Jump Crypto:深入分析区块链基础设施细分赛道
原文作者:Rahul Maganti/Jump Crypto合伙人,Rahul Maganti/Jump Crypto副总裁
原文标题:《Peeking Under the Hood: Key Pillars of Crypto Infrastructure》
原文编译:泽祎,麟奇,链捕手
相关阅读
简介
随着跨链桥、新框架和其他核心加密协议的迅速出现,有效地规划区块链基础设施仍然是用户、开发人员和投资者的关键挑战。“区块链基础设施”一词可以涵盖各种不同的产品和服务,从底层网络堆栈到共识模型或虚拟机。我们保留对构成 L1/L2 链的各种“核心”组件进行更深入的分析,以供以后发布(敬请关注!)。在这篇文章中,我们的具体目标是:
提供区块链基础设施关键组件的广泛概述。
将这些组件分解成清晰、易消化的子部分。
基础设施地图
我们将围绕区块链基础设施的生态系统定义为旨在支持以下关键领域的 L1 和 L2 开发的协议:
0层基础设施:(1) 去中心化云服务(存储、计算、索引);(2) 节点基础设施(RPC、质押 / 验证器)
中间件:(1) 数据可用性;(2) 通信/消息传输协议
区块链开发:(1) 安全和测试;(2) 开发者工具(开箱即用工具、前端/后端库、语言/IDE)。
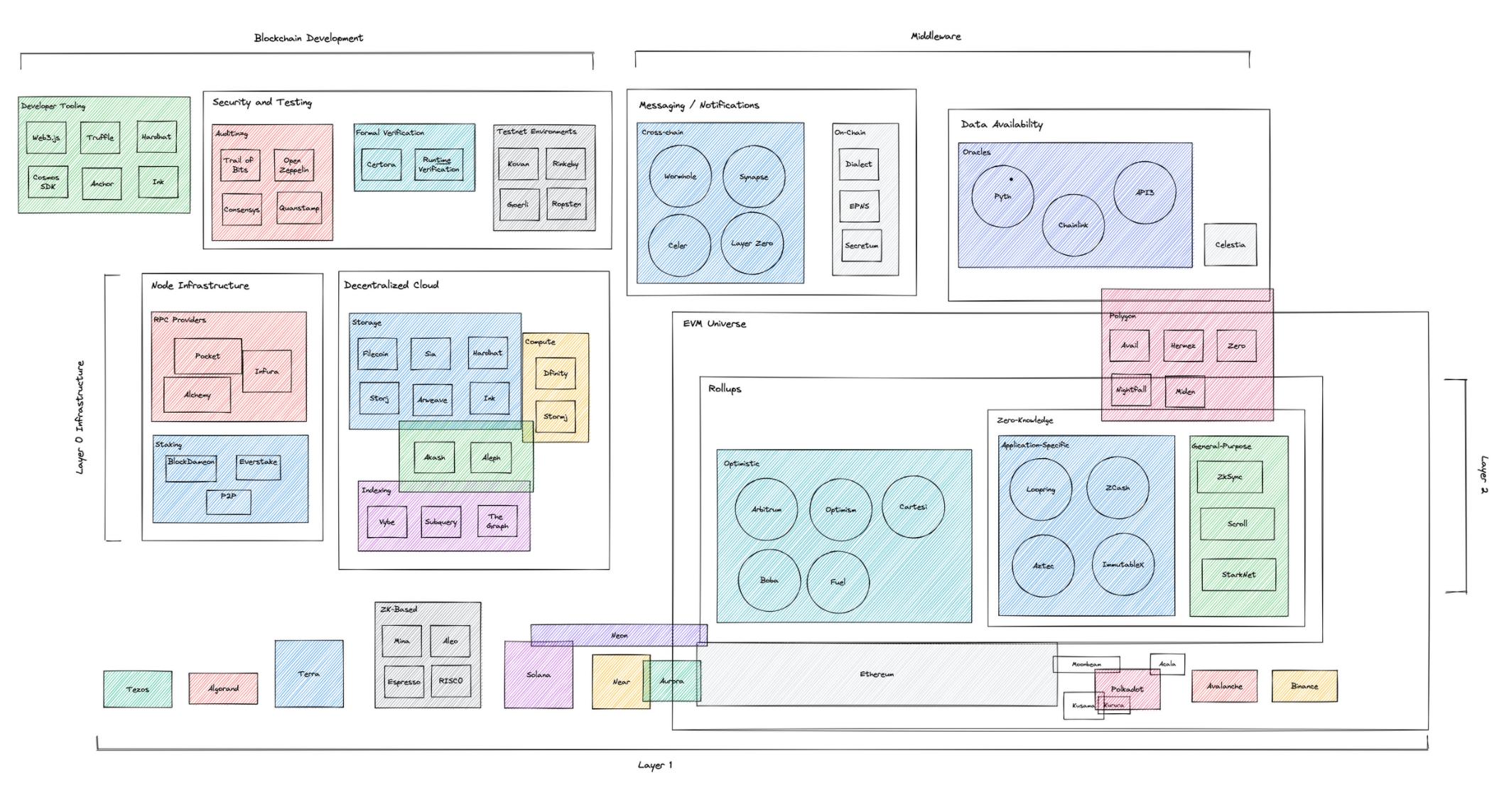
第0层基础设施
去中心化云服务
云服务对Web2的发展至关重要——随着应用程序的计算和数据需求的增长,专门以经济高效的方式快速提供这些数据和计算的服务提供商至关重要。Web3应用程序对数据和计算有类似的需求,但希望忠于区块链的精神。因此,旨在创建这些Web2服务的去中心化版本的协议已经出现了。去中心化的云有3个核心部分:
存储- 数据/文件被存储在由许多实体运行的服务器上。由于数据在多台机器上被复制或条带化,这些网络能够实现高度的容错。
计算--就像存储一样,计算在Web2范式中是集中的。去中心化计算关注的是将这种计算分布在许多节点上,以实现更高的容错性(如果一个或一组节点发生故障,网络仍然可以为请求提供服务,对性能的干扰最小)。
索引--在Web2世界中,数据已经存储在一个实体拥有和运营的一台或一组服务器上,查询这些数据相对容易。由于区块链节点是分布式的,数据可能是孤立的,分散在不同的区域,而且往往在不兼容的标准下。索引协议聚集了这些数据,并提供了一个易于使用和标准化的API来访问这些数据。
有几个项目提供了存储、计算和索引(Aleph和Akash网络),而其他项目则更加专业(例如,The Graph用于索引,Arweave / Filecoin用于存储)。
节点基础设施
远程过程调用(RPC)是许多类型软件系统功能的核心。它们允许一个程序调用或访问另一台计算机上的程序。这对于区块链尤其有用,区块链必须为来自不同区域和环境中运行的各种机器的大量传入请求提供服务。Alchemy、Syndica和Infura等协议将这种基础设施作为服务提供,使建设者能够专注于高级应用程序开发,而不是将呼叫传输和路由到节点所涉及的底层机制。
与许多RPC提供商一样,Alchemy拥有并运营所有节点。对于加密社区的许多人来说,集中化RPC的危险是显而易见的——它引入了单点故障,可能会危及区块链的活跃性(即,如果Alchemy失败,应用程序将无法检索或访问区块链上的数据)。最近,像Pocket这样的去中心化RPC协议出现了增长,以解决这些问题,但这种方法的有效性仍有待大规模测试。
质押/验证器——区块链的安全性依赖于一组分布式节点来验证链上的交易,但必须有人实际运行参与共识的节点。在许多情况下,运行节点所需的时间、成本和能源都令人望而却步,导致许多节点选择退出,转而依赖其他节点来承担确保链安全的责任。
然而,这种态度带来了严重的问题——如果每个人都决定将安全性转移给其他人,就不会有人验证。P2P和Blockdaemon等服务运行基础设施,允许不太成熟或资本不充足的用户参与共识,通常是通过集中资本。一些人认为,这些质押提供商引入了不必要的集中度,但替代方案可能更糟——在没有此类提供商的情况下,对于普通网络参与者来说,运行节点的进入壁垒太高,可能会导致更高的集中度。
中间件
数据可用性
应用程序大量消耗数据。在Web2范例中,这些数据通常以集中的方式直接来自用户或第三方提供商(数据提供商因将数据聚合并销售给特定的公司和应用程序而直接获得报酬——比如亚马逊、谷歌或其他机器学习数据提供商)。
DApp也是数据的大量消费者,但需要验证器使这些数据可供链上运行的用户或应用程序使用。为了尽量减少信任假设,以去中心化的方式提供这些数据非常重要。应用程序可以通过两种主要方式快速高效地访问高保真数据:
Pyth和Chainlink等数据预言器提供了对数据流的访问,从而允许加密网络以可靠和去中心化的方式与传统系统以及其他外部信息进行接入。这包括高质量的财务数据(即资产价格)。这项服务对于将DeFi扩展到交易、借贷、体育博彩、保险和许多其他领域的广泛用例至关重要。
数据可用性层是专门对事务进行排序并使数据可供其支持的链使用的链。通常,通过使用区块的一小部分,他们会生成证据,为客户提供所有区块数据已在链上发布的高概率确认。数据可用性证明是保证Rollup序列器可靠性和降低Rollup事务处理成本的关键。Celestia就是这一层的很好的例子。
通信和消息传递
随着Layer1及其生态系统数量的增长,对跨链管理可组合性和互操作性的需求更加迫切。跨链桥使原本孤立的生态系统能够以有意义的方式相互作用,这类似于新的贸易路线帮助连接原本不同的地区,开创了知识共享的新时代!Wormhole、Layer Zero与其他跨链桥解决方案支持通用消息传递,允许所有类型的数据和信息(包括逮捕)跨多个生态系统移动,应用程序甚至可以跨链进行任意函数调用,使它们能够进入其他社区,而不必部署到其他地方。Synpase、CELER等其它协议仅限于资产或代币的跨链转移。
链上消息传递仍然是区块链基础设施的关键组件。随着DApp开发和零售需求的增长,协议以有意义但去中心化的方式与其用户交互的能力将成为增长的关键驱动力。以下是链上消息传递可能有用的几个潜在领域:
代币领取通知。
允许在钱包中内置通信消息传递。
关于协议重要更新的通知。
跟踪关键问题的通知(例如,DeFi应用程序的风险指标、安全漏洞)。
一些值得注意的开发链上通信协议的项目包括Dialect、以太推送通知服务(EPNS)和XMTP。
区块链开发
安全与测试
加密技术的安全性和测试相对来说还处于初级不发达阶段,但不可否认的是,它对整个生态系统的成功至关重要。加密应用程序对安全风险尤其敏感,因为它们通常直接关系着用户资产。其设计或实施中的小错误往往会造成严重的经济后果。
有7种主要的安全和测试方法:
单元测试是大多数软件系统测试套件的核心部分。开发人员编写测试来检查程序中小的原子部分的行为。有各种各样实用的单元测试框架。例如以太坊上的Waffle和Truffle,Solana的标准是Anchor测试框架。
集成测试将各种软件模块作为一个组进行测试。因为库和高级驱动通常会以各种方式相互交互,以及其他低级模块之间的交互(例如,一个typescript库与一组底层智能合约交互)。测试这些模块之间的数据和信息流是至关重要的。
审计已成为区块链安全流程开发的核心部分。在向公众发布智能合约之前,协议通常会利用第三方代码审计员来检查和验证每一行代码。我们非常重视审核员来确保最高程度的安全。Trail of Bits、Open Zeppelin和Quantstamp是区块链审计领域中值得信赖的几个机构。
形式化验证涉及检查程序或软件组件是否满足一组属性。通常,有人会编写一份正式的规范,详细指出程序的行为方式。形式化验证框架将把这个规范转化为一组约束,然后对其进行解决和检查。来增强智能合约安全性的领先项目之一。Certora是一个领先的项目,它使用Runtime Verification来实施形式化验证以支持智能合约的安全性。
模拟—长期以来,定量交易公司一直使用基于代理的模拟来对算法交易策略进行回测。鉴于在区块链中进行实验的高成本,模拟方法提供了一种参数化协议和测试各种假设的方式。其中,Chaos Labs和Guantlet是两个利用基于场景的模拟,来保护区块链和协议的优质平台。
漏洞赏金有助于利用加密领域的去中心化精神来解决大规模的安全挑战。高额奖金激励社区成员和黑客报告和解决关键漏洞问题。因此,赏金计划在将“灰帽子”变成“白帽子”方面发挥了独特的作用。例如Wormhole创建的赏金平台Immunefi提供了价值高达1000万美元的漏洞赏金!我们鼓励任何人参与其中!
测试网络提供类似主网网络的展现形式,支持开发人员在研发环境中对其测试和调试参数。许多测试网络使用Proof-of-Authority/其他共识机制和少量验证者进行速度优化,并且测试网络上的代币没有实际价值。因此,除了通过水龙头外,用户没有其他方式获取代币。有许多测试网是为了模仿主网L1上的一些项目而构建的(如以太坊的Rinkeby、Kovan、Ropsten)。
每种方法都有自己的优点和缺点,当然也不是相互排斥的,不同的测试风格通常用于项目开发的不同阶段:
第 1 阶段:在构建合约时编写单元测试。
第 2 阶段:一旦构建了更高级别的程序抽象,集成测试对于测试模块之间的交互就会非常重要。
第 3 阶段:代码审计在测试网/主网发布或大型功能发布时进行。
第 4 阶段:形式化验证通常与代码审计相结合,并使用额外的安全保证。一旦程序被指定,其余的过程就可以自动化,这使得它很容易与Continuous Integration或Continuous Deployment工具配对。
第 5 阶段:在测试网络上启动应用程序检查吞吐量、流量和其他扩展参数。
第 6 阶段:部署到主网后启动漏洞赏金计划,利用社区资源来查找和修复问题。
开发人员工具
任何技术或生态系统的增长都有赖于其开发者的成功—在加密领域尤其如此。我们将开发人员工具分为四个主要类别:
开箱即用工具
用于开发新L1的SDK,有助于抽象出创建和部署共识模型的过程。预建模块允许灵活性和定制化,但针对开发速度和标准化进行了优化。Cosmos SDK就是一个很好的例子,它支持在Cosmos生态系统内快速开发新的经验证的区块链。Binance Chain和Terra是以Cosmos为基础的公链的著名例子。
智能合约开发—-有许多工具可以帮助开发人员快速开发智能合约。例如,Truffle boxes包含简单而有用的Solidity合约(投票等)示例。社区还可以向此存储库推荐附录。
前端/后端工具—有许多工具可以简化应用程序的开发。将应用程序连接到链(即,ethers.js、web3.js等)。
升级和与合约互动(例如OpenZeppelin SDK)—有各种不同的工具特定于生态系统(例如Solana智能合约的Anchor IDL,Parity智能合约的Ink),它们处理编写RPC请求处理程序、发出IDL、从ID生成客户端。
语言和IDE—区块链的编程模型通常与传统软件系统的编程模型有很大不同。用于区块链开发的编程语言就是为这一模型提供便利的。对于EVM兼容链,Solidity和Vyper被大量使用。其他语言如Rust被大量用于Solana和Terra这样的公链。
结论
区块链基础设施可能是一个过载和令人困惑的术语,它通常是一系列产品和服务的同义词,涵盖从智能合约审计到跨链桥的一切。因此,关于加密基础设施的讨论要么过于广泛和杂乱无章,要么对于普通读者来说过于具体和有针对性。我们希望这篇文章为那些刚刚进入加密行业的人和那些寻求更深入概述的人找到了合适的平衡。
当然,加密行业正在快速变化,本文中引用的协议很可能在2个月甚至3个月后不再构成生态系统的代表性样本。即便如此,我们认为本文的主要目标(即将基础设施分解为更容易理解和理解的部分)在未来将具有更大的相关性。但随着区块链基础设施格局的演变,我们也将确保提供明确一致的更新我们的想法。



