に及んでおり、次のようなオイラーに関連するいくつかの DeFi プロトコルに影響を与えます。
Euler Finance の脆弱性は、資金を引き出しようとした Aztec Connect ユーザーに影響を及ぼし、影響を受けたユーザーは現在資金を引き出すことができません。 Aztec は Euler との統合を制御できませんが、現在 Aztec Connect 機能は機能しています。
Yield
さらに、Aztec が発表した Aztec Connect は世界初のプライバシー ロールアップであり、その設計にはいくつかの問題があり、メンテナンス コストが増加していることも注目に値します。プロジェクトの規模と商業的要因を考慮すると、Aztec は間もなく Connect を終了し、すべてのエンジニアリング リソースが L2 プライバシー プロトコル Noir の構築に充てられ、次のバージョンではデフォルトのプライバシーを備えた完全にプログラムされたスマート コントラクトをサポートする予定です。
Balancer
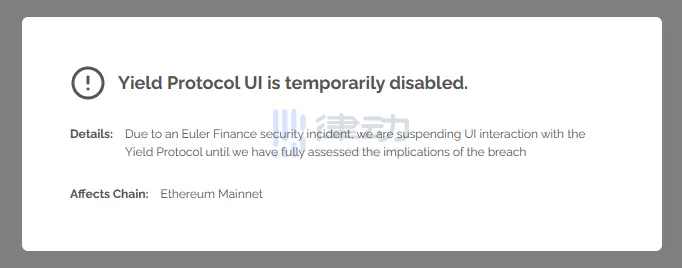
Yield Protocolは、Euler攻撃のため、メインネットワークの融資関連業務を閉鎖しました。Yieldのメインネットワークの流動性プールはオイラー上に確立され、オイラーはメインネットワーク契約を一時停止しました。現在、Yieldはアプリケーションを削除し、公式サイトでローンの入り口を閉鎖しましたウェブサイトのUI。
SwissBorg
Euler Finance攻撃では、流動性プールTVLの65%を占める約1,190万米ドルがbbeUSD流動性プールからオイラーに送金され、bbeUSDは他の4つの流動性プール(wstETH/bbeUSD、rETH/bbeUSD、TEMPLE)にも入金されました。 /bbeUSD、DOLA/bbeUSD、その他すべてのバランサー流動性プールは安全です。残りの資金を保護するために講じられた措置のため、UI は現在、これらの bbeUSD プールのポジションを手放す既存の LP をサポートしていませんが、資金がさらに失われるリスクはありません。 bbeUSD プールのユーザーは、UI を使用してトークンと bbeUSD を比例的に引き出すことができますが、オイラーが eToken (eDAI/DAI など) の譲渡可能性を回復するまで、bbeUSD から資金を引き出すことはできません。
SwissBorg は 6,357 Ethereum と 170万 USDT を Euler に預けました。攻撃後、SwissBorg は損失を減らすために 4,752 cbETH をすぐに貸し出しましたが、依然として足止めされ、約 1,617.23 ETH (またはわずか 1,617.23 ETH) を失いました。総資産の 2.27% を引き受ける予定です)。 170万USDT(プランに加入している総資産の29.52%を占める)。
Idle DAO
幸いなことに、スイスボーグによると、こうしたシナリオを防ぐためにリスク管理手順を含む多くの準備が何年も前から行われてきたため、被害の程度は最小限に抑えられているという。この場合に生じた損失はすべて SwissBorg が負担し、ユーザーはこれによって損失を被ることはありません。
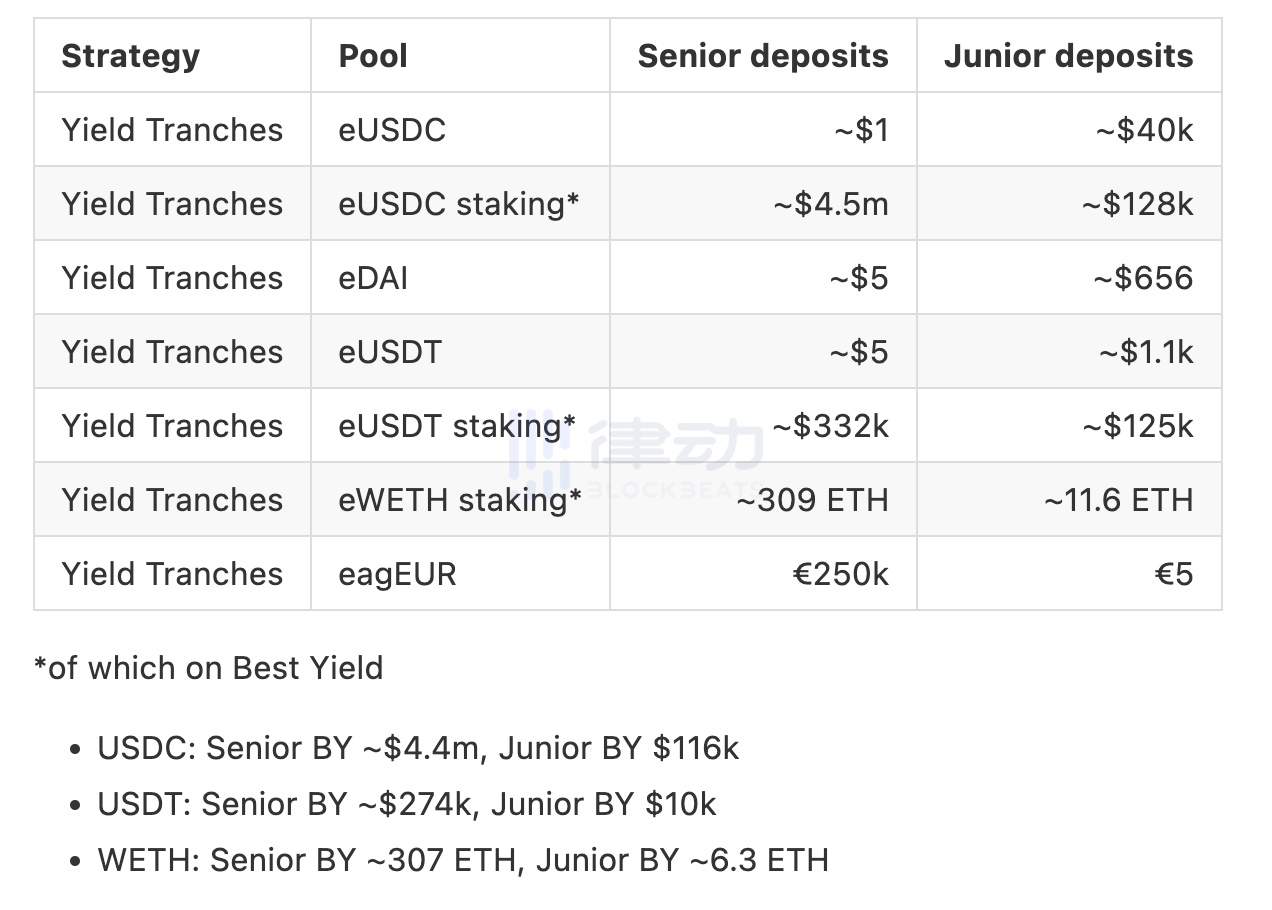
DeFi協定のアイドル・ファイナンスは、調査の結果、オイラー・ファイナンス事件の摘発には、協定のイールド・トランシェ戦略に約535万米ドルのステーブル・コインと320ETHが関与し、ベスト・イールド戦略の摘発には関与したと述べた文書を発行した。 480万米ドルのステーブルコインと313のETH。
Angle
さらに、アイドル・ファイナンスは、実際の影響はオイラーチームの行動と考えられる緩和策次第であると強調し、上記の数字は実際のリトレースメントではなく、オイラーに固定された実際の数字であると強調した。アイドル・ファイナンスはまた、シニア/ジュニア・ベスト・イールドDAI保管庫は、USDCがペッグされていないため、先週すべての資金をAaveに移管したため、保管庫(TVL総額1120万ドル)はオイラー事件の影響を受けておらず、現在は通常どおり運用されていると述べた。期待され、Aaveからお金を稼ぎます。
分散型ステーブルコイン協定であるアングル・プロトコルはソーシャルメディアに次のように投稿した:「アングル・プロトコルはオイラーのエクスプロイトの影響を受け、オイラーに1760万USDCが入金された。協定は停止され、債務上限は0に設定され、オイラーAMOは「リリースされました。閉鎖されました。状況を監視しており、情報を受け取り次第更新します。」
さらに、Angle Protocol は、オイラー ハッキングの前に、Angle コア モジュールの TVL は約 3,600 万米ドルで、コア モジュールを通じて 1,720 万 agEUR が鋳造されたと述べています。この契約には、標準流動性プロバイダーからの預金約 1,160 万ドル、ヘッジエージェントからの預金約 35,300 ドル、および剰余金約 558 万ドルも含まれています。
Yearn
DeFi収益アグリゲーターであるイヤーンは、オイラーの攻撃に直接さらされていないものの、一部のイヤーンボールトはアイドルとアングルの戦略の使用により間接的にハッキング攻撃にさらされていると述べた。このうち、yvUSDT と yvUSDC のエクスポージャーは合計 138 万ドルで、残りの不良債権は Yearn 金庫が負担し、すべての金庫は引き続きオープンで完全に運用されます。
最初のレベルのタイトル
6つの「不正」監査法人
Certora
事件が発覚するとすぐに、さまざまな世論がブロックチェーンセキュリティ監査会社に対する不信感を表明した。このような強力な強みと、監査を実施してくれるセキュリティ会社 6 社を見つける能力を備えたこのようなプロジェクトには、数億ドルを損失する可能性のある抜け穴がある可能性があります。 「DeFiは終わった」「監査は役に立たない」という声があちこちに響き渡ったが、本当に監査会社6社はオイラーの抜け穴を無視していたのだろうか。
Certora はイスラエルに拠点を置くブロックチェーン セキュリティ会社で、スマート コントラクト向けのセキュリティ分析ツールとサービスを提供しています。 2022年5月、CertoraはJump Crypto主導のシリーズBラウンドで3,600万ドルを調達した。 3,600 万ドルを調達する前に、Certora は Aave、Compound、Balancer、および SushiSwap のバグを特定していましたが、そのほとんどはコードがデプロイされる直前に発見され、修正されました。
チェルトーラは2021年9月から10月にかけてオイラーを監査した。 Certora は監査報告書の中で、オイラーのコードには重大度の高い問題が 3 つ、重大度が中程度の問題が 4 つ、重大度が低い問題が 2 つ含まれていると指摘しました。
Halborn
盗難を引き起こしたコードは 2022 年 7 月に Euler によって導入された新しい提案 eIP-14 からのものであるため、Certora はこの事件に対して責任を負いません。
Halborn はマイアミに本社を置くブロックチェーン セキュリティ会社で、2022 年 7 月に、Summit Partners が主導し、Castle Island Ventures、Digital Colurncom Group、Brevan Howard が参加した 9,000 万ドルのシリーズ A 資金調達の完了を発表しました。 Halborn ユーザーには、Solana、Avalanche、BAYC などの有名なプロジェクトが含まれます。
Solidified & ZK Labs
ハルボーンによるオイラーの監査は、eIP-14が導入される前の2021年5月から6月の間に行われたため、ハルボーンにも責任はありません。
Pen Test Partners
ブロックチェーンセキュリティ企業のSolidifiedとZK Labsは、それぞれOpenSea、Tether、Cosmosなどのプロジェクトに監査サービスを提供しており、2021年5月には共同でオイラーを監査しているため、今回の事件で責任を負う必要はない。
Omniscia
Pen Test Partners は、ブロックチェーン領域を超えたサイバーセキュリティ企業です。 2022 年 6 月、Pen Test Partners は Euler DApp のセキュリティを監査し、監査報告書で「アプリは攻撃に非常によく抵抗でき、Euler インフラストラクチャとユーザー データに対するリスクは低い」という結論を与えました。ペネトレーションテストパートナーも責任を負いません。
Omniscia は、複雑な分散型ネットワークとアプリケーションの構築とセキュリティに関する深い専門知識を持つ、経験豊富なスマート コントラクト監査人および開発者からなる分散型チームです。監査サービスには、Polygon、Ava Labs など 240 のプロジェクトと企業が含まれます。
SHERLOCK
オムニシシアは、マークル・プレッジ・マイニング・セキュリティ、チェーンリンク関連の機能セキュリティ、スワップ・ハブのセキュリティに焦点を当て、2022年3月、6月、9月にそれぞれオイラーに対して3回の監査を実施した。最後の監査は eIP-14 が提案されてから 2 か月後に行われましたが、eIP-14 は 3 回の監査に含まれていなかったため、Omniscia は大きなミスを犯しませんでした。
SHERLOCK は、スマート コントラクト保険サービスおよび監査プラットフォームであり、Opin、Euler、Lyra、Tempus、LiquiFi、Hook などのクライアントに総額 1,000 万ドルのオンチェーン脆弱性保険と報奨金を提供します。
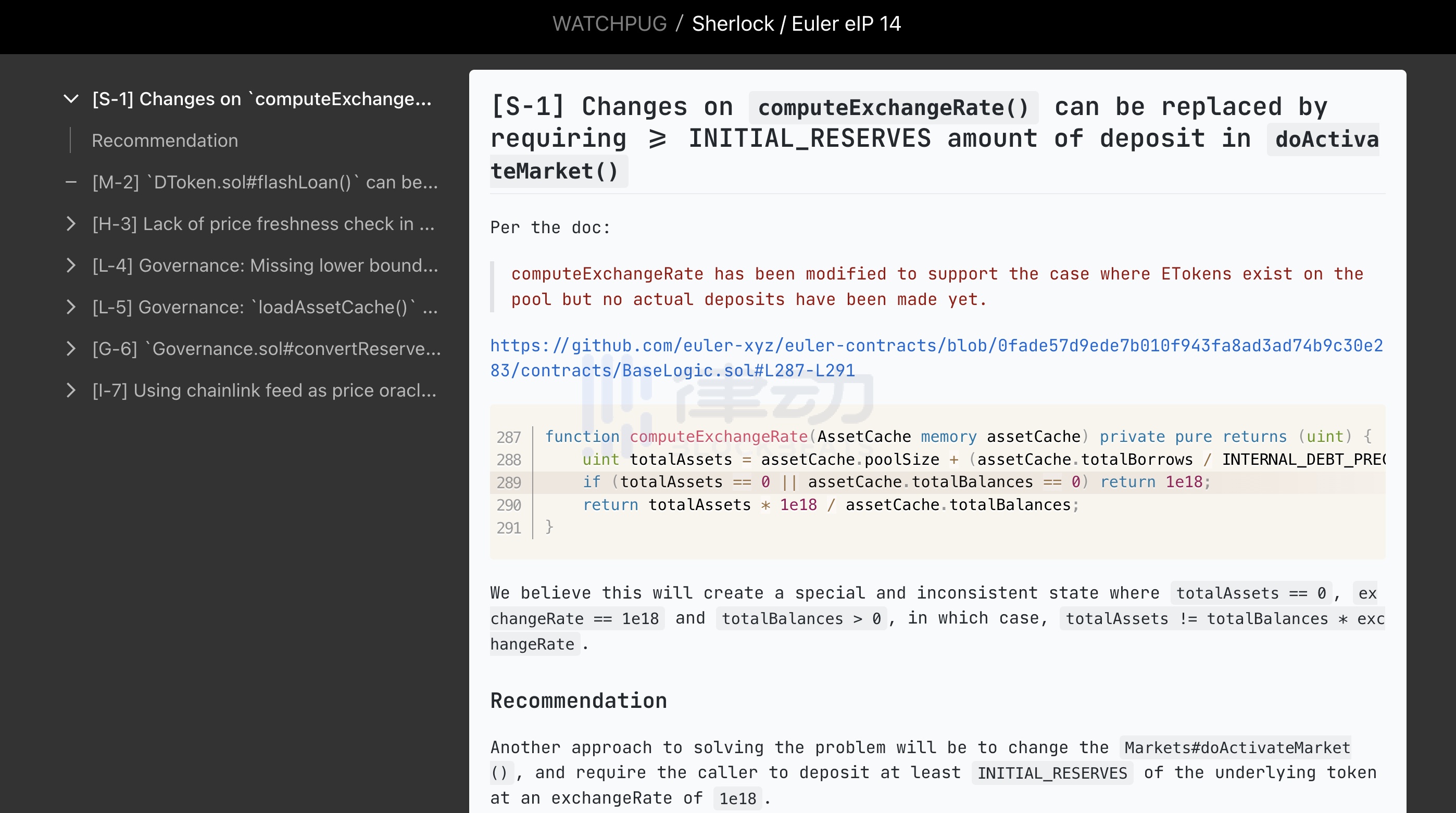
SHERLOCK は Euler に対して合計 3 回の監査を実施しました。 2021 年 12 月に監査人の Chris Michel によって最初に完成され、その後 2022 年 1 月に監査人の shw 9453 によって更新されました。そして最後の監査は、2022 年 7 月に監査人 WatchPug によって完了しており、攻撃を引き起こした eIP-14 の監査でした。
シャーロック社は責任を取る姿勢を示し、450万ドルの賠償計画を立て、330万ドルの賠償金を支払ったが、これは損失2億ドルに比べれば少なすぎる。
最初のレベルのタイトル
Web3 には新しい監査メカニズムが必要です
脆弱性を導入した機能の最後のレビューは SHERLOCK によって監査されましたが、他の 5 つの監査会社とは直接の関係はありません。しかし、このようなオールスター VC の投資に直面して、上流の資金提供者として多くの有名な DeFi 契約が短期間で 2 億米ドル近くハッキングされ、関与した資金は非常に巨額でした。今回のオイラーの攻撃はデフィにかなりの精神的打撃を与えた。
「監査は役に立たない」という声と比較して、この事件は実際にはブロックチェーンのセキュリティ監査の重要性と現在の監査プロセスの限界を浮き彫りにしています。監査人によるヒューマンエラー、不明確な監査範囲、新規提案の監査などが、現時点で監査の有効性に影響を与える主な要因となっている。この事件の主な責任者であるSHERLOCKは、実際にこれらの問題を認識していました。
シャーロック氏は2022年8月、大金を投じて少数の人にコードを4か月間チェックさせるのは騙されるのと同じだ、二度と騙されるな、二度と騙されるな、と述べた。 SHERLOCK は、従来のセキュリティ分野にキャプチャー・ザ・フラッグ・コンテストの形式を導入し、USDC を報酬として使用し、数百人のより広範なコミュニティの力を活用するために、単一のプロジェクト・ベースで抜け穴発見コンテストを開始します。人の。



