หาก Ethereum แยก NFT จะ "แยก" ด้วยหรือไม่
กระบวนการแปลง Ethereum PoS เป็น PoW จะได้รับความสนใจจากนักขุดและวันที่ควบรวมกิจการก็ใกล้เข้ามาแล้ว และชุมชนมีหัวข้อเกี่ยวกับ Fork มากมาย หัวข้อหนึ่งที่ดึงดูดความสนใจของ Odaily นั่นคือ: Ethereum Forks อาจนำไปสู่ การโจมตีด้วยการบุกรุกอย่างหนักทำให้ผู้ใช้เสี่ยงต่อการสูญเสีย NFT
ทวีตเตอร์ในภาพด้านบนเตือนว่าหากผู้ใช้ไม่ทำอะไรเลย NFT ของเขาอาจหายไปเนื่องจากการโจมตีซ้ำ ในเรื่องนี้ยังมีเสียงที่แตกต่างกันด้านล่างพื้นที่แสดงความคิดเห็น เช่น ผู้ใช้ไม่ทำอะไรเลย แต่สามารถปกป้องทรัพย์สินของตนเองได้
ชื่อเรื่องรอง
Reentrancy Attacks และ EIP-155
เรามาทบทวนความรู้สองประเด็นกันก่อน หนึ่งคือการโจมตีซ้ำ และอีกข้อคือ EIP-155
ใน blockchain การโจมตี re-entry หมายถึงข้อเท็จจริงที่ว่าระหว่างการ hard fork ของเครือข่าย ธุรกรรมที่ลงนามโดยผู้ใช้ใน chain เดิมสามารถคัดลอกได้ด้วยตัวเองหรือผู้อื่นโดยไม่ได้รับอนุญาตจาก forked chain อื่น ๆ เพื่อรับสินทรัพย์เพิ่มเติม
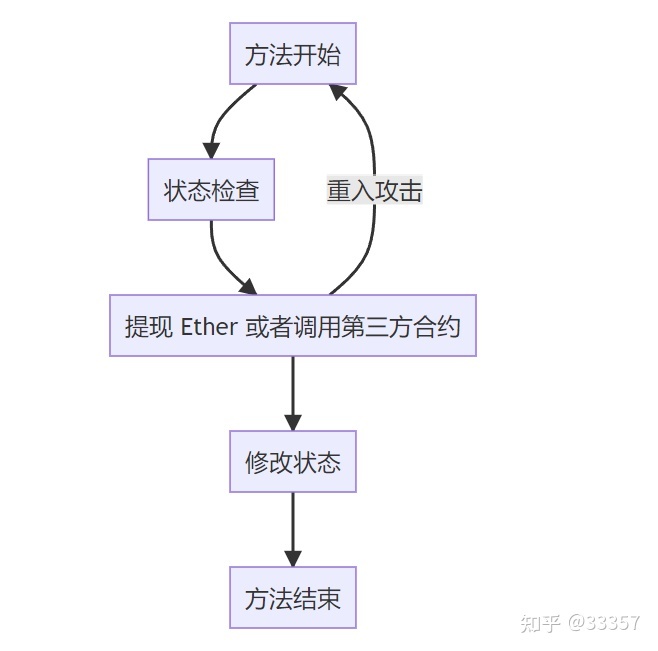
ตัวอย่างเช่น Xiao Ming มี CryptoPunk หลายตัวในเครือข่าย PoW หนึ่งๆ หลังจากที่โซ่ PoW แยกออกเป็นห่วงโซ่ PoS แล้ว Xiao Ming จะมีจำนวน CryptoPunks เท่ากันในเครือข่ายทั้งสอง ในเวลานี้ Xiao Ming ได้ลงนามในธุรกรรมการขาย CryptoPunks หลายรายการบนเชน PoW ตามทฤษฎีแล้ว ธุรกรรมนี้สามารถคัดลอกอีกครั้งบนเชน B โดยไม่ได้รับอนุญาตจาก Xiao Ming หาก Xiao Ming คัดลอกธุรกรรมนี้ด้วยตัวเอง Xiao Ming จะได้รับกำไรพิเศษจากการขาย NFT (ยังโกงผู้ซื้อด้วยการปลอมแปลง "การออกเพิ่มเติม") หากธุรกรรมนี้ถูกคัดลอกโดยผู้อื่น Xiao Ming จะสูญเสียทรัพย์สินโดยเปล่าประโยชน์บน ห่วงโซ่ PoS
ชื่อเรื่องรอง
ใครจะปกป้องผู้ใช้? ผู้ใช้จะป้องกันตนเองได้อย่างไร?
หลังจากเข้าใจหลักการโจมตีกลับเข้าใหม่และ EIP-155 เราได้อธิบายอย่างชัดเจนว่าเราควรทำอย่างไรหากเกิดการแยกหลังจากการควบรวมกิจการของ Ethereum
ก่อนอื่นเราต้องรวบรวมข้อมูล Ethereum fork chain เป็นไปตามโปรโตคอล EIP-155 หรือไม่
หากห่วงโซ่ที่แยกออกเป็นไปตามโปรโตคอล EIP-155 (ขึ้นอยู่กับการเปลี่ยนแปลงรหัสที่ทำโดยผู้นำที่แยก) ก็จะไม่สามารถคัดลอกธุรกรรมของผู้ใช้บนบล็อกเชนที่แตกต่างกันได้ผู้ใช้ไม่ต้องทำอะไร。
หากห่วงโซ่ที่แยกไม่เป็นไปตามโปรโตคอล EIP-155 (ไม่เฉพาะเจาะจงเกินไป) การโจมตีกลับเข้ามาใหม่ก็เป็นไปได้ และธุรกรรมใดๆ ที่ลงนามโดยผู้ใช้อาจถูกคัดลอกไปยังห่วงโซ่ที่แยกอื่นๆ ถ้าคุณหวังว่าจะได้รับประโยชน์สูงสุด ทุกครั้งที่คุณทำธุรกรรม ให้คัดลอกบนเชนอื่น (ควรผ่านสัญญาอัตโนมัติ) หากคุณเลือกที่จะยอมรับ Ethereum (ของแท้) อย่าเซ็นธุรกรรมใด ๆ บนเชนที่ถูกแยก



