Telegram盗号诈骗事件频发,如何警惕与防范?
原文来源:Beosin
近期,跨平台的即时通讯软件Telegram盗号事件频发,不法分子通过非法手段盗取用户Telegram账号,并以冒充好友的方式进行诈骗。
针对近期的盗号诈骗事件,Beosin 安全研究部为大家梳理了Telegram 常见的诈骗方式,教大家如何警惕与防范。

一、诈骗方式
🧊骗取 TG 验证码截图
最近比较新颖的诈骗盗号,诈骗者冒充好友的身份以各种理由骗取聊天页面截图,看似毫无危险,但此刻骗子正在尝试利用你的手机号码登陆 Telegram,当发送的截图页面包含了官方发送的登陆验证码(Login code),即会被骗子利用成功登陆你的 TG 账号。骗取详细流程如下:
1.首先获取你 TG 账号的电话号码。
如果你的 TG 账号隐私设置成任何人可见,则会被陌生账号看到手机号码;或是骗子首先获取到你好友的账号,然后查询到你的手机号。
2.骗取登陆验证码。
骗子以各种理由,告诉你账号有问题,骗取你的聊天截图。同时,骗子在一台新设备输入你的手机号码尝试登陆。
例如以下两种话术类型:
(1 )聊天界面中有两个相同的联系人:当对某个联系人开启了加密聊天时,聊天列表就会出现两个相同的联系人,如下图加密的聊天通信会在名字前加一把锁。
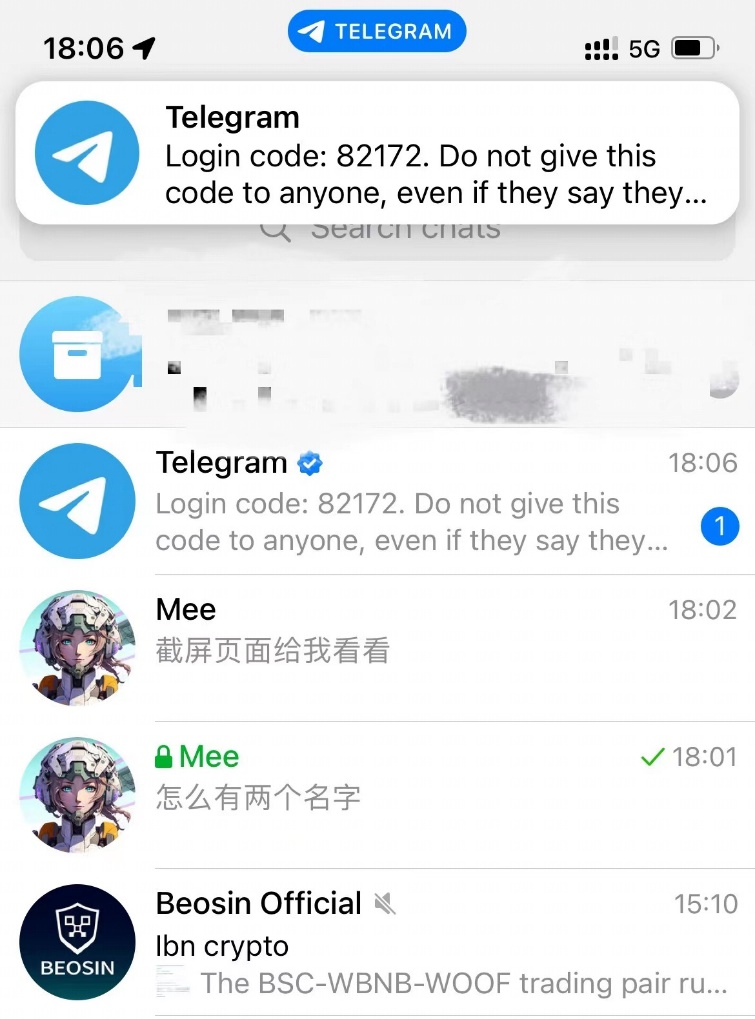
(2 )好友辅助解封账号:骗子称账号被官方限制,需要好友发送验证码帮忙解封账号。
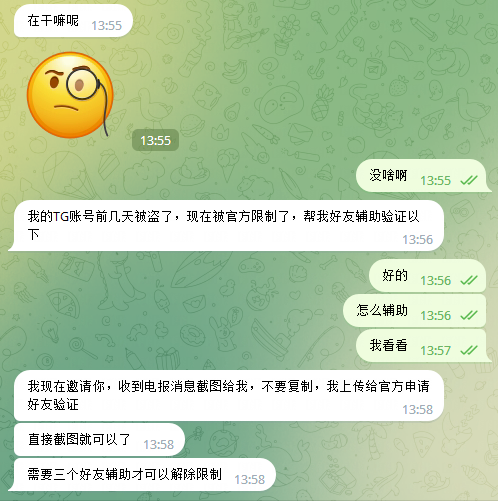
3.登录你的账号继续诈骗。
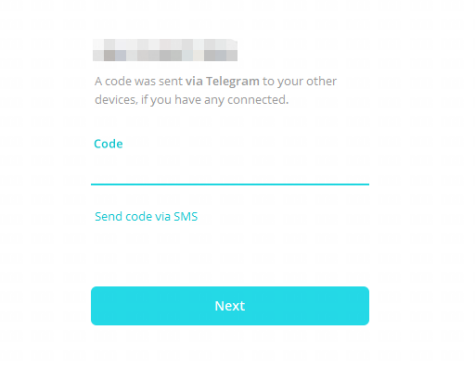
当你在不经意间把包含登陆验证码的聊天截图发给对方时,如果账号没开启两步验证,骗子则可以通过验证码直接登陆你的账号。随后骗子会删掉所有的设备,更改密码,然后继续骗通讯录中的其他人。
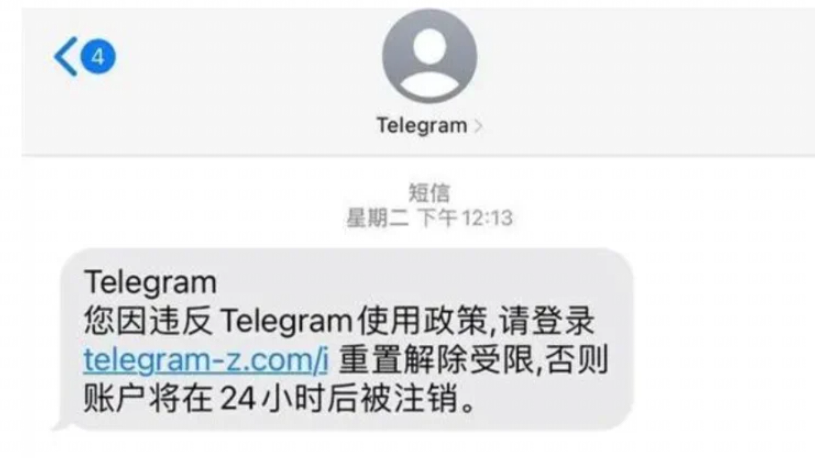
🧊冒充官方的诈骗短信
诈骗短信冒充Telegram 官方账号,声称该用户的 TG 账号违反了账号使用规则将被限制使用,需要登陆网站解除受限。如果用户不慎点击链接,账户就会被盗。
🧊带后门的第三方程序
由于 Telegram 没有中文安装包,普通用户通常会使用第三方搜索引擎来查找对应的中文安装程序,因此诈骗分子通过 SEO 优化为自己的 Telegram 中文版下载网站引流,诱导用户下载排名前列的应用程序。
当用户下载使用了带有后门的 TG 程序,会被自动检测聊天中的区块链地址,并且当检测到用户聊天消息中的钱包地址时,会将钱包地址替换成诈骗分子自己的地址,造成用户资金损失。
如下案例中,用户在 http://www.telegram-china.org(目前已失效)链接下载一个中文版的客户端,然后通过这个中文版发送一个 trx 的钱包地址:
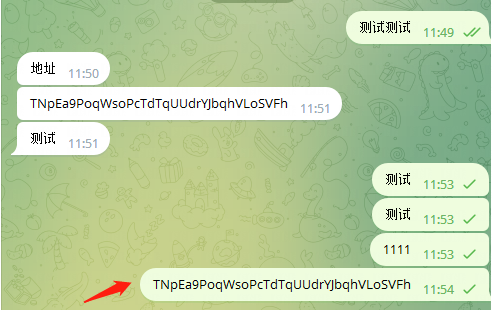
Beosin 测试结果
此时,发送的钱包地址为:TNpEa 9 PoqWsoPcTdTqUUdrYJbqhVLoSVFh
然后关闭软件重新打开发现钱包地址被替换为另外一个地址。
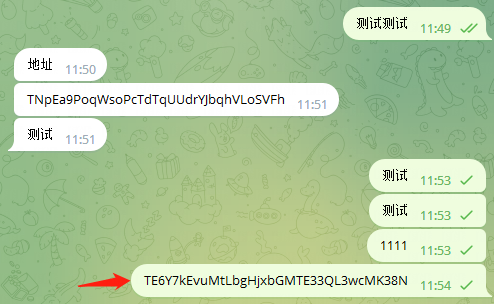
Beosin 测试结果
🧊恶意 Telegram 汉化语言包
前段时间某 TG 汉化频道(https://t.me/zh_CN_Telegram_zh_CN_CN_zh_ch_zn)被曝光是仿冒频道,真正的简体中文语言包维护频道是 https://t.me/zh_CN,因缺乏人员支持目前翻译工作已停止。该仿冒频道被曝光时有近八十万的关注者,其传播的语言包是一个带有后门的安装文件。
安全人员分析该语言包文件是一个下载器,运行后会下载各种模块并尝试绕过安全软件的检测。除此之外,该样本使用了检测鼠标移动等方式绕过沙箱分析。
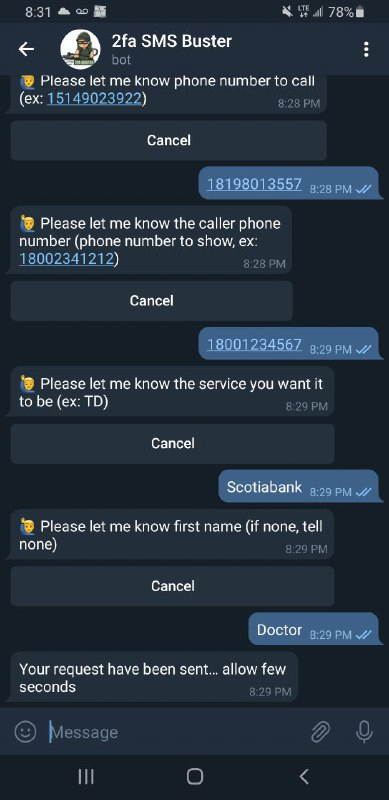
🧊Telegram bot 窃取密码
国外安全研究员发现,有犯罪组织利用 Telegram 机器人窃取用户 OTP 令牌和 SMS 验证码以完成 2 FA(双因素身份验证)。攻击者使用 Telegram 机器人获取帐户信息,包括致电受害者、冒充银行和合法服务等。通过社会工程,攻击者还欺骗人们通过移动设备向他们提供 OTP 或其他验证码,然后骗子用这些代码来骗取用户账户中的资金、密码、会话 cookie、登录凭据和信用卡详细信息。
🧊“加密货币投资”骗局
诈骗者冒充 Telegram 上的加密货币专家,宣传对加密货币投资有回报的承诺。诈骗者会通过 Twitter 评论,或直接在 Telegram 上与你联系,声称能够为你提供高额的投资回报。
如果参与,诈骗者会要求你在他们的特殊加密货币交易所开设一个账户。届时,他们会向你展示表明你的投资正在增加的图表,但是当你试图取出你的收入时,骗子连同你的账户就会消失。
Beosin 安全建议
针对 Telegram 的安全使用,避免被盗和资金损失,我们提出了以下参考建议。
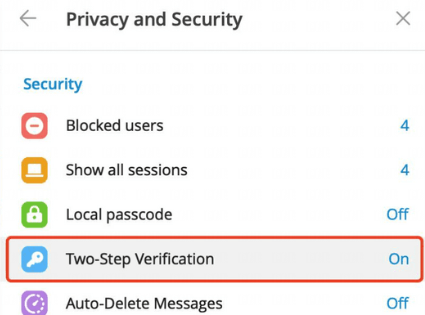
🧊开启两步验证
为了账号安全,及时设置两步验证密码。该密码只会在新登录 Telegram 时被要求输入。
打开 Setting(设置)> Privacy and Security(隐私和安全)> Two-step Verification(两步验证)进行设置,并建议在后续步骤中设置安全邮箱,目的是在忘记两步验证密码的情况下,可以通过安全邮箱进行重置密码。
🧊谨慎使用第三方客户端
检查自己的软件下载途径,如果是网页搜索下载的安装包,建议直接卸载后去官网重装。第三方客户端有能力获取和控制你的账户,读取你全部的聊天记录,收集你设备的可识别信息,安全起见,务必通过 Telegram 官网下载使用软件。
🧊不向电报机器人发送敏感个人信息
谨慎使用电报机器人服务,不泄露个人数据,包括姓名、用户名、手机号、电子邮件地址、密码数据或可用于识别您身份的任何信息。
🧊警惕陌生人私信
陌生人私聊不要轻易相信,提高警惕,避免造成资金损失或被盗取信息,如果被打扰可以选择屏蔽;收到的陌生文件、链接不轻易点击。
🧊转账地址验证
发送钱包地址与对方多次沟通验证;以截图钱包二维码的形式向对方发送钱包地址,对方通过扫码识别钱包地址。
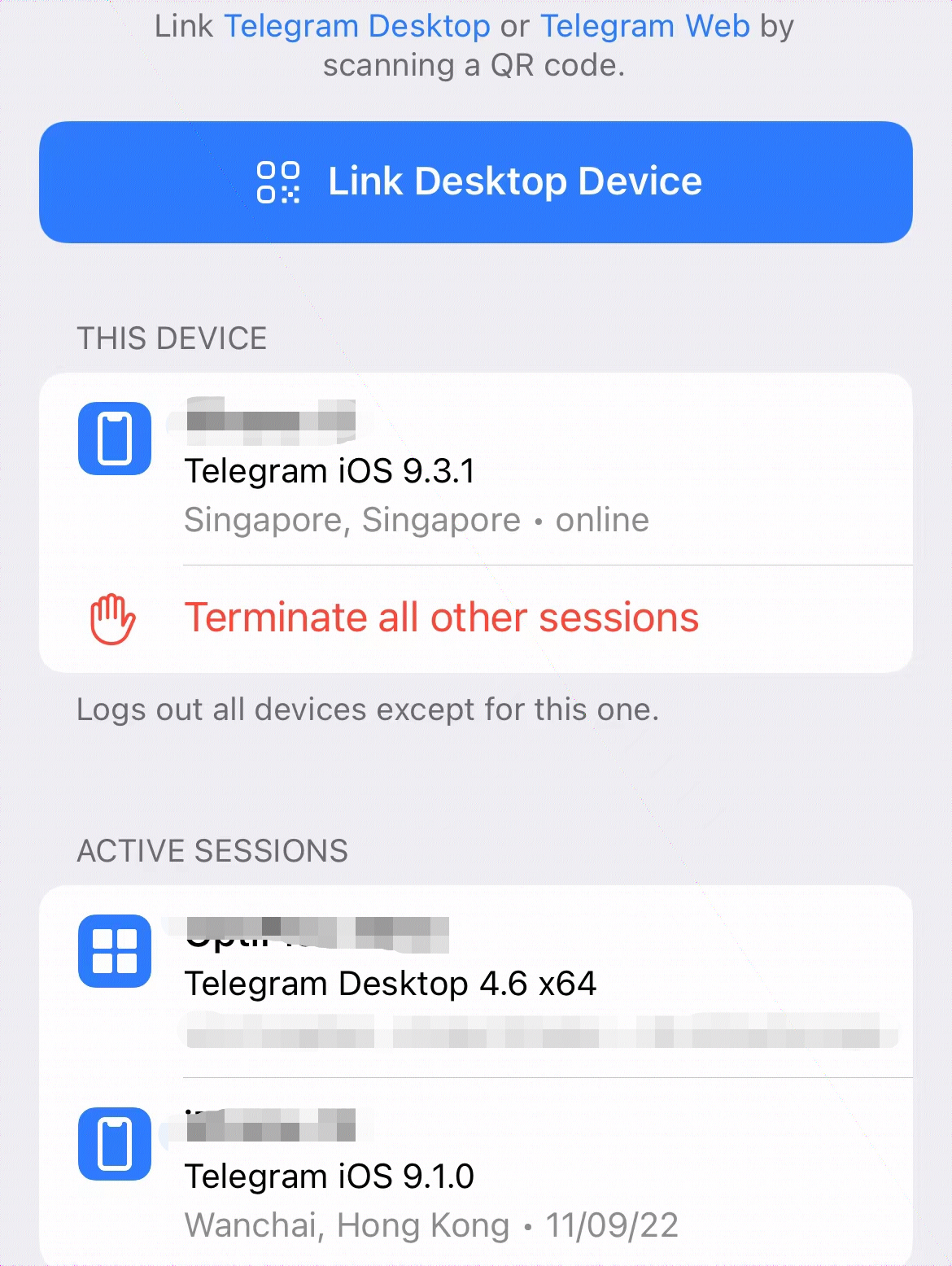
🧊定期查看 Telegram 的登陆设备
定期查看设备 IP 登陆状态,对有异常登录的设备 IP 强制下线。
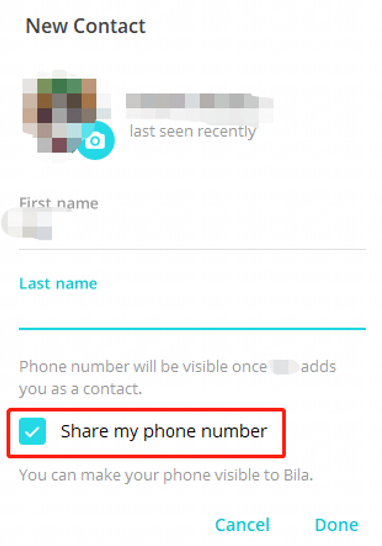
🧊添加联系人时取消分享手机号码
Telegram 只有 Contact(联系人),没有“好友”的说法。添加和删除联系人是单向操作,即你添加或删除某个联系人,并不会导致你在对方联系人列表中被添加或者被删除。因此注意在添加联系人时,取消 Share My Phone Number (分享我的手机号码),该选项会被默认勾选。
🧊隐藏手机号和加群限制等
在设置–>隐私与安全中选择设置隐藏手机号、上线状态、头像、转发消息等;设置账号不被非好友拉入陌生群,减少被骗概率;不使用 Telegram 附近的人功能。
Beosin 官网上线安全验证功能
同时,为了防范 Telegram、Twitter 等平台的“冒充”诈骗,Beosin 官网目前上线了安全验证功能。
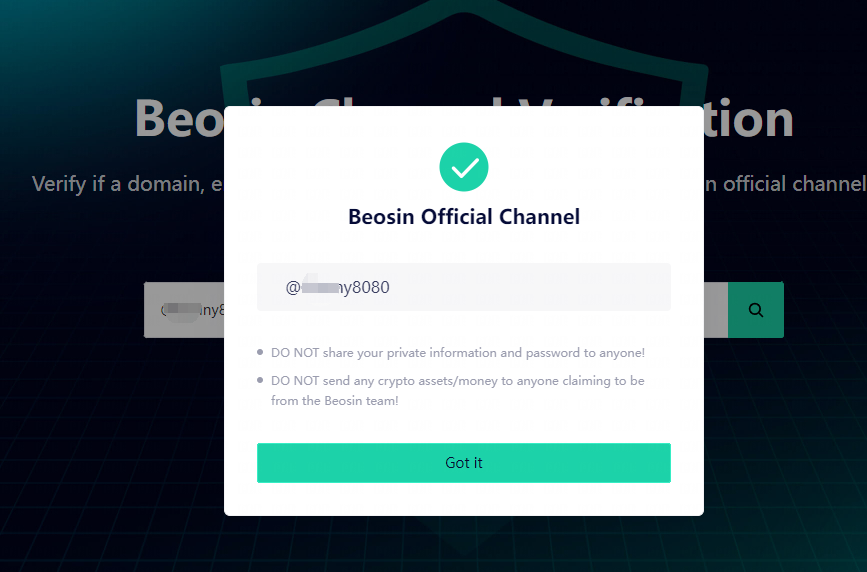
客户可以输入与您联系的Beosin的员工名片信息,如果通过验证,那就是安全的。
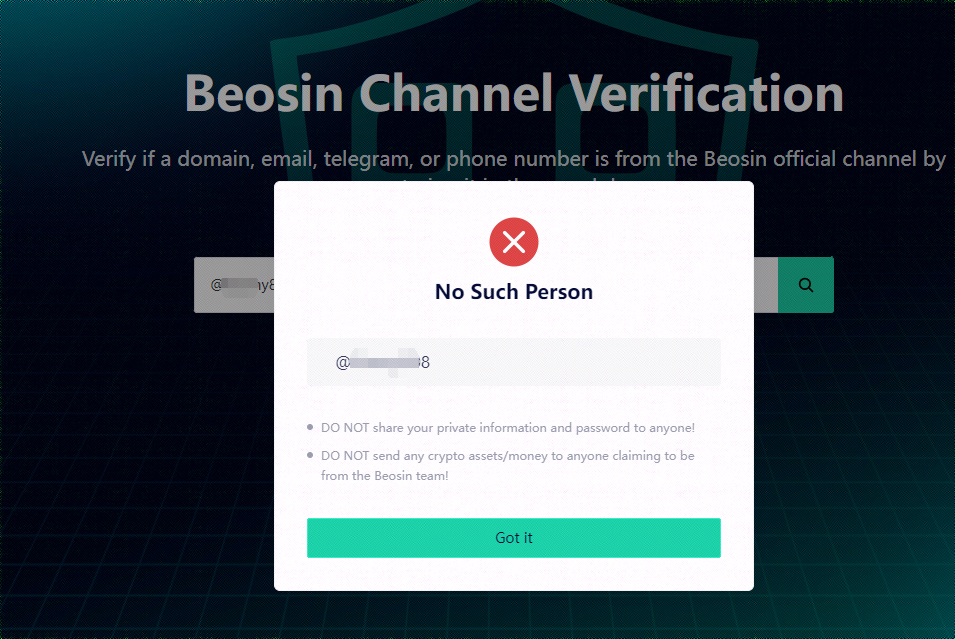
相反,如果不通过,那可能您遇到的是冒充 Beosin 员工的骗子,大家要多加防范。
好了,今天的安全分享就结束了,我们下期再见。
Beosin 是一家全球领先的区块链安全公司,在全球 10 多个国家和地区设立了分部,业务涵盖项目上线前的代码安全审计、项目运行时的安全风险监控、预警与阻断、虚拟货币被盗资产追回、安全合规 KYT/AML 等“一站式”区块链安全产品+服务,目前已为全球 2000 多个区块链企业提供安全技术服务,审计智能合约超过 3000 份,保护客户资产高达 5000 多亿美元。


![Axe Compute [NASDAQ:AGPU] 完成企业重组(原POAI),企业级去中心化GPU算力Aethir正式进入主流市场](https://oss.odaily.top/image/2025/12/12/ff08e068a361495da15f80b89405441e.jpeg)
