数百万ドルを略奪、Web3.0 独自のフィッシング攻撃のアップグレード版である Ice Phishing に注意してください

さまざまな種類の詐欺の中でも、フィッシング攻撃は詐欺師が使用する最も一般的な手法の 1 つです。
しかし、Web3.0の分野ではフィッシング攻撃だけでなく、コミュニティにとって大きな脅威となる「アイスフィッシング」のような攻撃も存在します。
2022 年の初めに、マイクロソフトはブログでこのタイプの攻撃の具体的な形式について初めて説明しました。詐欺師はユーザーの秘密キーとニーモニックを騙す必要はなく、詐欺師のウォレットに資産を転送する操作を承認するようユーザーに直接誘導します。
これまでのところ、Ice Phishing は Web3.0 分野で数百万ドルの財産的損害を引き起こしています。
アイスフィッシングとは何ですか?
Ice Phishing は、Web3.0 の世界に特有の攻撃の一種で、ユーザーがだまされてアクセス許可に署名させられ、詐欺師がユーザーのアカウント内の資産を直接消費することを可能にします。
これは、ソーシャル エンジニアリング攻撃の一種であり、ログイン資格情報やウォレット、秘密キーやパスワードなどの資産情報などのユーザー データを盗むためによく使用される従来のフィッシング攻撃とは異なります。
これと比較すると、Ice Phishing は Web3.0 ユーザーにとってより大きな脅威となります。DeFi プロトコルとの対話にはユーザーに許可を与える必要があり、詐欺師は承認する悪意のあるアドレスが正当なものであるとユーザーに納得させるだけで済みます。ユーザーが詐欺師による資産の使用を承認すると、アカウントが盗まれるリスクがあります。
オンチェーンアイスフィッシング
アイス フィッシング攻撃の最初の段階は、多くの場合、被害者がだまされて EOA または悪意のある契約を承認させ、被害者のウォレット内の資産を使い果たすというものです。
画像の説明
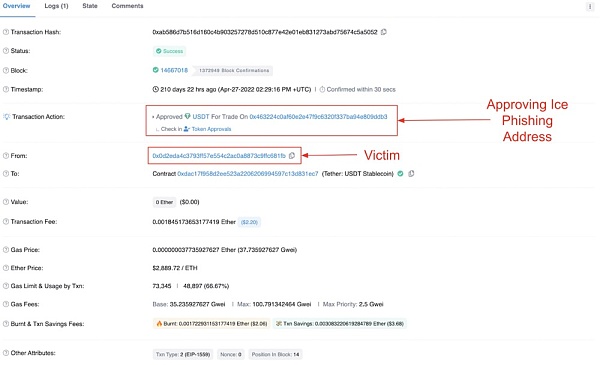
出典: イーサスキャン
画像の説明
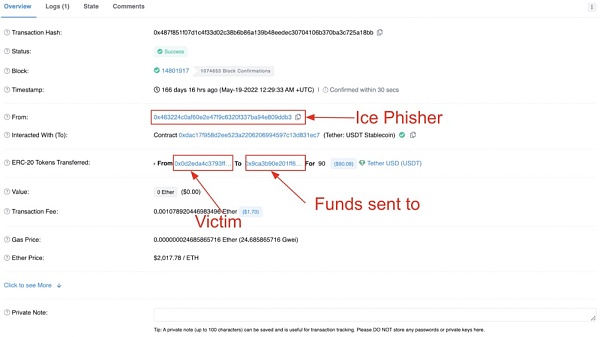
出典: イーサスキャン
画像の説明
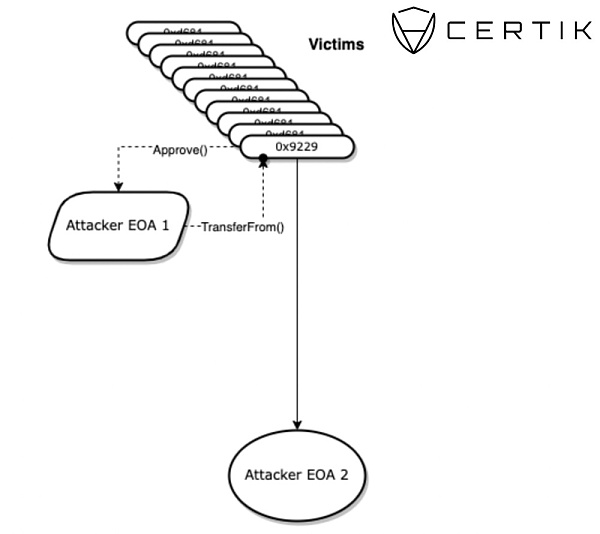
出典: CertiK
画像の説明
出典: イーサスキャン
見覚えのないアドレス、またはあなたの承認なしにトランザクションを開始するアドレスを見つけた場合は、すぐにアクセス許可を取り消してください (revoke.cash などのサイトにアクセスするか、ウォレットをスキャン システムに接続して)。
Etherscan などの Web サイトをスキャンして権限を取り消すにはどうすればよいですか?
2.ウォレットを接続する
2.ウォレットを接続する
3. [ERC-20]、[ERC-721]、または [ERC-1155] タブをクリックして、引き出したいアドレスを見つけます。
4.「キャンセル」ボタンをクリックします。
アイスフィッシングを特定するにはどうすればよいですか?
ユーザーがアイス フィッシングの罠に陥っていることを示す最初の兆候は、ユーザーが使用している URL または DApp に注目することです。
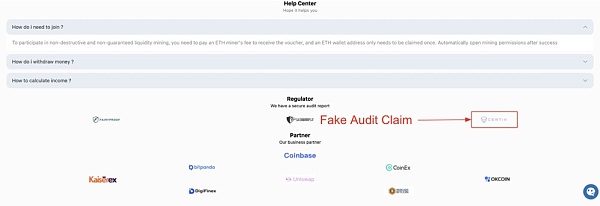
悪意のある Web サイトは、正規のプロジェクトからページをコピーするか、正規の組織のパートナーであるふりをします。
たとえば、CertiK とリンクしたり、偽の CertiK 監査レポートをアップロードしたりする詐欺的な Web サイトがよく見られます。
画像の説明
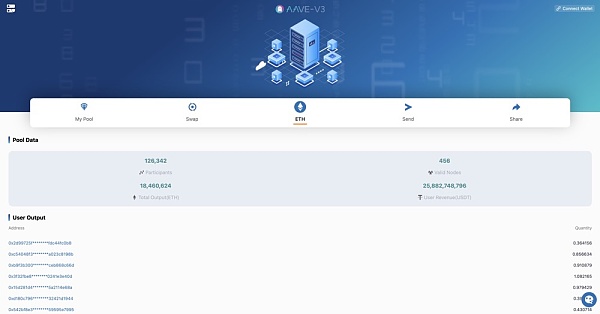
出典: CertiK調査チーム
画像の説明
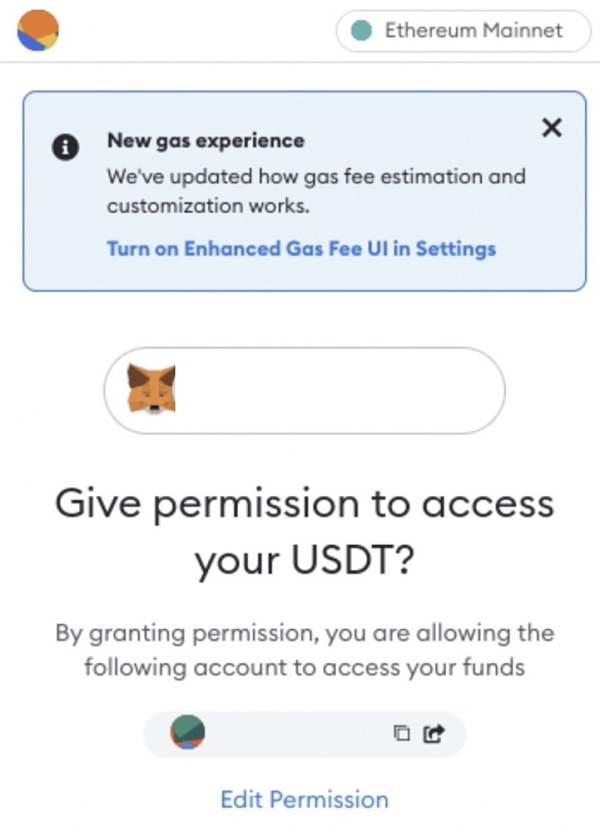
出典: メタマスク
画像の説明
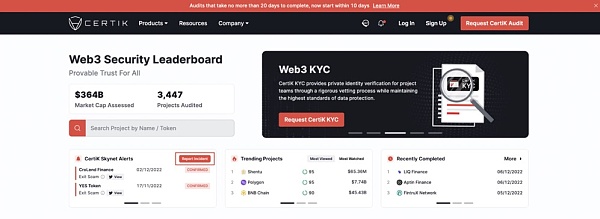
ユーザーは、certik.com で悪意のある契約のレポートを送信できます。
一部のオンチェーン チェックは、Web サイト (Etherscan など) をスキャンして、DApp または URL に表示されるアドレスに不審なアクティビティがないかどうかを確認するなど、ユーザーが独自の DYOR (Do Your Own Research) を通じて実行できます。
画像の説明
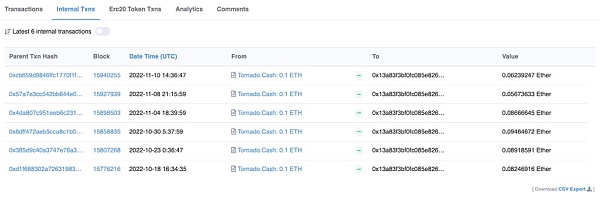
出典: イーサスキャン
出典: ツイッター
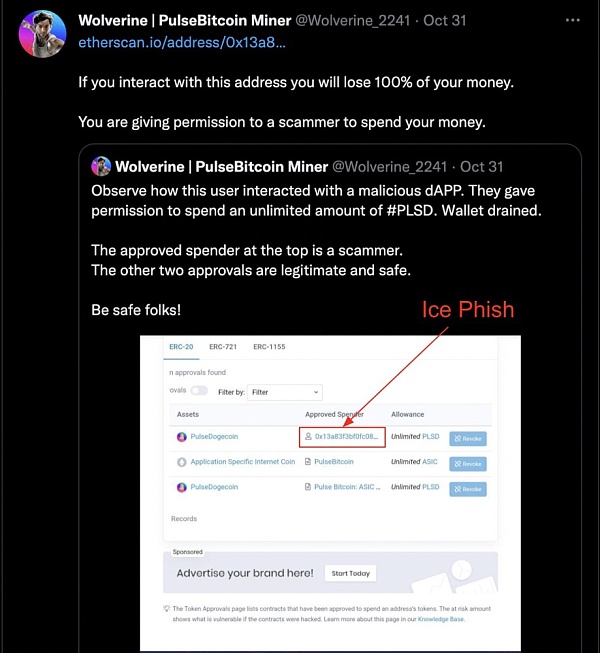
出典: ツイッター
被害者のウォレットの一部を調査し、ソーシャル メディアに苦情を投稿したところ、Ice フィッシング ウォレットに関連している可能性が高い偽の Maximus DAO ツイッター ページを発見しました。
自分自身を守るにはどうすればよいでしょうか?
アイス フィッシングの被害に遭わないようにする最も簡単な方法は、Coinmarketcap.com、coinecko.com、certik.com などの信頼できる Web サイトにアクセスして情報の信頼性を確認することです。
アイス フィッシング詐欺の多くは Twitter などのソーシャル メディアで見つかり、詐欺的なプロジェクトが正規のプロジェクトを装い、エアドロップなどの偽のイベントを宣伝します。
画像の説明
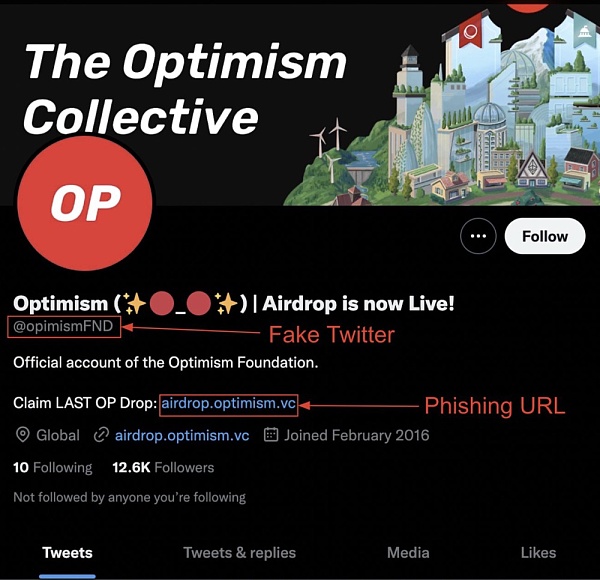
ソース: @CertiKAlert
最後に書きます
最後に書きます
フィッシング サイトは、Web 3.0 の世界で最もよく見られるタイプの詐欺の 1 つであり、ユーザーは機密情報をまったく提供しないため、罠にはまったことにさえ気づかないことがあります。
したがって、独自にオンチェーン チェックを行うことに加えて、インタラクションの URL が信頼できるソースによって検証されていることを再確認するために、より多くの時間を費やす必要があります。費やした時間はいつか報われます。



